Multi-factor authentication (MFA) is now one of the core methods for securing user access to IT resources, and a critical component of a Zero Trust security model. With the rise of remote work and the continued prevalence of high-profile data breaches, many organizations are evaluating their options for implementing MFA policies.
According to a recent survey of IT professionals, 52.6 percent of small and medium-sized enterprises already require MFA across all applications and logins. This article is geared towards the remaining organizations trying to figure out the best way to do that while avoiding resistance from decision makers and end users.
An excellent option for a frictionless MFA experience is push notification-based MFA, but how does it compare to other implementation options?
What is MFA & Why Should You Use It?
Multi-factor authentication (also called two-factor authentication or 2FA) is the practice of requiring an additional factor beyond the standard username/password combination requested at most logins. Oftentimes, these factors are colloquially known as:
- “Something you know” – includes username/password credentials, but also applies to security questions or similar factors
- “Something you have” – pertains to device-based MFA options like mobile passcodes or physical keys
- “Something you are” – generally refers to biometrics.
According to Verizon’s 2021 Data Breach Investigation Report, 61% of data breaches involve credentials. When used as a single factor, passwords are an insufficient security measure and unable to protect your organization from the costs of a data breach. Layering on a second authentication factor at login is significantly more secure than relying on passwords alone, and can make accounts 99.9% less likely to be compromised.
So how much of an effect does the type of additional factor have? Well, Google’s Security Blog studied the effects of MFA on account takeovers. Here’s what they found:
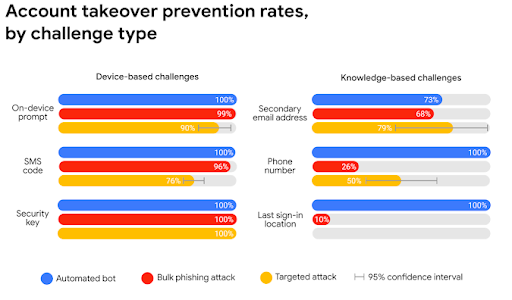
The chart above details the efficacy of the six most popular “something you have” and “something you know” MFA methods. With this chart in mind, let’s look at how push notification MFA (which falls under the “On-Device Prompt” classification) compares to the other forms of multi-factor authentication an organization can deploy.
What is Push Notification MFA?
Push MFA utilizes smartphone notifications to assert authentication. This puts push MFA in the category of “something you have,” as the user will need to have their smartphone on them to use push notifications as a second factor. After inputting their username and password, end users simply need to unlock their phone and then press a button to either approve or deny the access request.
Push notifications are growing in popularity thanks to the ease of use for end users and the low cost of implementation for IT admins. To best illustrate the benefits of this authentication factor, the following sections highlight the similarities and differences between push notifications and other MFA implementation options.
Push Notifications vs. Other MFA Factors
SMS-based MFA
SMS-based MFA is one of the more widely-used forms of MFA in use today. This method sends a login code to an end user’s phone or email after they have submitted their credentials. Once they receive the code, they must input it correctly to complete the login.
Per the Google chart above, SMS-based MFA offers effective security for automated and bulk phishing attacks, but is less effective for accounts that are specifically targeted. This security vulnerability is due to the need for a third-party network to act as the middleman between the origin of the code and the end user. This provides an additional attack vector, as well as a larger window of time in which foul play can occur.
Push notifications, on the other hand, are created directly on a user’s smartphone with an authenticator app and do not require the user to input a numerical code. This not only provides a simpler user experience, it also saves employees time. In fact, push MFA saves a user 13 minutes annually over SMS-based MFA.
Time-based One-Time Password (TOTP)
TOTP MFA utilizes a randomly generated code similar to that of SMS-based MFA. In contrast to SMS, however, TOTP codes are generated the same way as push notifications—via an authenticator app. The numerical codes are only valid for a specific time interval, such as 30 seconds. The user must correctly input the TOTP before the end of the time period since once it ends, a new code is generated and the previous one is rendered null.
TOTP is generally considered more secure than SMS, falling under the “On-Device Prompt” classification in the chart above. TOTP is continuing to gain in popularity although some users find inputting the code within the time limit to be a cumbersome process. IT admins, however, find TOTP quite easy to manage.
Push notifications operate very similarly to TOTP and provide the same level of security with a better user experience. A good authenticator app will provide the option for both TOTP and push MFA, and empower employees to choose the second authentication factor that works best for them. This is especially important for putting MFA accessibility considerations into practice.
Physical Keys
Physical key-based MFA is akin to a digital version of a tangible lock and key. Each physical key — often represented in the form of a USB stick like Google Titan — is unique to its user. As long as the user maintains possession of their key, their authentication should be hyper-secured. Google backs this up with their research from the chart above, claiming 100% efficacy at blocking most major forms of attack.
Although incredibly secure, physical key MFA has its own headaches. For starters, physical keys are expensive, and they require a significant amount of effort on the part of the IT admin to implement and tie in to each individual end user. Beyond that, there’s always potential for a physical key to be lost or stolen. In this case, an end user will be locked out of their associated accounts until the key is found or replaced.
Push notifications, however, are a more cost effective authentication factor and less of a hassle to implement at scale. These benefits can definitely be worth it for IT admins, as the difference in security between push MFA and physical key MFA is negligible.
Biometrics
Science fiction has long speculated on the extent of biometric authentication, often represented by retinal scans and voice or facial recognition. Today’s day and age have made such biometrics a reality. Biometrics exemplify the “something you are” MFA factor, and many people have grown accustomed to using biometric authentication in the form of a fingerprint reader or face ID on their smartphone or laptop.
Although it is still challenging to manage biometric MFA at scale in today’s enterprise settings, the use of an authenticator app can naturally add biometrics into the equation. For example, to accept a push notification, the user must first unlock their phone to respond to the request. How do most people unlock their phones these days? With a biometric identifier that inherently provides an additional layer of security.
How to Choose a Push Notification MFA Solution
IT organizations can use several different solutions to enforce MFA push notifications across their user base. There are three key considerations to keep in mind when evaluating MFA push notification solutions:
- Which IT resources need to be protected?
- How does the solution interact with existing tooling?
- How much will it cost?
The decision is easy for IT admins using the JumpCloud Directory Platform to manage virtually all of their IT resources. JumpCloud Protect is an authentication app available on both iOS and Android devices that integrates seamlessly with our cloud-based admin console, and allows for both push notifications and TOTP across cloud and on-premise applications, Mac, Windows, and Linux desktops, VPN and wireless networks, and servers.
It’s included in all packages at no extra cost. Try JumpCloud Protect today.



