U.S.government agencies control and store a lot of sensitive data. The Federal Information Security Management Act (FISMA) was adopted as a framework to keep that information from falling into the wrong hands.
Complying with FISMA requirements is mandatory for federal and state agencies, but it also carries significant benefits that can translate into readiness for current and emerging cybersecurity threats. This article breaks down what FISMA is, its requirements,non-compliance penalties, and how JumpCloud can help your organization to comply with FISMA.
What Is the Federal Information Security Management Act (FISMA)?
FISMA, is a U.S. federal legislation that provides a framework for protecting government information and operations. It was enacted into law in 2002 as part of the E-Government Act and has become one of the most significant regulations for reducing information security risks.
The E-Government Act was enacted to allow U.S. federal and state agencies to improve e-government services and processes while enabling them to manage federal spending regarding information security. At the core of the E-Government Act is the FISMA framework, which provides a framework for U.S. agencies to leverage to minimize information security risks while emphasizing cost-effectiveness.
The framework has broadened to also include private businesses that hold contracts with the U.S. government. FISMA assigns some of its responsibilities to other federal agencies, such as NIST(National Institute of Standards and Technology) and OMB (Office of Management and Budget).
FISMA requires agency officers including chief information officers (CIOs) and inspector generals (IGs) to formulate and implement policies and controls that can mitigate information security risks to acceptable levels and in a cost-effective manner.
Once implemented, these officials must undertake an annual review of their security programs and report the same to OMB, which uses the supplied data to assist in its oversight responsibilities. The OMB can also leverage this data when preparing a compliance report for congressional oversight.
FISMA Compliance Requirements
The requirements for complying with FISMA are vast and are intended to offer flexibility. The steps a company needs to take will differ depending on factors such as the type of organization, information the organization handles, risk profiles, and more. NIST outlines several steps toward complying with FISMA. These are some of those requirements:
- Maintaining information security inventory. Federal agencies and contractors must keep an updated inventory of all their IT assets. In addition, the inventory must also maintain an updated identification of any interface, such as an application programming interface (API) that a system uses to interact with other systems or networks.
- Risk categorization. Agencies must categorize information systems based on risk levels. For example, systems that store the most sensitive data need to be implemented with robust security measures to prevent their data from being compromised and remaining compliant.
- Maintaining security controls. FISMA requires agencies to meet security requirements defined by Federal Information Processing Standard (FIPS) 200. However, while agencies are not obligated to implement every security control, they need to document selected controls in their security plans once they have implemented them.
- Refining controls using a risk assessment procedure. Agencies need to validate their security measures to determine if they need any other controls.
- Conducting annual security reviews. FISMA requires information security program officials to conduct annual security reviews to ensure they have implemented sufficient security measures. Continuous monitoring must include status reporting, configuration management, and any changes made to the system.
NIST 800-53 Framework
Agencies must implement risk-based information security programs that comply with applicable legislation, executive directives, and orders. NIST Risk Management Framework (RMF) defines a holistic, flexible, and repeatable seven-step process that agencies must implement to manage security and privacy risks.
The NIST RMF’s risk-based approach helps agencies and contractors to:
Prepare
Agencies must carry out essential activities and prepare all the departments within the organization to manage risks associated with security and privacy. The outcome of this step includes:
- Identifying key risk management roles within the agency
- Establishing risk management strategies and tolerance levels
- Developing and implementing an organization-wide strategy for continuous monitoring
- Identifying standard security controls and measures
Categorize
FISMA requires agencies to determine impact levels regarding security and privacy controls when it comes to hosted data and applications. The outcome of this phase includes:
- Documenting system characteristics
- Categorizing security of the system and data
- Classifying the decisions that information security officials have reviewed and approved
Select NIST SP 800-53 Controls
Agencies must choose, customize, and document all the security controls they deem necessary to protect their systems. The outcome of this step includes:
- Selecting control baselines and customizing them
- Designating security controls as system-specific, hybrid, or common
- Allocating security controls to specific system components
Implement Controls
Agencies should implement security controls and privacy measures for their system. This phase has two basic outcomes:
- Implementing security and privacy control measures
- Updating security and privacy plans to reflect the controls as implemented within the agency
Assess
Agencies need to evaluate if the implemented controls are operating as intended and generating the desired results. Some of the outcomes of this step include:
- Selecting the assessors or assessment team
- Developing security and privacy assessment plans
- Reviewing and approving assessment plans
- Developing security and privacy assessment reports
Authorize
FISMA requires agencies to provide accountability measures by requiring senior officers to determine whether the security and privacy risk levels are acceptable. For example, agency officials must provide risk responses and approve or deny authorization for the system or common security controls.
Continuously Monitor
Agency officials need to maintain an ongoing situational awareness of the status of the security exposure and support risk management decisions.
FISMA Non-Compliance Penalties
Agencies and contractors face a range of potential consequences for not complying with FISMA requirements. These penalties include:
- Reduction in federal funding. Federal contractors can lose some federal funding when they breach their contractual obligations regarding FISMA compliance.
- Censure from Congress. In case of a data breach, Congress can call the contractor or the agency to determine the scope of the damage and evaluate whether the breach is related to non-compliance with FISMA requirements. If Congress determines that the agency or contractor didn’t comply with FISMA requirements during the breach, it can remove the organization from future contracts.
- Reputational damage. Failing to comply with FISMA requirements can lead to potential data breaches, resulting in reputational damage for the affected agency or contractor.
How to Achieve FISMA Compliance
FISMA has emerged as an essential framework for reducing risks and keeping data safer, allowing agencies to minimize financial risks associated with data breach recovery. For non-government organizations (NGOs), FISMA compliance is crucial to becoming a contractor for U.S. federal and state agencies.
However, like any other regulatory compliance, complying with FISMA requirements can be time-consuming and costly for an organization. JumpCloud’s Directory Platform® is an intuitive, all-in-one cloud-based identity and access management (IAM) solution that can help you streamline compliance with FISMA requirements and other regulations.JumpCloud’s Directory® Platform
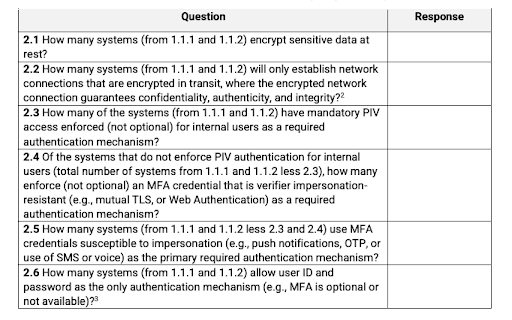
FISMA places heavy emphasis on the adoption of multi-factor authentication (MFA) and encryption. The publication 2022 CIO FISMA Metrics includes the following checklist covering authentication methods:
As a cloud-compliance solution, JumpCloud Directory enables IT teams to secure access to crucial IT assets within the organization — whether such assets are hosted on-prem or in cloud-based environments. It allows organizations to adhere to IT governance and compliance standards by incorporating security controls such as conditional access, MFA, multi-platform device management, and more.
For example, JumpCloud provides:
- SSH keys for servers, which are more secure than passwords
- Passwordless certificates to secure RADIUS Wi-Fi access
- SAML and OIDC for authentication into web apps
- Conditional access rules for privileged access management
Ready to start getting compliant? Read our IT Compliance Quickstart Guide to give you more insights as you prepare to shore up your IT security baseline.
Would you prefer tailored, white-glove implementation assistance? Learn more about JumpCloud Professional Services.





