JumpCloud has introduced an enhanced Push, and Time-Based One-Time Password (TOTP) multi-factor authentication (MFA) capability to secure your access. This update simplifies the enrollment process, providing users with the flexibility and control of both Push, and TOTP methods, while maintaining robust security.
Admins with billing role can enable this feature through the MFA settings in their Admin Portal. Once enabled, existing users will continue to log in using their previously configured MFA methods, alongside the new unified experience. This ensures a seamless experience with no disruption to current user access or workflows.
If a user previously configured TOTP with a third-party authenticator and then switches to JumpCloud Protect TOTP, access from the third-party app will be retained until the user resets the JumpCloud Protect app.
Prerequisites
At least one MFA method is mandatory at all times.
Enrolling Users for the Unified MFA Experience
To enable the JumpCloud Protect unified MFA experience for users in your org:
- Log in to the JumpCloud Admin Portal.
If your data is stored outside of the US, check which login URL you should be using depending on your region, see JumpCloud Data Centers to learn more.
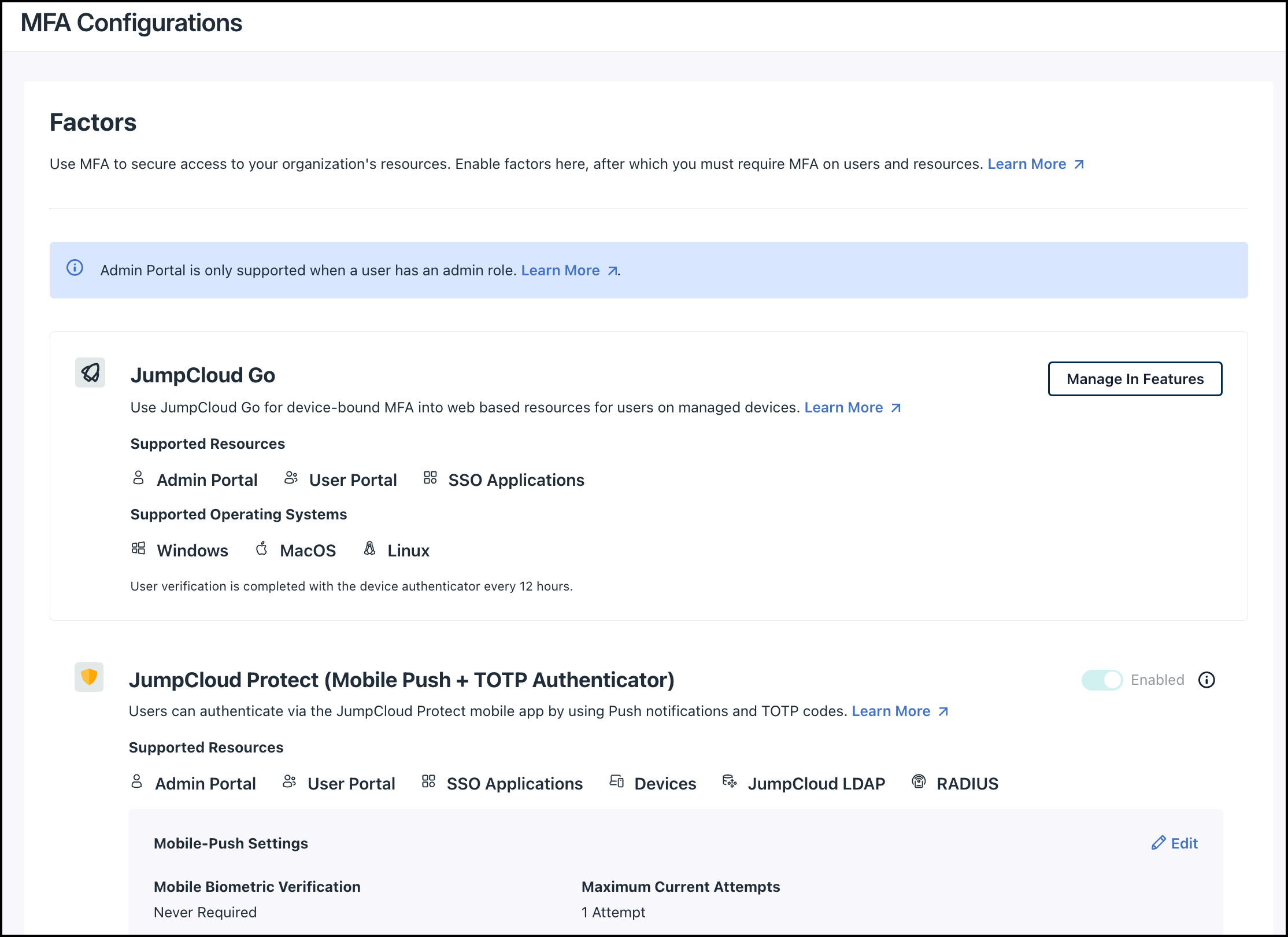
- Go to Security > MFA Configurations.
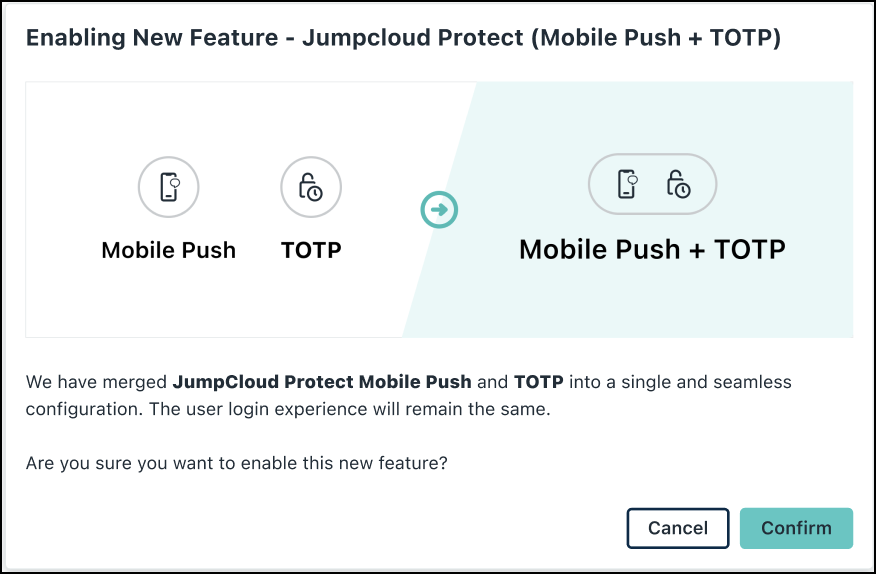
- A banner appears at the top, notifying you about merging JumpCloud Protect Push and TOTP. Click Merge.
- You’ll be prompted to verify before continuing. Click Confirm.
The JumpCloud Protect settings for both Push and TOTP authenticator code notifications are now unified and shown in a single view.
If you have users in a region where JumpCloud Protect Push cannot be enrolled, add those users to a dedicated group and exclude that group from Push enforcement. This way, you can maintain a unified JumpCloud Protect experience (Push and TOTP) while allowing those users to use only TOTP.
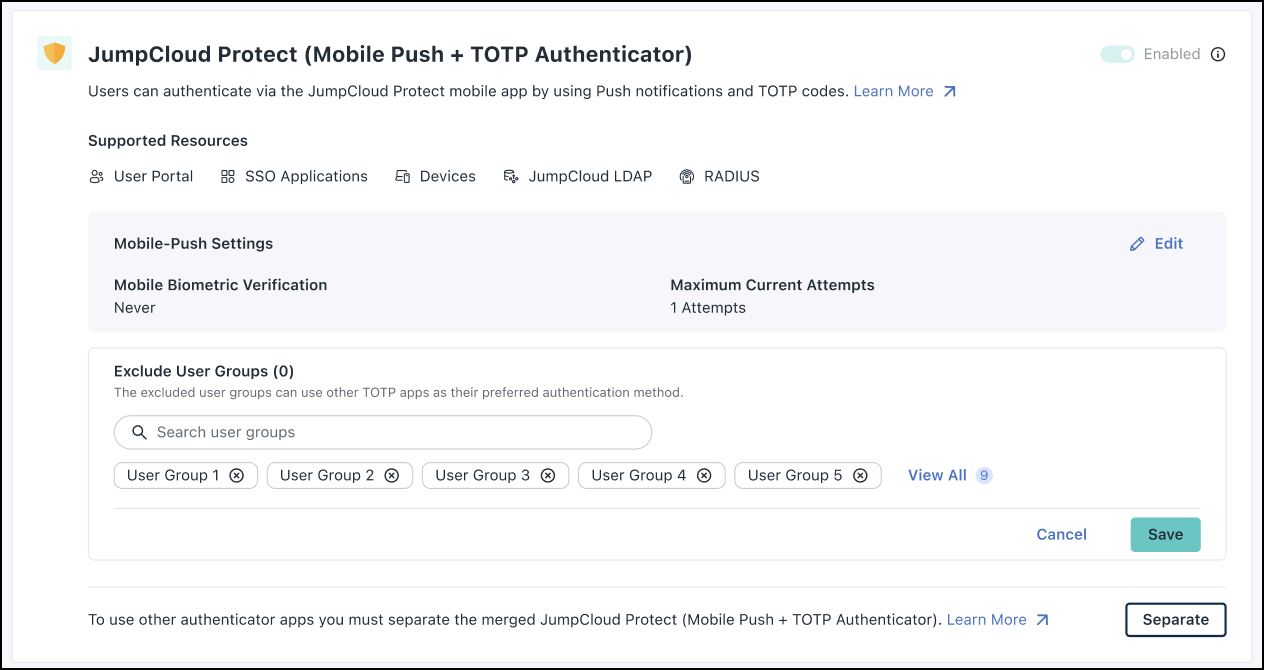
Admins can search for user groups to be excluded from unified MFA experience. The users in these groups can use apps other than JumpCloud Protect for 2-factor authentication. Search for the required user groups, select them and click Save.
Admins have to choose between TOTP with JumpCloud Protect, or TOTP with other vendors (e.g., Microsoft Authenticator), as both cannot be enabled simultaneously.
Unenrolling Users from the Unified MFA Experience
The unified MFA experience offers a one-step enrollment for both Push, and TOTP authenticator codes by scanning a single QR code. It’s not recommended to unenroll users from this process.
To unenroll users from JumpCloud Protect Push, and TOTP unified MFA experience:
- In the JumpCloud Admin portal, go to Security > MFA Configurations.
- Under Jumpcloud Protect, click Separate.
- You’ll be prompted to verify before continuing, click Confirm.
Now the JumpCloud Protect Push, and TOTP authenticator code settings are separated.
When the Admin unenrolls a user, the settings for Push, and TOTP authenticator code MFA are displayed separately in the user portal.
Unified MFA Experience for Users
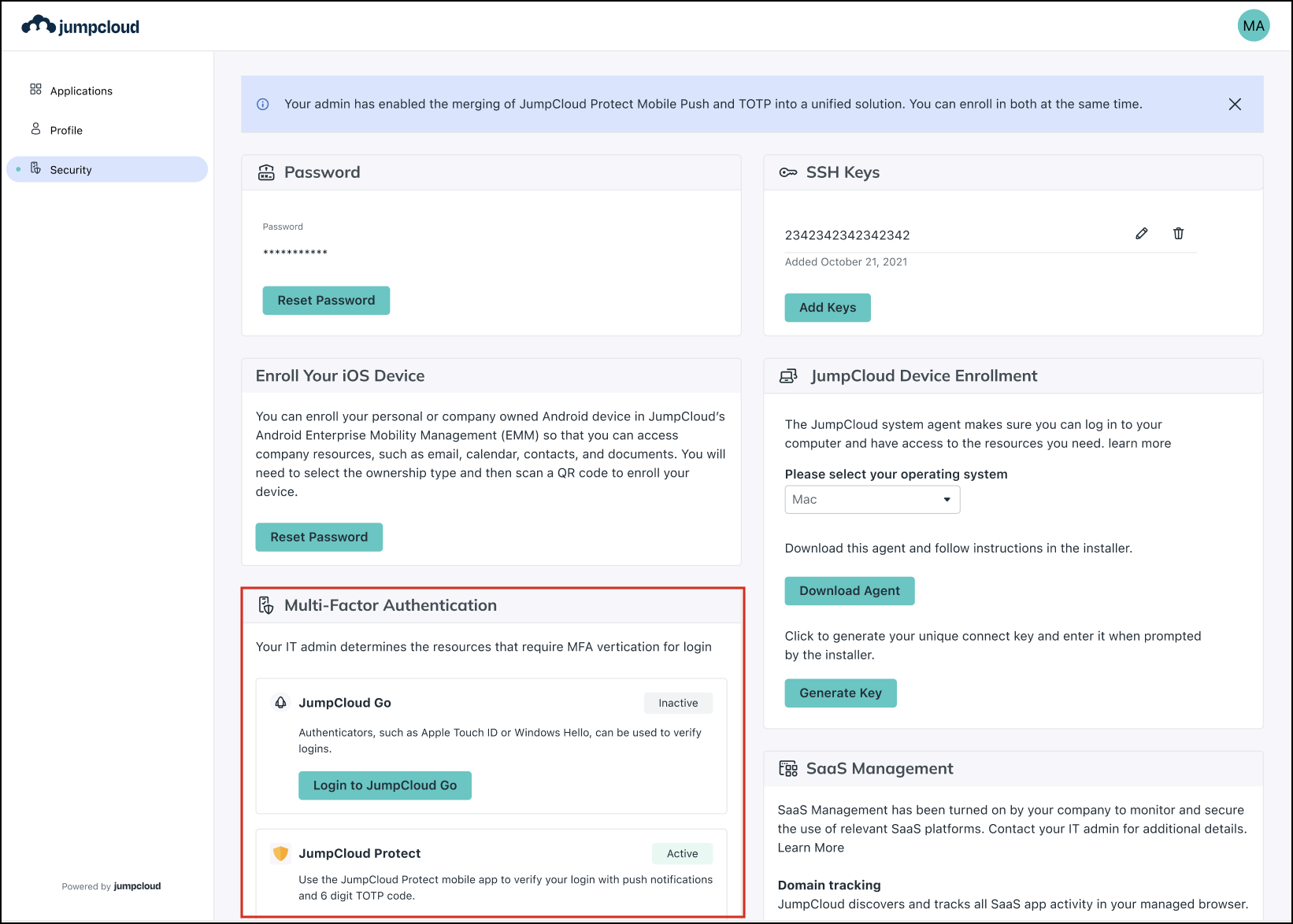
After an Admin enables the unified MFA experience, a banner is displayed in the User Portal on the Security settings page. In the Multi-Factor Authentication section, the JumpCloud Protect option is Active.
Users will receive a notification that their push account has been successfully migrated to JumpCloud Protect. Log in to your JumpCloud Protect App. In the Account Details, both Push, and TOTP MFA details are visible. If the user tries to delete the account, they’ll see a warning message.
If an Admin unenrolls a user from the unified experience, the settings for Push, and TOTP authenticator code MFA will be displayed separately in the user portal. Under Security settings, the user can delete the existing device and/or sign up for another TOTP vendor.
Unenrolling from the JumpCloud unified MFA experience is not recommended, as it may prevent users from accessing their JumpCloud account.
FAQ: Unified MFA Experience with JumpCloud Protect
TOTP with JumpCloud Protect and TOTP with other vendors can't be enabled simultaneously for devices and users for install base tenants.
Admins will need to opt in to this feature on the Admin portal by going to SECURITY MANAGEMENT > MFA Configurations in order to access the new unified authentication experience in the UI.
Only Admins with Billing role can enable unified experience with JumpCloud Protect.
Users/Admin can access both JumpCloud Protect TOTP and Push, and cannot have either one within the unified experience, allowing them to choose their preferred authentication method.
No new onboarding workflows for JumpCloud Protect will be introduced via email or other methods. The existing customer onboarding process will remain unchanged and will be revisited in future phases.
Yes. If a user has configured TOTP with a third-party authenticator before upgrade and decides to switch to JumpCloud Protect TOTP, enabling JumpCloud Protect will retain TOTP access from the other vendor’s app (until the user resets JumpCloud protect).
The next time users log in using Protect Push or Protect TOTP, the User Portal will reflect the updated unified experience.
After entering their username and password, users will be prompted for MFA and can log in using their previously enrolled factors, while the User Portal will encourage them to scan the QR code with the JumpCloud Protect mobile app (no manual entry of the 6-digit code required).
No.
No. With unified experience, we have merged Push and TOTP as a single MFA so the enrollment is a one-step process. Resetting the MFA method is also a one-step process. Both Push and TOTP will be reset simultaneously.
After entering their username and password, users will complete MFA with their existing factors. A banner on the landing or Security page will notify them of the update, and both Push and TOTP will be enabled via Protect.
Users will continue logging in using Protect Push and TOTP. In the Security tab, they will see two entries: one for Protect Push and another labeled Authenticator App, which includes a “Reset Authenticator App” button. If a user wishes to switch to a different authenticator app such as Google, Duo, or Authy, they must first click the reset button and authenticate using the TOTP from the JumpCloud Protect app. Once the reset is complete, they can enroll with their preferred third-party authenticator.
Admins not linked to users will continue using TOTP as their sole MFA factor. For admins linked to users, a one-step enrollment for JC Protect Push and TOTP will be available, inheriting MFA enforcement from the user. Admins not merged with users will only log in via TOTP and will not have access to this feature.