Assertions are one of the most powerful aspects of Security Assertion Markup Language (SAML 2.0). They make it possible for small and medium-sized enterprises (SME) to adopt single sign-on (SSO) that combines convenience with extremely granular user permissions for web applications. This capability is vital for organizations that operate within regulated industries with stringent data security requirements. This article provides an overview of what assertions are, how they function, how to debug them for your applications, as well as the specific statements contained within them.
What Is SAML Assertion?
SAML assertions are the messages that are exchanged between an identity provider (IdP) and service provider (SP) that confidentially identify who a user is, what pertinent information exists about them, and what they’re authorized or entitled to access. Those messages also specify security conditions (such as the source of the assertion) and assurances that assertions are valid. XML schemas are used to author assertions, providing a rich canvas to specify very specific conditions. They’re communicated following successful authentication of the SAML request. The SAML response is sent in lieu of a username and password being shared over the wire.
XML Documents
Assertions are recorded and transferred as XML documents to standardize communications between the IdP and SP. These documents are composed using a schema format for assertions and protocols.
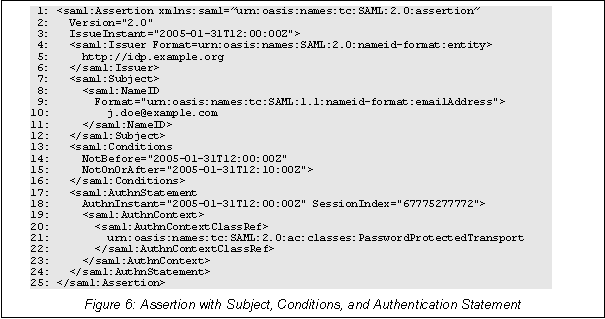
Attribution: OASIS
Writing assertions is a coding activity that will require quality assurance and testing. Organizations should maintain schemas throughout the lifecycle of their SSO system. It’s advisable to use pre-built connectors if your SME cannot support custom development.
What Is a SAML Assertion Validator?
Writing XML schemas can be a heavy lift for some organizations and may take time to debug. That’s why the SAML standard has a built-in facility to troubleshoot user login errors called an Assertion Validator. It will identify problems in assertions that are sent from your IdP. Some platforms will automatically capture assertions for debugging purposes. Assertion Validators expressly target issues with assertions and will not identify login issues. JumpCloud’s platform contains a library of several hundred pre-built SSO connectors so that users may bypass this process.
Types of SAML Assertion Statements
Statements are found within assertions and are broken down into specific functions. There are three types of statements, as specified by the SAML 2.0 open standard:
- Authentication statements
- Attribute statements
- Authorization Decision statements
Statements are encapsulated within SAML assertions, and provide significant flexibility for identity and access management (IAM) onboarding and governance. Let’s explore each of these in further detail.
Authentication Statement
These assertions are generated by the system that authenticates a user and contain information about how the authentication decision transpired and log information including timestamps.
Attribute Statement
SAML has the capacity to relay information about users such as what department they work within, whether they’re part of a “VIP” group that may access a restricted system, as well as basic contact information such as email addresses. Attributes can be created for custom applications and mapped back to predefined values.

Attribution: OASIS
Authorization Decision Statement
The decision statement provides additional details about what actions a user is entitled to perform such as accessing a particular webpage or a secure area of an application. For instance, it’s a very good idea to limit who can access private health information. Other authentication protocols, such as OpenID Connect (OIDC), do not have that capability.
Compare SAML to other internet protocols:
How Assertion Statements Are Used
Assertions contain one or more of these statements, depending on whether the configuration is for authentication or also includes authorization. There may also be user-defined statements. Statements allow systems to interoperate across domain boundaries and make it possible to securely establish SSO for websites, attribute-based user authentication, and to secure web services through the sharing of security information within Simple Object Access Protocol (SOAP) messages.
Try JumpCloud
JumpCloud simplifies the creation of SAML SSO connectors and is constantly adding to its library of connections. Give us a try to test out your SSO without any commitment or restriction.
Frequently Asked Questions
What is SAML in simple terms?
SAML (Security Assertion Markup Language) is an open standard that enables secure single sign-on (SSO) by allowing identity providers to communicate user authentication and authorization information to service providers.
What is the difference between SAML assertion and response?
A SAML assertion contains the actual authentication and authorization information about a user, while a SAML response is the overall result of an authentication request, which includes the assertions.
What is the difference between SAML and SSO?
SAML is a protocol used to achieve single sign-on (SSO), allowing users to authenticate with multiple web applications using a single set of credentials, whereas SSO is the overall user experience of accessing various services with one login.
What are the types of SAML assertions?
SAML assertions consist of three types: Authentication statements (confirming user identity), Attribute statements (providing user details), and Authorization Decision statements (specifying user permissions).
Can you provide an example of SAML authentication?
An example of SAML authentication is when a user logs into a corporate portal and is automatically granted access to various linked applications without needing to enter their credentials multiple times.




