Ransomware is a multi-billion dollar a year racket and attacks against small and medium-sized enterprises (SMEs) are on the rise, costing companies between $25,600 to $200,000 on average. The insurance industry is stepping in with cyber insurance policies tailored to help SMEs recover; but, as with any plan, there’s an underwriting process to avoid adverse selection. Insurance companies aren’t in business to just give money away and don’t want too many “sick” clients.
Insurers determine whether an SME is worth the risk by assessing where there are sufficient security controls and patching strategies in place. They’ve recently keyed in on several high-profile software vulnerabilities related to Microsoft Exchange Server, for example. Exchange’s presence, and the absence of critical security updates for it, are being used as criteria to refuse coverage.
The assessment of risk doesn’t begin or end with Exchange. A client asked me to help her fill out an application for cyber insurance that services the legal industry and questions ranged from the usage of technical controls such as multi-factor authentication (MFA) and email security to least privilege computing. However, several legacy products and solutions were also explicitly called out:
- Windows Server 2008
- Windows 7
- Remote Desktop Protocol
- Windows Patch Management within 30 days
Don’t just take our word for it … here it is, in black and white:
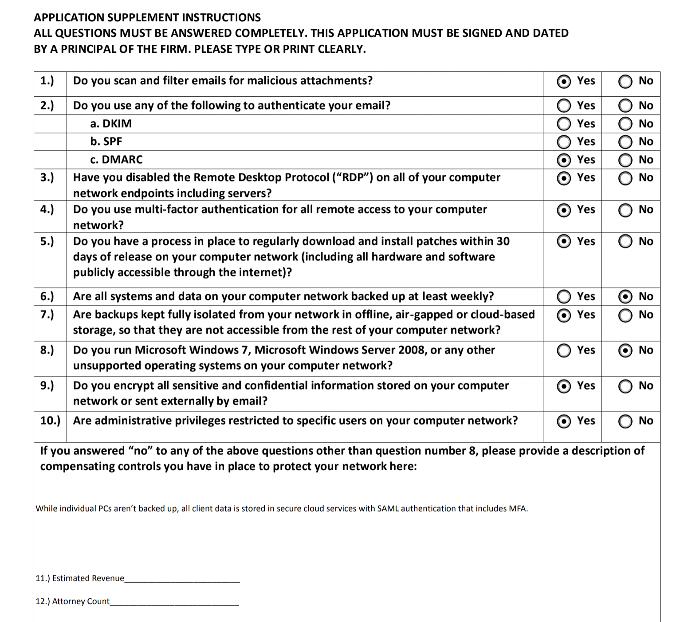
Many IT admins would publicly roll their eyes at the notion that any SME would be using unsupported software, but those of us who have been out in the field know what’s hidden underneath the covers. Why else would insurers be asking? If administrative overhead is inherent to operate legacy, on-premise infrastructure in any organization, and if doing the same old thing is a “pre-existing condition,” why not change? Simply put, many companies feel they don’t have the resources in their budget to update old server racks or to locate and hire qualified people to do this.
To that I say, it all boils down to this question: Is it worth the risk to maintain all of that legacy, or is it possible to think differently, accomplish more, and become a (insurer-friendly) security and compliance hero?
Risk Transference
Migrating to a cloud service is risk transference, and we’d argue it’s an effective way to reduce vulnerabilities that cyber insurers would approve of. You’re placing trust in a SaaS provider to have a mature secure development lifecycle (SDLC), a security operations center (SOC), and a team that has experience and technical certifications that an SME couldn’t afford to implement.
IT admins can use JumpCloud for their identity and access management (IAM) infrastructure, with confidence. JumpCloud has completed a SOC Type 2 examination for its directory platform and follows these security best practices. You can read more about why you should trust us here.
In all fairness, Microsoft has also invested heavily in security (I had the pleasure of working with some terrific people on its security team). However, as noted by Fortune, Microsoft can’t be both the firefighter and the arsonist. Its legacy on-premise products are a wellspring of security vulnerabilities and products that are beyond end-of-life are compromised and insecure.
That’s true even for server products that are within the support lifecycle. For instance, I had to decommission a domain controller (DC) that had been running Remote Desktop Protocol and was open to the web. That meant rebuilding the DC and deploying a dedicated server for RDP. There were several hidden costs to this endeavor, like ensuring that the server rack and our server virtualization suite (and staff who had to be certified to use it) were capable of handling those changes. Costs add up, quickly.
Today’s IT environments require a Zero Trust security posture and many industries are governed by regulations and compliance policies, or soon will be, that have specific requirements that must be met. This calls for systems that are up to the challenge, but manageable enough, so that SMEs don’t have to buy a fully loaded Porsche for a cruise down Main Street.
JumpCloud is designed to support the requirements of SMEs to manage the user lifecycle across all devices, regardless of the OS, and to connect to more things securely. Zero Trust IAM and compliance features such as patch management tools are exactly what cyber insurers are looking for.
Do More with Easy Zero Trust and Compliance
Specifically, JumpCloud enables Zero Trust through cloud directory policies, unified device management, conditional access, single sign-on (SSO) for all apps, and free multi-factor authentication (MFA). The user’s journey begins with a strong password on a device that’s managed by policies; and policies can become conditions that must be met before access is granted to IT resources. Conditions can include rules such as “is this device patched?”, and JumpCloud provides cross-OS patching and device management to support compliance with those rules. We’re continuing to expand upon those patching capabilities and provide for easier reporting.
Compliance is another consideration for insurers. The JumpCloud platform is audit-ready with a device panel highlights tab that consolidates all pertinent system, access, and device information into a single view. JumpCloud enables its users to treat compliance as a process, not a product. Easy compliance is part of the domainless enterprise, which empowers IT admins versus the on-premise software that creates the attack surface area that cyber insurance is, ironically, intended to safeguard against. It’s better to be prepared for the future than have to take corrective actions.
If managing legacy servers would risk your organization being denied access to cyber insurance, now is the time to seriously consider moving on to a more modern directory and IAM infrastructure.
Try JumpCloud
JumpCloud is a cloud directory with advanced IAM capabilities throughout its cloud platform, securely connecting you to more resources than on-premise solutions at a lower cost. It’s free to try for up to 10 users/devices with complimentary premium support over the initial 10 days.





