Symptom
When configuring a device or application for use with JumpCloud RADIUS, users are not able to authenticate to WiFi or VPN.
Cause
This may be due to one or more reasons:
- Misconfigured device/application
- Configuration mismatch between the RADIUS record in JumpCloud and the device/application
- User is not a member of a group granted access to JumpCloud RADIUS record
- Misconfigured client
- Network problems
- Incorrect credentials
Resolution
Note: JumpCloud RADIUS servers do not respond to ICMP, so ping will not respond if you attempt a basic availability check.
- Make sure the password being used works as expected with the JumpCloud User Portal. Though the portal uses the email address, RADIUS expects the username and password, NOT email address and password.
- When authenticating with delegated auth for Entra ID, the UPN in Entra ID should match the company email address in JumpCloud and the user should be using this attribute for their Radius login.
- Make sure if your IdP is JumpCloud the credentials being used are JumpCloud, and if the IdP is Entra ID that the credentials being used are Entra ID.
- Verify the public IP address where the requests originate and compare it to the RADIUS record in the JumpCloud Console. This can be done with WhatIsMyIP.com or using
# curl ifconfig.cofrom a shell. - Verify the shared secret. For some devices/applications, complex strings will cause a failure. If this is suspected, change the shared secret to a short alpha/numeric string.
- Verify users are members of a User Group that has been granted access to RADIUS. See Binding Users to Resources.
- Make sure that users are in an active state.
- Verify port 1812/UDP is being used and the network is not blocking that traffic.
- Make sure you have not missed a step in the certificate or profile installation. See Update RADIUS Certificates on Existing EAP-TTLS Client Systems.
- If the RADIUS client has a testing option and still fails, test the RADIUS connection on an independent device such as a computer with an internet connection that uses the public IP address configured both in your RADIUS client & JumpCloud endpoint to pinpoint whether there's an error with your RADIUS client configuration or a connection issue to one of our RADIUS endpoints.
Use one of the following third-party tools to test:
Note: You must input the following parameters to receive a valid request response from both tools:
- Destination JumpCloud RADIUS server IP address with UDP port number 1812.
- The RADIUS NAP IP attribute or public IP address provided by your ISP or cloud provide along with the NAS port number (typically 61).
- An active JumpCloud username or email address and password that's bound to your JumpCloud RADIUS endpoint.
- For Windows devices, use ntradping by unzipping the file and selecting Run as administrator on the executable. Ensure the Request type field is set to Authentication Request.

- For macOS & Linux, use the radtest server from freeradius.org that requires the Homebrew package manager. Once the Homebrew package manager is installed on your device, enter the following command:
brew install freeradius-server
Use the following syntax for radtest in your Unix terminal:
radtest -t mschap username password 18.204.0.31:1812 61 sharedsecret -4 INSERT_PUBLIC_IP
Note: You can exclude -t mschap to test with the PAP protocol.
If your authentication attempt was successful, you will receive a response message of Access-Accept.

You can also verify these results in both the Directory Insights portal and the RADIUS section of your Admin Portal by navigating to Details > Network Device Details of your JumpCloud endpoint.


If these solutions do not resolve the issue, note the username failing to authenticate, your Organization ID, a timestamp of the attempt(s)/failure(s), if possible, logs from the application/device, and submit a support request for further assistance.
Symptoms
Multiple failed RADIUS authentication attempts are seen the in Directory Insights (DI), even though the end user hasn't initiated the authentication attempts.
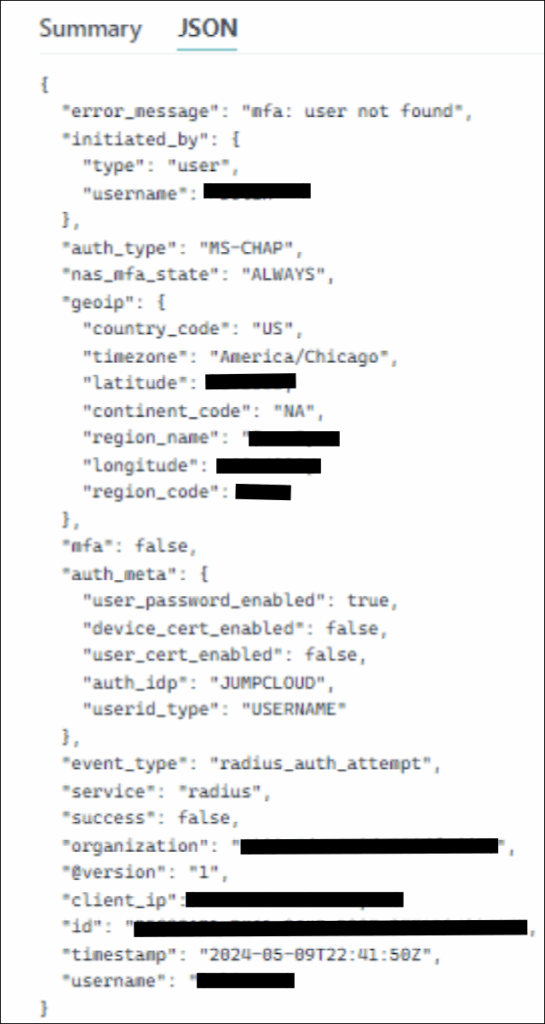
For example, the screenshot below is a JSON from the RADIUS failed event which contains information such as Username, Error Message, Country Code, Region Code, and Timezone. It is also observed that an "User not found" error message is displayed as no such user exits in the organization.
Cause
Failed Directory Insights events are generated anytime RADIUS authentication fails. This may occur when an employee attempts to authenticate with invalid credentials, or it may also indicate potential threat actor attempts.
Resolution
The following preventive measures can be taken:
- Enforce MFA for your users when authenticating to JumpCloud RADIUS servers.
- Rotate your RADIUS Shared Secret.
- Use passwordless authentication. See Passwordless (Certificate Based) Authentication for more information.