Updated on December 20, 2024
Like snowflakes, no one person is quite the same as any other. Yet, when creating a user identity in a directory service, everyone starts out the same. How can an IT admin differentiate their users so that interns can’t access the VP’s expense report or contractors can’t tap into confidential information? Of course, this can be done manually on a user-by-user basis, but IT is always looking for a more efficient, systematic approach. That’s where group-based management and user attributes come in. But, you may be asking, what are user attributes?
History of User Attributes
In the early days of IT, the Lightweight Directory Access Protocol (LDAP) offered a way for sysadmins to better manage directories of their users. With the directory, admins could federate access between their users and their resources. Some of these resources, however, were only for a certain group of users, or required a user’s personal information, as examples. Due to this, LDAP and other legacy directory services, such as Microsoft Active Directory, include a user attributes feature.
Using user attributes, a sysadmin can create a personalized, centralized identity for each of their end users. Some common user attributes include things like first and last name, email/phone number, address, etc. When it comes to using them for authorization, however, these standard profile fields aren’t as quite useful as others. For instance, knowing a user’s employee ID or their department is much more valuable for granting access than their address.
By having a fully fleshed out user attribute system, IT admins could start implementing widespread policies to dictate how user identities should be handled. For example, these policies could allow access to resources for all users in a certain department, restrict privileges for contractors, or any other identity management controls that admins might need. Attributes could also propagate into the applications that users were leveraging, using the information to fill out forms so said user would not have to. The time saving abilities of attributes made them a powerful tool in the admin’s belt.
Future of User Attributes

In the modern IT world, however, legacy directory solutions are falling out of favor. With so many different software-as-a-service (or SaaS) options in the cloud, directory services like AD struggle to keep up with all of them. Some IT admins are using web-application single sign-on (SSO) solutions to bridge the gap.
As if cloud applications weren’t enough, more employees than ever are adopting non-Windows platforms (i.e. Mac and Linux). AD is designed for Windows environments, so the influx of differing systems throw a proverbial wrench in the works of AD’s group policy objects (GPOs). For IT admins who have relied on user attributes and policies for their identity management systems, what does the future of user attributes look like?
User Attributes in the Cloud
Well, many believe that the future of the directory service is a sort of cloud-based directory SaaS. Will these solutions be able to offer the same functionality as the directory services admins are familiar with? For those interested in user attributes and group policies in a modern platform, look no further than JumpCloud Directory Platform.
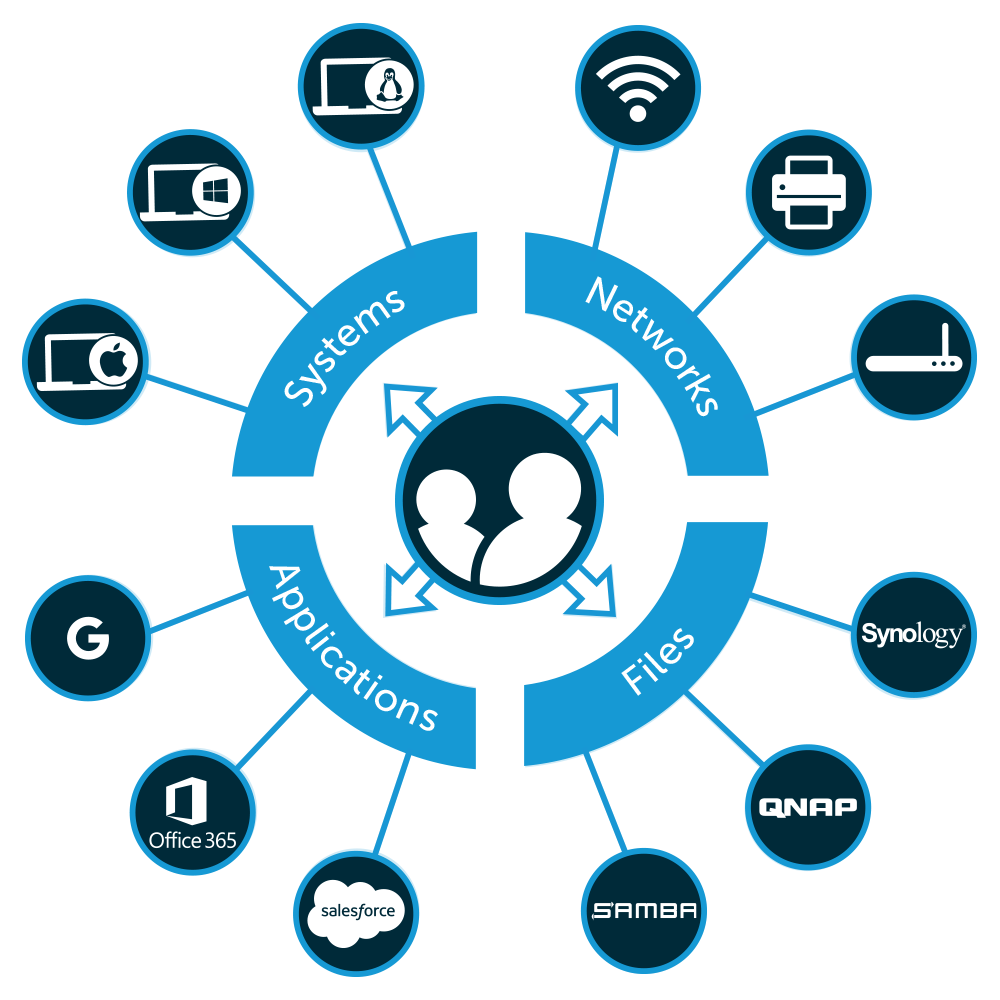
JumpCloud reimagines the functionality of Active Directory in a modern, platform-agnostic cloud directory service. The cloud directory platform utilizes user attributes to create a powerful, unified identity for end users that acts as the source of truth for systems, applications, servers, files, and networks.
Learn More
Contact us or check out our YouTube channel to learn more about JumpCloud’s user attributes feature. You can also see the features firsthand by scheduling a demo. If JumpCloud seems like the solution for your organization, you can sign up for JumpCloud absolutely free. Your first ten users and ten devices are on the house to get you started.




