Active Directory (AD) was introduced two decades ago to provide centralized user and rights management as well as Windows PC configurations for private networks behind firewalls. Email was the first factor to upend that model for access control, and was followed by the proliferation of cloud services and devices that transformed networks into a digital estate.
The perimeter model that AD supported worked well, until it didn’t. Its shortcomings helped lay the groundwork for the Zero Trust approach to identity and access management (IAM). Zero Trust brings access control (the perimeter) closer to identities and devices by enforcing explicit trust before granting access to resources.
JumpCloud’s open directory platform makes it possible to modernize AD for Zero Trust. It works by combining cloud IAM with universal endpoint management (UEM) and other essential services to manage today’s IT infrastructures, which are a hybrid of everything, everywhere. JumpCloud’s Active Directory Integration (ADI) feature integrates AD with the open directory.
ADI makes it possible to extend multi-domain environments to the cloud without locking small to medium-sized enterprises (SMEs) into a suite of vertically integrated tools. That approach to AD modernization can limit freedom of choice and distract from your overall mission with significantly higher IT management overhead. This article provides an overview of what ADI is and how it works to help SMEs reestablish the strong access control that was lost when AD’s network perimeter model couldn’t support modern IT infrastructure requirements.
Note: JumpCloud helps you follow Microsoft’s Zero Trust Rapid Modernization Plan (RaMP) for a privileged access strategy to secure AD.
AD Integration Deployment Models

ADI continuously syncs users, groups, and passwords between AD and JumpCloud. Its components are installed on a member server and configured to import and sync identities for each domain. It provides several options for authentication flows: bi-directional syncing and one-way syncing (in either direction). Pass-through authentication back to AD is supported to uphold security and compliance requirements for local authentication and authorization.
Note: Microsoft’s Entra ID cloud directory will not synchronize groups unless the subscription is a Premium SKU.
Bi-Directional Synchronization
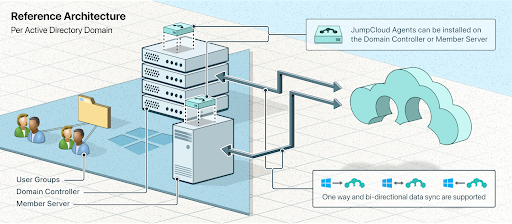
Bi-directionality means that password changes that occur on the integrated platform get synchronized and changed in AD. This makes it possible for friction-free user access with single-sign on (SSO). It also enables advanced identity lifecycle management. For example, you can use JumpCloud to sync human resources systems with JumpCloud and back to AD.
AD integrations are often one-way, where AD is the source of truth and a third-party application or IT resource authenticates user access against AD. Resources such as web applications require SSO in order to meet modern security and usability requirements. A cloud directory provides SSO with the added benefit of multi-factor authentication (MFA) and conditional access to enable a Zero Trust security strategy that “assumes breach” and verifies requests.
This approach modernizes AD to extend access control to every device and resource without requiring admins to perform consolidation, migration, or deep integrations with multiple point solutions. Admins can manage users, groups, and access in either AD or JumpCloud.
There’s also an available migration path to JumpCloud, if and when it makes sense to leave AD.
Note: Microsoft requires its customers that modernize AD using Entra ID to purchase premium subscriptions for password write-back.
Pass-Through Authentication
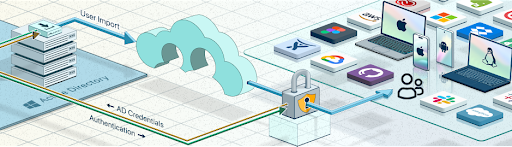
Some sectors are required to retain oversight of their credential store for certainty and compliance. JumpCloud’s open directory can federate authentication AD through ADI, which extends AD to other resources and devices without running afoul of those rules.
Note: Outbound authentication flows from AD to JumpCloud enable AD users to access cloud resources and non-Windows devices.
Modernizing AD with JumpCloud
JumpCloud is modern, user-friendly, and makes it possible for admins to manage SSO and UEM from a single console with minimal effort. It also extends SSO to common network protocols, adding convenience, while reducing the risk of unauthorized access to infrastructure. A Zero Trust IAM strategy complements your existing investment in network perimeter security.
A crucial part of reestablishing access control over your digital estate comes from the ability to integrate AD with non-Windows systems.
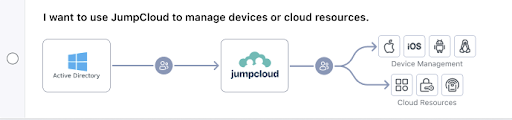
Universal Endpoint Management
JumpCloud’s UEM adds the ability to integrate Android, macOS, and Linux devices into Active Directory-controlled environments with mobile device management (MDM) support for Windows. Untrusted endpoints can become a weak link in a Zero Trust strategy; UEM ensures that there’s a baseline of policies and patch management (optional) to reduce your attack surface.
End users don’t have to jump through hoops to stay compliant with password policies, password resets, and other critical functions. And, they can do this from anywhere — with no VPN. Built-in remote assist is available to support your users with both attended and unattended sessions.
Agents provide telemetry and reporting on device and user activity.
SSO and Modern Authentication
ADI synced identities connect through SSO to networking infrastructure with RADIUS, cloud infrastructure and web apps with OIDC and SAML, file servers on-prem and in the cloud, legacy applications via LDAP, and more by using JumpCloud’s RESTful API.
JumpCloud offers an integrated password manager for when SSO isn’t possible.
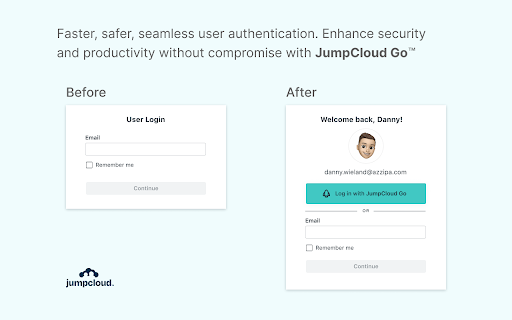
The platform also includes JumpCloud Go™, a hardware-protected and phishing-resistant passwordless login for JumpCloud managed devices. It provides modern authentication that’s more secure and simpler and safer for your users. JumpCloud Go is supported on MacOS and Windows and integrates with device biometric authenticators (Apple Touch ID or Windows Hello) to satisfy traditional password sign-in challenges. It will provide high MFA authenticator assurance.
Adopting SSO and UEM is recommended for all organizations that use AD, per Microsoft’s Cybersecurity Reference Architectures (MCRA). JumpCloud provides SMEs with an alternative to Microsoft’s prescribed path by keeping your identity provider (IdP) and IT stack independent. JumpCloud has essential IAM, UEM, and system management capabilities in a single place.
Try JumpCloud ADI
Still wondering what Active Directory Integration is and how it can modernize AD? See for yourself when you sign up for a free trial of JumpCloud. It’s included with the open directory platform at no additional charge. JumpCloud has professional service options to assist with onboarding users. JumpCloud is also a Google partner and integrates with Google Workspace, making both services better together with a modern IT management and productivity package.




