“Let’s start a business that never grows!” said no one ever.
Thriving businesses translate to increased profits, enhanced market share, and more jobs. Unfortunately, the same growth also paves the way for new challenges.
According to Allianz’s 2023 Risk Barometer, cyber incidents — IT outages, ransomware attacks, and data breaches — rank as the most important corporate concern globally for the second year in a row. Business interruption and macroeconomic developments came in second and third.
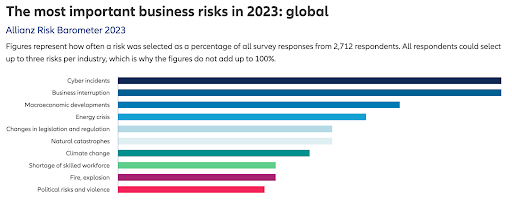
The organization surveyed more than 2,700 risk management experts from a record 94 countries and territories to generate the results. As IT admins know, an increase in employees and customers leads to more end user devices and cloud-based applications, all of which are entry points for bad actors.
Maintaining devices with the latest patches is a huge undertaking in and of itself. Combine that with a never-ending list of issues from end users in remote locations, and admins have an unmanageable workload on their hands. And the minimal sharing features of WebEx, Zoom, and Teams to help admins see what’s happening on an impacted machine, or take control to troubleshoot further, compound this challenge, making it difficult to get to the bottom of end user issues.
But there’s one thing that can make it easier: unattended access. This post will explain what unattended access is, how to unify your IT stack with it for efficiency, and what to look for in an all-in-one unattended access solution.
What Is Unattended Access?

Unattended access, also referred to as unattended remote access, allows users to remotely control devices even when they are not actively in use. In today’s globalized business landscape and with the rise of remote work, the demand for efficient and secure remote access solutions has significantly increased. With unattended access, businesses can streamline their operations and enhance security by granting authorized users the ability to remotely connect to devices, enabling seamless collaboration and productivity.
Unattended access is particularly useful for large, remote organizations with end users operating in multiple time zones. Without needing a user to grant access to files or devices, IT can provide 24/7 remote support, install necessary updates and patches, easily set and enforce identity management, and any other security tasks from anywhere.
The best unattended access solutions come with built-in technician authentication, authorization, and data encryption methods to safeguard any data transmissions during a remote session. Direct connections and copy-and-paste functionality can also enhance unattended access performance. And central logging and back-end reporting can give IT broad usage and security insights across company assets.
Unattended Access Use Cases and Benefits
Unattended access is becoming a must-have as companies continue to adopt fully remote or hybrid workforces.
Being able to manage access to every device regardless of where it’s located can help enterprises avoid privacy and compliance violations, poor authentication, and other risky behavior, particularly in sensitive industries like finance or healthcare.
Unattended access can uphold security best practices on:
- Kiosks
- IoT devices
- Point of sale devices
- Remote learning applications
- Specialized video or modeling software
- Telemedicine and medical record portals

Implementing unattended access also provides a myriad other benefits, such as:
- Faster ticket completion: When troubleshooting, IT teams with unattended access can see what’s happening on someone’s device rather than just reading a ticket description. Direct interaction with devices and applications gives IT a better sense of what might be happening, helping them prioritize and get through their ticket backlog.
- Improved IT productivity: Being able to triage problems faster streamlines IT’s workflow and maintenance tasks, allowing them to work on more pressing issues related to networks, systems, and customer support.
- Less friction for end users: End users get their problems solved faster with near-instant remote assistance. Quick and efficient resolution enables employees to get back to the important, strategic tasks on their plates.
- Easier updates and patching: Installing updates can be the bane of employees’ existence, and they often put it off as long as possible. However, unattended access puts IT in the driver’s seat — they can schedule patches or perform them directly with minimal employee disruption.
At this point, you may be thinking there is nothing to lose when it comes to unattended access. But, as with most IT practices, the technology has some drawbacks.
Unattended Access Risks
Below are some potential risks to become aware of when implementing it:
- Trust and privacy: Employees may react strongly to having someone else access their computer, and rightly so. Companies should outline policies detailing how and when to use unattended access. These policies should be communicated to every employee via email, All Hands meetings, or other company forums.
- Unauthorized use: Every IT staff member with unattended access privileges should be trained on and abide by company practices. Monitoring IT teams’ unattended access activity on a regular basis can help avoid breaches of employee and customer privacy.
- Connectivity: Unattended access relies on a stable internet connection. Devices without a solid signal could impact your IT teams’ speed and effectiveness. Look for unattended access solutions that can work on Mac, Linux, and Windows devices and provide a secure peer-to-peer connection. You might also consider boosting internet connections where possible to enhance access and efficiency.
While there is a range of unattended access solutions on the market, not all will suit your organization’s IT or managed service provider (MSP) requirements. Keep reading to learn more about the best unattended access solution for heterogeneous environments.
Unattended Access With JumpCloud Remote Assist
JumpCloud Remote Assist’s silent assist features (coming soon!) benefit IT teams and MSPs, enabling admins to connect directly to end user machines — regardless of their OS — in real time to resolve technical problems and manage identity, access, and devices all in one platform. It features:
Multi-OS Support
Most remote assist tools are focused on Windows, depend on proprietary remote desktop protocols and technology, and require companies to relax their firewall rules. JumpCloud Remote Assist enables remote assistance for Windows, Mac, and Linux devices directly from browsers like Firefox, Chrome, Safari, and Edge with out-of-the-box encryption.
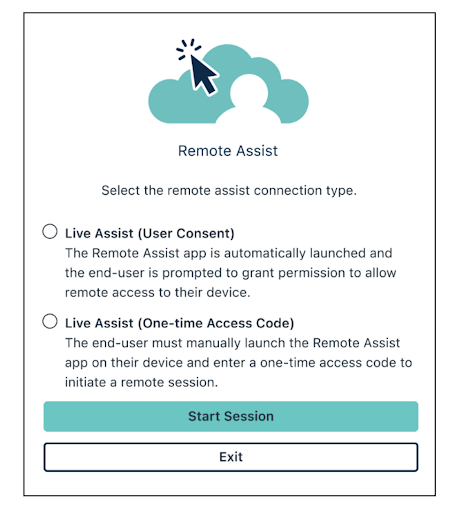
Session Launch With and Without Consent
Users want to know when someone will be assuming control over their device. JumpCloud lets admins give end users a heads-up but can also launch without a user’s consent in an emergency.
Lock Screen Access
Admins can unlock a device’s locked screen, even without knowing the end user’s password. Then, when remote support is finished, admins can lock the screen again.
Logon Screen Access
IT teams and MSPs can access the sign-in screen of a remote device through their connection and set permissions to control who can leverage logon screen access to minimize unauthorized usage.
Windows UAC Support
Technicians can see and control the Windows UAC prompt for activities that require elevated privileges, such as modifying system settings, without sharing their admin credentials with end users.
Other MSP Benefits With JumpCloud
With JumpCloud, managed services providers have the added advantage of a one-click remote control solution that integrates with their ticketing and billing systems.
JumpCloud Remote Assist integrates with PSA, CRM, and ITSM tools like ServiceNow, Zendesk, Autotask, and Freshdesk, enabling MSPs to launch a remote desktop session directly from an incident, ticket, or chat.
They can also automatically update tickets with details from the support session and include the session recording in the ticket. These additional features accelerate MSP reselling margins while decreasing operating costs and security risks.
Sign up for a free trial and explore JumpCloud pricing today.




