The SAML 2.0 Connector and pre-built connectors support the ability to add additional attributes to a SAML/SSO configuration.
Finding and Configuring SAML Attributes
- Log in to the JumpCloud Admin Portal.
If your data is stored outside of the US, check which login URL you should be using depending on your region, see JumpCloud Data Centers to learn more.
- Go to Access > SSO Applications.
- To configure attributes for a new application:
- Type the name of the application in the Search field, select it and then click Next
- In the Display Label, type your name for the application. Optionally, you can enter a Description, adjust the User Portal Image and choose to hide or Show in User Portal
- Click Save Application and then click Configure Application
- Select the SSO tab and scroll down to the Attributes section
- Configure User Attributes and Constant Attributes
- To configure group attributes, select Include Group Attribute
- Click Save.
Attributes
A SAML attribute is a piece of information about a user that is included in a SAML assertion. It is a name-value pair that is used by the SP to make decisions about the user's access to the protected resource. SAML attributes can also be used to support advanced authentication and authorization scenarios, such as role-based access control or single sign-on (SSO).
User Attributes
Before configuring user attributes for SAML connectors, make sure you’ve populated the standard and custom user attributes that you plan to use with SAML SSO. User attribute values are unique to each user and are located in the Details tab of the user's record. Some standard user attributes are required when you create a new user, like Username and Company Email.
Service Provider Required User Attributes
When you configure user attributes for a pre-built connector, you see some user attributes that are pre-populated. These user attributes are required by the Service Provider (SP) for SAML SSO authentication. You can edit the Service Provider Attribute Name; you can’t edit the JumpCloud Attribute Name. However, you can choose a different JumpCloud attribute or create a custom attribute to map to the Service Provider Attribute Name.
JIT Required User Attributes
Some pre-built connectors support Just-in-Time (JIT) provisioning and require additional attributes. JIT required attributes are pre-populated and are enabled for JIT provisioning by default.
Keep the following in mind when working with JIT attributes:
- You can’t edit the JIT required Service Provider Attribute Name.
- You can customize the JumpCloud Attribute Name and the Constant Value for JIT required attributes.
- Toggle off the attributes if you’d like to opt out of sending the attributes in the SAML assertion. Learn more about SAML.
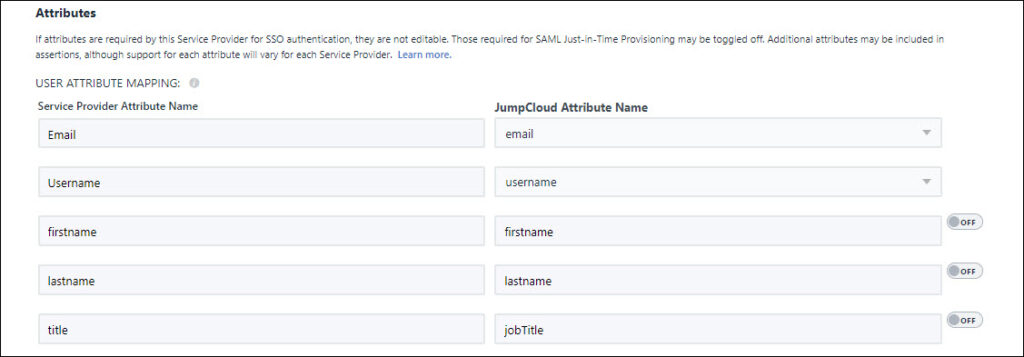
User Attribute Mapping
As the Identity Provider (IdP), JumpCloud sends specific information in the SAML assertion to be extracted by the (SP). Within the assertion, JumpCloud attributes are mapped to the SP's required user attributes to log in a user with SAML. As shown below, JumpCloud attributes are mapped to Slack's required attributes, e.g., User.Email, first_name and last_name.
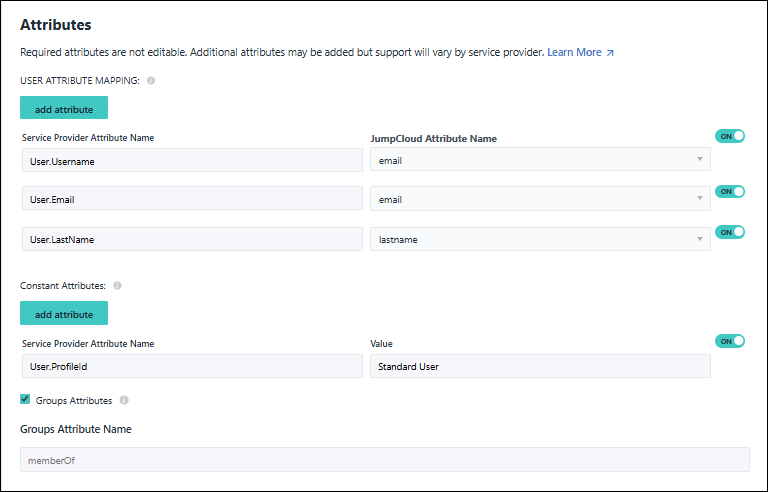
Additional User Attributes
You can add additional user attributes to customize user roles and permissions for an application. Read how to configure additional user attributes for SAML connectors.
Constant Attributes
Constant attributes apply to all users. For example, a constant attribute for session duration limits session times for all users of the application, or SP.
Group Attributes
- Groups that connect the user to the application are included in assertions to that application. The Groups Attribute Name is the SP's name of the group attribute (e.g. memberOf).
- If the Groups Attributes option is selected and the field is prepopulated with the group attribute name, that means we’ve validated that the group attribute is supported by the SP. If the group attribute option isn’t selected and the Group Attribute Name field is empty, you need to find out if the SP supports group attributes on your own. See Group Inherited User Attributes for more information.
When you select the group attribute option for a connector, you must include a Groups Attribute Name. You'll receive an error when you attempt to activate the connector if you select this option and leave Groups Attribute Name blank.
- Group attributes may be used in some SPs, like AWS IAM, to map roles. To learn more, see Integrate with Amazon IAM (Multiple Roles).