Updated on October 3, 2025
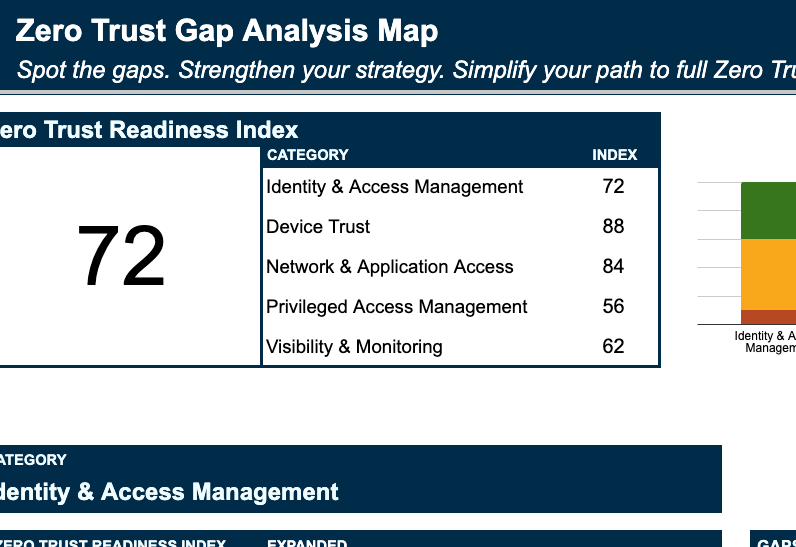
The shift to Zero Trust security has transformed how enterprises approach identity and access management, necessitating IAM solutions that verify every user and device. Five trusted choices for enterprise Zero Trust implementations are JumpCloud, Okta, Microsoft Entra ID, Ping Identity, and CyberArk Identity.
How We Ranked the Top IAM Platforms
Our ranking combines objective criteria and real-world performance data to help enterprise decision-makers select solutions that align with Zero Trust goals. We evaluated IAM software based on five critical factors:
- Zero Trust enforcement capabilities
- Device trust and unified MDM support
- Multi-OS coverage
- Integration ecosystem breadth
- Scalability with transparent pricing models
Zero-Trust Enforcement Criteria
Our evaluation centered on essential Zero Trust controls, including continuous authentication and risk-based policies. Key capabilities assessed include:
- Continuous user and device authentication
- Dynamic risk assessment based on context
- Granular policy enforcement across all access points
- Real-time threat detection and response
- Least-privilege access principles
- Session monitoring and adaptive controls
Device-Trust and Unified MDM Support
Device-trust verification and integrated mobile device management (MDM) are crucial for hybrid workforces. Organizations need platforms that verify device posture and provide unified management across operating systems.
| Platform | Device-Trust Capabilities | MDM Coverage |
|---|---|---|
| JumpCloud | Native device health checks, compliance policies | Windows, macOS, Linux, iOS, Android |
| Okta | Device trust with third-party MDM integration | Via integrations with major MDM providers |
| Microsoft Entra ID | Device compliance policies, Azure AD Join | Windows, iOS, Android (limited macOS/Linux) |
| Ping Identity | Device fingerprinting, adaptive authentication | Via partner integrations |
| CyberArk Identity | Device-bound privileged sessions | Limited native MDM, strong device authentication |
Managing diverse technology stacks and remote work models necessitates a single pane of glass for device management.
Multi-OS and Hybrid Environment Coverage
Support for multiple operating systems is non-negotiable for modern enterprises. With many enterprise fleets running non-Windows operating systems, organizations need IAM platforms that enforce consistent policies across diverse environments.
Key benefits of multi-OS support include:
- Reduced tool sprawl
- Consistent policy enforcement
- Simplified onboarding
- Unified reporting
- Lower administrative overhead
Effective platforms integrate on-premises infrastructure with cloud services, supporting the hybrid deployments required for digital transformation.
Integration Ecosystem Breadth
The breadth of integrations directly impacts deployment speed and maintenance costs. Key integration categories include:
- HRIS systems
- Business applications
- Security tools
- Infrastructure services
- Compliance platforms
API-first architectures enable custom integrations when pre-built connectors aren’t available.
Scalability, Pricing Transparency & ROI
Enterprise IAM platforms must scale to tens of thousands of users while providing transparent pricing models. Organizations typically see measurable ROI through:
- Reduced onboarding time
- Lowered administrative overhead
- Decreased breach risk
- Simplified compliance
Research indicates that organizations see up to 30% reduction in IAM operational costs after consolidation.
#1 JumpCloud – Open Cloud Directory with Built-In Device Management
JumpCloud combines directory services, SSO, MFA, PAM, and MDM in a single cloud-native platform, making it the ideal choice for enterprises seeking a unified solution to replace legacy systems.
Zero-Trust Controls Built into the Directory
JumpCloud’s native Zero Trust features include:
- Real-time device health assessment
- Location-based access policies
- Risk-based authentication
- Continuous monitoring of user behavior
- Automated policy enforcement
Organizations using Zero Trust architectures have seen a 50% reduction in the risk of data breaches.
Unified SSO, MFA, PAM & MDM for Windows, macOS, Linux, Mobile
JumpCloud delivers multiple capabilities through a single platform:
- SSO: Single credential access for cloud and on-premises applications.
- Passwordless Authentication: JumpCloud Go™ passwordless authentication boosts security with phishing-resistant technology.
- PAM: Privileged access controls include session recording.
- MDM: Policy enforcement across all devices ensures security standards.
“The JumpCloud platform has transformed our business from the ground up to operate more efficiently, effectively, and — most importantly — securely.”
The hipages Group Uses JumpCloud to Centralize Mobile Device Management & Supercharge Security
Real-World Enterprise Case: Global Tech Firm Scales to 5,000 Users
A global tech company migrated from multiple point solutions to JumpCloud, addressing diverse user management challenges. This resulted in a 40% reduction in onboarding time and successful compliance audit outcomes.
Migration Tips from AD and Point-Solution Stacks
To migrate to JumpCloud effectively:
- Inventory existing infrastructure. Document AD objects and group memberships.
- Leverage migration tools. Use JumpCloud’s AD connector or LDAP import tool.
- Start with a pilot group. Test the new platform with a small user cohort.
- Engage professional services. JumpCloud’s team can assist with complex integrations.
Zero-touch deployment capabilities streamline the provisioning process for remote workforces.
#2 Okta – Cloud-Native Identity Platform
Okta provides application access and adaptive security, offering risk assessment and policy enforcement capabilities.
Adaptive MFA & Policy-Based Access for Zero Trust
Okta’s Adaptive MFA evaluates real-time risk signals to determine authentication requirements, reducing friction for low-risk scenarios.
Extensive SaaS Catalog & API-First Integrations
Okta’s integration strength spans essential categories for enterprise operations:
- HR systems
- CRM platforms
- ERP solutions
- Collaboration tools
The API-first architecture enables custom connectors for proprietary applications.
Deployment Considerations for Large User Bases
Consider scaling factors during large-scale Okta deployments:
- API rate limits
- Regional data residency
- Administrative delegation
| Deployment Model | Use Case | Considerations |
|---|---|---|
| Cloud-Only | Pure SaaS environments | Fast deployment, limited integration |
| Hybrid | Mixed cloud/on-premises | Requires AD agents |
| Multi-tenant | Large enterprises with subsidiaries | Enhanced isolation |
#3 Microsoft Entra ID – Integrated Identity for the Microsoft Cloud
Microsoft Entra ID is the native identity layer for Azure and Microsoft 365, providing integration and conditional access capabilities.
Conditional Access & Risk-Based Sign-In Policies
Entra ID enables administrators to create granular policies that evaluate multiple risk factors before granting access.
Seamless Azure & Windows Integration, Hybrid AD Extension
Entra ID synchronizes with on-premises Active Directory, extending identity infrastructure to the cloud.
Licensing & Cost-Model Overview
Microsoft offers three primary licensing tiers for Entra ID:
- Entra ID Free: Basic directory services and limited SSO.
- Entra ID Premium P1: Adds conditional access and dynamic groups.
- Entra ID Premium P2: Includes identity protection and management features.
#4 Ping Identity – API-First Identity for Complex Hybrid Environments
Ping Identity focuses on API security and microservices authentication, serving complex environments.
Intelligent Authentication & Token-Based Zero Trust
Ping’s Zero Trust approach centers on token-based authentication flows, using standards like OAuth 2.0 and OpenID Connect.
Support for Micro-Services & API Security
Key features include:
- API gateway integration
- JSON Web Token (JWT) signing
- Dynamic scope enforcement
Integration Tips with Legacy LDAP and On-Prem Apps
Integrating Ping Identity requires:
- Deploying PingFederate as an LDAP bridge.
- Mapping legacy groups to dynamic groups in PingOne.
- Testing SSO flows before full deployment.
#5 CyberArk Identity – Privileged-Access-Focused IAM
CyberArk specializes in protecting high-privilege credentials, combining traditional PAM features with identity management capabilities.
PAM-Centric Zero-Trust Controls for High-Privilege Accounts
CyberArk’s Zero Trust focus on privileged accounts includes credential vaulting and just-in-time access provisioning.
Credential Vaulting, Secret Management, and Session Monitoring
Core features include:
- Credential vaulting
- Secret management
- Session recording
- Threat analytics
- Risk scoring
Example: Manufacturing Firm Safeguards OT & IT Convergence
CyberArk’s implementation created isolated credential vaults for operational technology systems, ensuring authorized access while maintaining operational continuity.
Scaling Privileged Access in a Hybrid Workforce
Strategies for scaling privileged access management include:
- Role-based JIT policies
- Cloud-native secret storage
- MDM integration
How to Choose the Right IAM Solution for Your Organization
Selecting the optimal IAM platform depends on business context, technical requirements, and organizational constraints.
Decision-Tree: Size, Compliance, Device Landscape, Budget
| Organization Size | Primary Recommendation | Alternative Options |
|---|---|---|
| SMB (100-500 users) | JumpCloud (unified approach) | Okta (application focus) |
| Mid-Market (500-5,000 users) | JumpCloud (comprehensive platform) | Okta, Entra ID (Microsoft shops) |
| Enterprise (5,000+ users) | JumpCloud (scalable unified solution) | Platform-specific based on primary use case |
Evaluating Total Cost of Ownership vs. Feature Set
Total cost of ownership extends beyond subscription fees, including implementation services, training costs, and ongoing overhead.
Pilot-Program Best Practices
Successful IAM deployments begin with planned pilot programs that validate capabilities:
- Define quantitative success metrics.
- Select representative user groups.
- Deploy with minimal customization.
- Collect structured feedback after 30 days.
- Iterate based on pilot results.
Frequently Asked Questions
How do I migrate from Active Directory to a cloud-native IAM tool?
Migration from Active Directory requires a phased approach. Export existing AD objects, map them to the new platform’s schema, and use hybrid connectors for gradual migration. Validate access patterns with a pilot group before full cutover.
Can these IAM platforms enforce Zero-Trust across all device types?
Yes, all five platforms provide device-trust verification and policy enforcement for diverse devices, though approaches vary. JumpCloud offers the most comprehensive native MDM, while others integrate with third-party MDM providers.
What is the typical timeline to deploy an enterprise IAM solution?
Deployment timelines vary. Small pilots typically take 8-12 weeks, mid-market deployments 3-4 months, and enterprise-wide implementations can extend to 6-12 months, depending on complexity.
How do I handle privileged-access management alongside standard IAM?
Implement a layered security approach using IAM for everyday access and specialized PAM for high-privilege credentials, integrating both for comprehensive protection.
Which tool offers the most cost-effective licensing for a 1,000-user org?
For a 1,000-user organization, JumpCloud often provides the best value with its bundled model that includes comprehensive device management. Okta can be competitive for SSO and MFA only, while Microsoft Entra ID may be cost-effective for existing Microsoft 365 or Azure users. However, it’s worth considering the total cost of ownership and the tradeoffs of relying on Microsoft’s ecosystem.
What if a custom SaaS app isn’t in the vendor’s pre-built catalog?
Most modern IAM platforms support industry-standard protocols for custom application integration. When connectors aren’t available, generic SSO templates and API-first architectures facilitate development for proprietary applications.