If your organization uses Microsoft Azure Active Directory (AD) and has an LDAP (lightweight directory access protocol) server or other LDAP-dependent resources, you’ve likely run into some issues connecting them. The culprit? Azure AD’s limited LDAP functionality: Azure AD does not support LDAP connectivity directly. While there are ways to connect to LDAP resources with Azure AD, they take a few extra steps (and sometimes, extra costs) and their configurations tend to be fairly complex.
This blog will cover the methods for supporting LDAP servers and resources with Azure AD. It will also discuss potential alternatives to incorporating your LDAP servers and resources into your architecture if the traditional route through Azure AD isn’t a good fit for your organization.
Does Azure AD Support LDAP?
Azure AD cannot support LDAP directly; it can only do so through a connector or sync. As Microsoft puts it, “Azure AD doesn’t support the Lightweight Directory Access Protocol (LDAP) protocol or Secure LDAP directly. However, it’s possible to enable Azure AD Domain Services (Azure AD DS) instance on your Azure AD tenant with properly configured network security groups through Azure Networking to achieve LDAP connectivity.”
Let’s explore this method of connecting Azure AD to LDAP resources with Azure AD Domain Services.
Method 1: Azure AD Domain Services
Azure AD Domain Services (AAD DS), Microsoft’s managed domain service, can facilitate LDAP authentication for resources within the AD domain. In this model, AAD DS acts as the link between the LDAP resource and Azure AD. It provides one-way synchronization from AD (through AD Connect and then Azure AD), which the LDAP resource can then authenticate against.
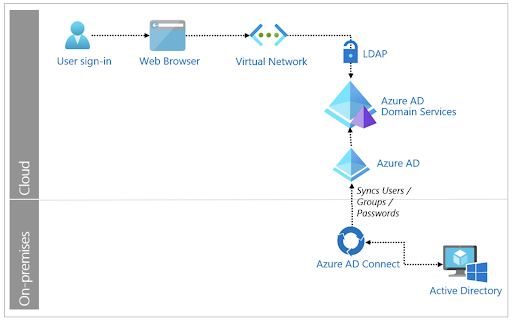
This model is not a direct method for connecting Azure AD with LDAP resources — it adds several steps to the authentication process. In general, every step or connection in an IT process is a potential point of failure; this multi-step process increases complexity and risk. Compared to a direct LDAP connection, this method is dependency-heavy and can prove brittle and limiting.
Additionally, Azure AD DS isn’t always a financially viable option. AAD DS is billed in addition to your AD or Azure subscription, charged either hourly or monthly. That can add up, especially for small and medium-sized enterprises (SMEs) on a limited budget. For SMEs using a standard subscription in the U.S., Azure AD DS would likely amount to over $1,000 per year.
Finally, note that this method only works for LDAP servers or resources within the AD domain.
There’s another method of connecting to LDAP resources with Azure AD that bypasses Domain Services, but it acts as a sync rather than supporting a direct LDAP connection. We’ll explore this method next.
Method 2: LDAP Synchronization
Microsoft’s directory synchronization feature can be extended to sync LDAP servers (view the full documentation here). In this method, the LDAP server syncs with AD Connect, which then follows a similar configuration to Method 1. This model works for on-premises LDAP resources outside of the AD domain.
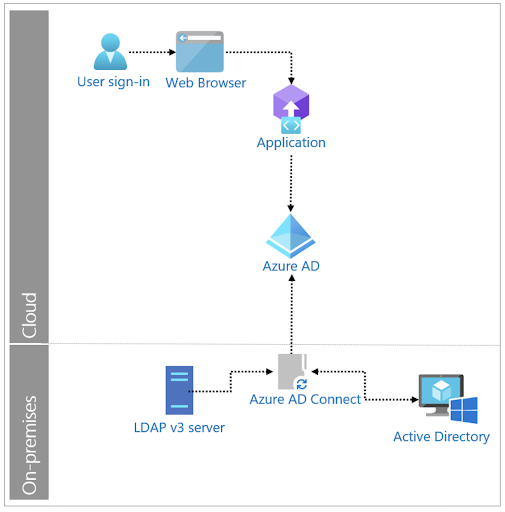
In this method, the LDAP server only communicates with Azure AD Connect, which synchronizes data from the LDAP server to AD and, in turn, to Azure AD. Similar to Method 1, this method requires integrations that are prone to breakage and must be handled with care and expertise. As Microsoft warns,
Deploying the LDAP Connector requires an advanced configuration and this connector is provided under limited support. Configuring this connector requires familiarity with Microsoft Identity Manager and the Specific LDAP directory.
Customers who require to deploy this configuration in a production environment are recommended to work with a partner such as Microsoft Consulting Services for help, guidance and support for this configuration.
Suffering From the Authentication Blues? Try These Alternatives.
Both methods detailed above add complexity to the LDAP authentication process, making them a less-than-perfect fit for many organizations. Method 1 requires an additional cost for Azure AD Domain Services, and Method 2 is self-proclaimed to be difficult to configure and manage. Not the easy answer you may have been looking for.
Fortunately, there are alternatives: you can implement your own LDAP system or leverage cloud-based LDAP. We’ll cover both below.
Implementing Your Own LDAP System
Implementing your own LDAP system is essentially creating your own LDAP directory, which you can achieve through several solutions, including the open source OpenLDAP. Implementing your own LDAP system provides significant flexibility to configure and manage it how you want. However, this typically comes with significant overhead. Organizations that decide to implement their own LDAP system are responsible for the hardware, software, installation, configuration, and ongoing maintenance. This includes:
- Ensuring high availability. LDAP systems are responsible for authentication, which makes their availability critical to maintaining uptime.
- Configuring and connecting resources to the LDAP server.
- Standing up, hosting, and updating servers. Don’t forget the costs associated with renting, securing, and temperature-controlling the space.
Alternatively, organizations that don’t want the burden of hosting their own LDAP instance can offload the bulk of its maintenance and management to a cloud-based LDAP solution.
Cloud-Based LDAP as a Solution
Some directory services offer LDAP-as-a-Service. With this SaaS-based approach to LDAP, organizations can leverage a cloud-hosted LDAP endpoint that enables on-prem or cloud-based applications to authenticate against it directly. IT admins don’t need to install, configure, manage, monitor, or maintain the infrastructure; the LDAP provider does all of the heavy lifting. And because the LDAP protocol itself is highly flexible, IT teams maintain a significant amount of freedom to configure it how they want.
Another benefit to cloud LDAP is that it provides a standardized schema, enabling quicker application integration. It includes standard documentation on how other LDAP applications can be integrated, and applications like Atlassian Jira, Jamf, Casper, MySQL, and OpenVPN have standard integration documentation of their own. These resources ensure IT admins aren’t left on their own without help.
In addition, hosted LDAP from a reputable provider helps ensure LDAP security. Rather than managing LDAP security yourself, LDAP-as-a-Service usually follows strict security standards. As a rule of thumb, look for LDAP providers that practice the following security measures:
- LDAPS (TCP port 636) and StartTLS encryption (TCP port 389).
- Password hashing.
- Required binds; no anonymous binds.
- Support for LDAP multi-factor authentication integration.
You may also be able to find a free cloud LDAP solution that fits your needs.
Azure AD – LDAP Integration with JumpCloud
Directory-based, cloud-hosted LDAP services help organizations connect applications hosted outside of Azure with LDAP. Organizations can use the service under a SaaS model and only pay for what they need and use without worrying about the heavy lifting.
Further, IT environments in businesses today are diversifying; with SaaS now the business standard for applications, organizations must be able to accommodate an increasing number of processes and protocols. Similarly, as Mac, Linux, and mobile machines become more popular for business use, organizations need to be able to support more than just Windows devices. This changing environment calls for a more flexible and dynamic directory structure than Azure AD can offer — after all, Azure AD doesn’t truly replace AD; it still requires a connection to AD or AAD DS.
Open directories were designed with flexibility in mind. JumpCloud, for example, is an open directory platform that’s OS agnostic and supports LDAP, SAML, SCIM, to name a few. If authenticating to LDAP with Azure AD is causing you trouble, you’re likely to run into more bumps as you continue incorporating new, non-Microsoft and non-Windows resources into your stack. Open directories offer the flexibility to connect users to all the resources they need across a range of operating systems and protocols (without convoluted, multi-step processes that create unnecessary complexity). To learn more about how open directories power flexibility and diversity in your IT environment, read What Is an Open Directory?





