Historically, Macs have been for personal use. For the creatives.
But today? Not so much.
While Windows machines still dominate, Macs and other Apple devices are steadily gaining steam, particularly in startups and enterprise technology companies. Although employees may be stoked, the switch to Macs can be a major pain for IT — especially those with many years of Windows management under their belts.
The good news is that new software platforms are making Mac user and system management much easier, uniting Mac, Windows, and Linux device and user management into a single, centralized platform.
But before discussing the benefits of all-in-one management, let’s review a brief history of Microsoft and Apple ecosystems and why Macs have a reputation for being tough to manage. Then, we’ll explore how to overcome those challenges as Apple continues to shape the work hardware and OS future.
The Success of Microsoft’s Management Tools for Windows-Based Ecosystems
Microsoft Windows has been around for years. In that time, IT admins grew accustomed to the tools built to manage Windows systems and users — for good reason. Microsoft poured significant time and money into creating an ecosystem of management tools that could provide centralized control and security, like SMS (now called SCCM) and later Active Directory (AD).
Strategically, Microsoft released these tools at the height of Windows popularity, making it a no-brainer for companies to establish SMS and AD as their default system management. Over time, Microsoft continued perfecting SMS and AD, which increased their adoption across enterprise companies — if an IT manager used SMS or AD at their previous job, they were likely to recommend it at their next. And the Microsoft management tool flywheel kept on spinning.
Challenges Posed by Macs in Enterprise Environments
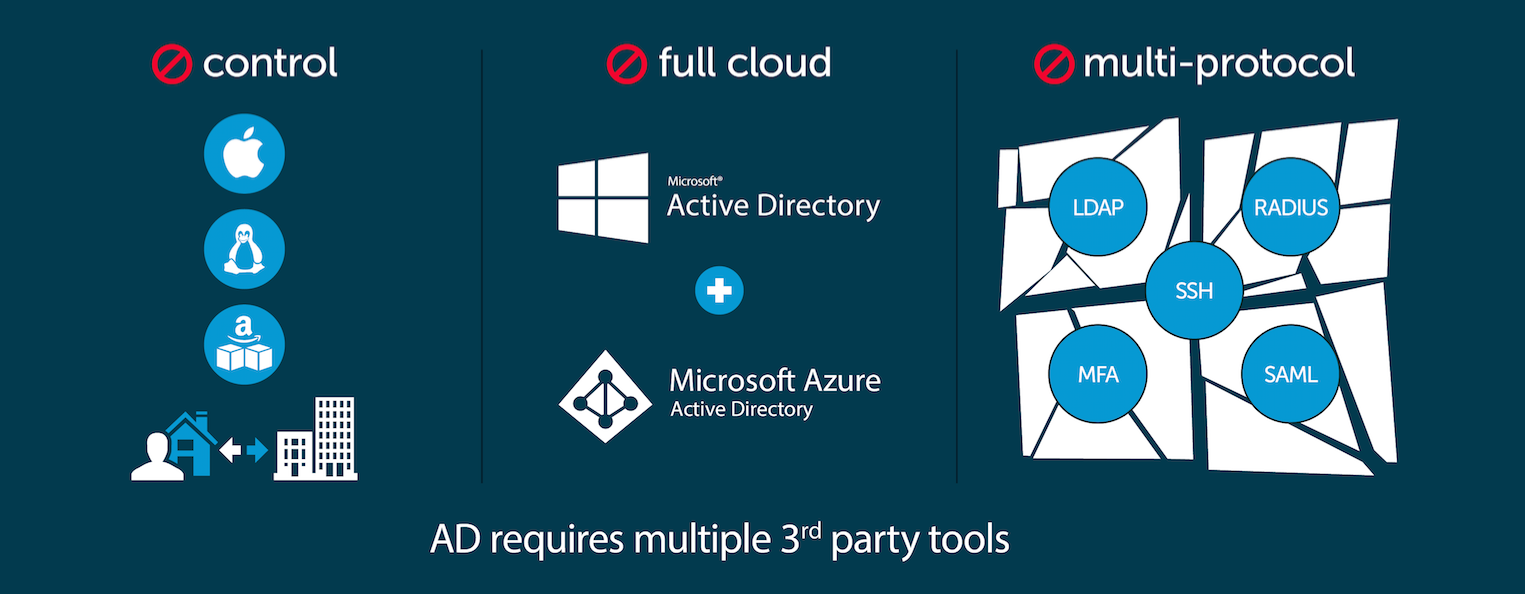
As you might expect, existing IT management tools like Active Directory and SCCM don’t play well with Macs. And that has left IT teams with three options:
- Try to make it all work with in-house tools.
- Buy multiple tools for multiple systems and multiple types of users.
- Find a way to house and manage them all under one roof.
Forward-thinking IT organizations are choosing the third option. Trying to keep track of systems and users in disparate systems isn’t only a waste of time; it’s also an opportunity for things to fall through the cracks, opening the door to internal and external threats.
Organizations overseeing multiple operating systems and users need a platform that can mimic Microsoft’s Group Policy Objects (GPOs), virtual collections of policy settings, across Mac, Windows, and Linux devices and users straight from the cloud. More on those solutions later.
Mac Management Best Practices
Secure Mac management is key to upholding security policies in fully remote, hybrid, or bring your own device (BYOD) workplaces. Here are some ways to integrate Mac management best practices into traditional system management.
Implement a Centralized Directory Service
As we’ve hinted, a centralized directory service is critical for end-to-end user and device management. A unified, fully integrated system makes it much easier to configure the correct permissions, deploy the right apps, and maintain software updates across all users and operating systems (including Macs). Centralized platforms also make it easier to spot and stop potential security threats or performance issues impacting employee productivity.
Enable Single Sign-On (SSO) for Mac Users
Single sign-on, or SSO, expedites the login process for users and eliminates the risks of password reuse. In Macs, IT should implement SSO using Apple’s configuration profiles. These can be manually installed or managed via a mobile device management (MDM) platform. During the configuration process, IT can offer SSO for all apps or restrict SSO by app identifier and/or service URL.
Embrace Mobile Device Management (MDM) Solutions for Macs
Every user needs different apps to do their jobs. The scope of those jobs can change throughout employees’ time at the company, meaning their permissions and app access have to change along with it. This has become even more challenging as most offices have transitioned to a remote IT team. Enter mobile device management.
With MDM, IT can install apps, maintain device trust certificates, grant printer access, configure Wi-Fi settings, and more on employee smartphones, tablets, and laptops — from anywhere. They can also standardize user profiles and deploy changes to those profiles globally, and they can use MDM commands to lock, shut down, or erase any compromised devices near-instantly. Overall, following MDM best practices can enhance company security, uphold compliance requirements, and maintain network access control.
Apply Patch Management for Mac Systems
Patching greatly enhances the security of macOS environments. Keeping up with patches involves compiling a list of missing patches on user devices, downloading them, testing them on non-employee machines, and rolling them out to the entire Mac workforce. Without a robust patch management process in place, you leave your company open to cyberattacks or insider attacks that compromise your company’s data and reputation.
Enforce Security Policies and User Access Controls for Macs
While Mac management is about creating a seamless employee technology experience, it’s also largely about lowering a company’s risk of compliance breaches, data breaches, and cyberattacks. Using MDM, IT can activate Apple’s native macOS security capabilities and enforce strict security policies on all Apple devices, from standardizing user account permissions to mandating Mac password best practices to preventing unauthorized app downloads.
Regularly Update and Upgrade Mac Software
Apple’s software updates not only improve security, they also improve the user experience. Macs that haven’t been updated in a while can be slow, incompatible with certain apps, or be missing certain features. Keeping up with macOS updates keeps end users productive and mitigates issues (and helpdesk tickets) that could come from working on an outdated OS.
Implement Remote Management and Support for Macs
Remote and hybrid workplaces are becoming increasingly common. That means IT needs a way to access, set up, assess, and fix Macs remotely. Thankfully, a handful of remote assist platforms support macOS, giving IT insight into user problems irrespective of employee location.
Provide Training and Support for Mac Users
Mac operating systems have a significantly different layout and shortcuts than Windows, which can be hard for new Mac users to get used to. Providing educational materials with screenshots and videos, hosting training sessions, and notifying users of upcoming software updates or changes to their Macs can accelerate adoption and decrease the number of low-priority helpdesk tickets IT has to work through.
Monitor and Report on Mac System Health and Performance
Closely monitoring Mac fleets empowers IT teams to proactively address performance or compliance concerns. Centralized systems can also put these problems into context. Perhaps there is a global issue across Macs, Windows, and Linux machines or something affecting a company’s entire user base. Setting up automatic, configurable alerts ensures IT staff can come to a resolution quickly, minimizing the chances of work interruptions.
Leverage Automation and Scripting for Mac Management
Just like any other OS, there are many repetitive tasks when configuring and maintaining Macs. Apple has its own scripting language that IT teams can use to automate time-consuming tasks related to apps, processes, and the operating system as a whole.
With AppleScript and any other native automation functionality in your user and system management tool, IT can reduce errors, reduce downtime, and speed up employee onboarding times — ultimately saving companies time and money.
Check out this series on 5 helpful commands every Mac admin should know.The Advantages of Using a Cloud-Based Solution like JumpCloud
While Mac management can be complex, it doesn’t have to be.
A new generation of Mac management solutions is enabling admins to enforce best practices and streamline their workflows. The best among them? The JumpCloud Directory Platform. JumpCloud is a cloud-based user and system management platform specifically designed to manage Mac, Windows, and Linux machines (and their users) simultaneously.
Built specifically to centralize IT management, JumpCloud allows admins to securely manage access to Macs, activate SSO, require multi-factor authentication (MFA), enable screen saver locks, disable guest accounts, and much more — from wherever they work.
JumpCloud also has native automation functionality that IT can use to set up onboarding workflows or deploy software updates or patches as they become available, saving time and ensuring employee workspaces stay secure.
End users benefit from JumpCloud, too. Easy Mac setups and zero-touch deployment get them up and running quickly. And JumpCloud’s built-in MDM features enable fast troubleshooting, decreasing disruptions and increasing productivity.
Simplify Mac Management with JumpCloud
In today’s hybrid world, remote Mac management is a must. But most device and user management providers are built only for Windows or only for Macs. And managing multiple systems leads to increased overhead costs, IT sprawl, and a larger attack surface for bad actors.
What sets JumpCloud apart is its open directory architecture, which connects users to their systems, applications, files, and networks regardless of operating system, machine, platform, provider, protocol, or location. JumpCloud’s all-in-one platform can handle all of your security, analytics, MDM, patch management, and virtual support needs, while still providing you the flexibility to work with the IT tools you prefer.
Perhaps even more importantly, JumpCloud’s automation features drastically decrease the time your IT team spends closing out helpdesk tickets, giving them the space they need to work on your company’s most pressing issues.
So, what are you waiting for? Get started with a free trial today or schedule a demo with our sales team.






