Identity lifecycle management (ILM) is the act of managing users’ digital identities and access levels from day 1 of their employment all the way through their departure date.
Before we get any deeper into identity lifecycle management (also sometimes referred to as user lifecycle management), let’s back up and define a few related terms: digital identity and identity lifecycle.
What is a Digital Identity?
A digital identity is a cluster of information used across cyberspace that represents an individual person, organization, application, or device. In this article, a digital identity will be specifically referring to that of an individual user.
What is an Identity Lifecycle?
An identity lifecycle refers to the entire process that starts when a user’s digital identity is created and assigned access to resources, and continues with authentication of that identity, updates to credentials and attributes, ending when that identity is retired or deleted entirely.
What is the Identity Lifecycle Management Process?
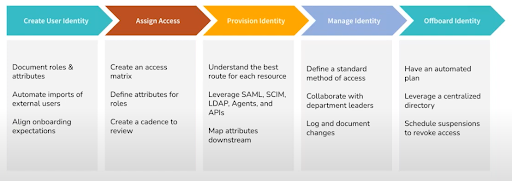
The overarching identity lifecycle management process is simply the management of each of the processes and steps outlined directly above. Essentially, it’s a handful of identity and access related processes that are meant to keep the user behind the identity and organizational resources safe.
To reiterate, those identity and access related processes are:
- Onboarding: Creating a new digital identity and provisioning access to resources.
- Ongoing access tweaks: Changing access levels during role changes or other events in a timely manner.
- Monitoring and reporting: Keeping track of who has access to what, how, and when, to ensure that compliance standards are met and security expectations are adhered to.
- Offboarding: Deprovisioning resource access from a digital identity of a departing employee in a timely manner.
Now that we’ve defined all of the relevant terms that come up when discussing identity lifecycle management, this article will now dig into the following topics:
- The challenges associated with ILM.
- The benefits of using an identity lifecycle management tool.
- The costs of ILM.
- Tools and solutions to help your organization handle ILM.
What are the Challenges Associated with Identity Lifecycle Management?
Identity lifecycle management is not always a straightforward process. Sometimes workflows are not documented or even set in stone, existing tools don’t have the capabilities needed to simplify those workflows, or integral team members have too much on their plate, and things slip through the cracks.
There are many challenges that organizations face regarding ILM, including but not limited to:
- Onboarding and assigning access to a new user in a timely and complete manner.
- Managing contractors and seasonal employees on top of all other internal employees.
- Immediately updating access levels when role changes occur, and avoiding privilege creep.
- Finding time for the IT department to manually manage user lifecycles in conjunction with other priorities.
- Offboarding securely.
1. Onboarding and Assigning Access Efficiently
Many organizations struggle with onboarding new users. A new employee needs access to role-appropriate resources in a timely manner on day one, which can be a big ask when a big class is being onboarded, or HR and IT have conflicting priorities. No matter the reason, when HR and IT are unable to make this a reality, productivity is nearly impossible and the employee experience suffers right from the start.
On top of that, manual onboarding workflows, including identity creation and access provisioning, are time-consuming, especially for growing organizations, and things can often slip through the cracks. A lack of automation across the identity management lifecycle can lead to huge consequences as time goes on.
Further, determining what the correct access levels are for each employee joining the organization can be difficult when that access is assigned individually. Without preset permissions based on role as well as onboarding automation capabilities, this part of user lifecycle management becomes unnecessarily tedious and insecure.
2. Managing External Users
Another identity lifecycle management challenge many organizations face is the management of contractor and seasonal employee digital identities. Sometimes these external or short-term employees don’t exist within your organization’s HRIS tool, but their identity and access still need to be set up, monitored, and eventually deprovisioned in your IT infrastructure.
This divide between the HR and IT software can cause a few different issues as employees and contractors enter and leave your organization. If communication between these two departments is not clear and in-the-moment, identities and the access (or lack thereof) provisioned to them can either cause delays in productivity or create major gaps in security.
3. Adjusting Permissions When Roles Change
People are constantly changing roles at work. Whether it’s a vertical or lateral change, permissions and access will likely need to be adjusted to keep that user productive and secure. The lack of proper identity lifecycle management that many organizations suffer from can result in an employee who has changed roles retaining too much access or not having enough to do their job.
Privilege creep, in particular, is an issue that crops up in many organizations. Privilege creep is the gradual accumulation of access rights that go beyond what an employee needs to do their job. In short, over time, you might find that users have unnecessary access to organizational resources.
4. IT Admin Time Management
Manually setting up, monitoring, and deprovisioning identities and access takes time. Layer on top of that — password resets, permission updates, and addressing access requests, and you’ll find that there’s simply not enough time in the day for IT to get it all done, especially when time is of the essence. It’s not fair to pile manual tasks, especially ones that can be automated with a modern ILM tool, onto the day-to-day workload of IT when there are many other high priority tasks sitting in their queue.
5. Offboarding Securely
The last identity lifecycle management challenge we want to point out is secure offboarding. Earlier we mentioned that onboarding is a significant hurdle in many organizations, and so is offboarding. Improper offboarding poses serious threats to organizational security and compliance, and without proper ILM in place, new security vulnerabilities are likely to pop up. This is typically due to human error and lack of communication between departments, resulting in ex-employees retaining access to company resources after their departure.
Mitigating These Identity Lifecycle Management Challenges
All of these challenges can be solved with the implementation of a modern identity lifecycle management tool that automates processes and integrates with other tools in your tech stack. Let’s get into some of the benefits of using an ILM tool, to showcase exactly how adopting one can improve the entire process organization-wide.
What are the Benefits of Using an Identity Lifecycle Management Tool?
There are many benefits that can accompany identity lifecycle management tools, including:
- Automation capabilities.
- Risk reduction and improved identity compliance.
- Reduced overhead costs.
- Flexible integration capabilities with other useful tools.
The important thing to note here is that not all ILM tools will include each one of these benefits. But, there are ILM tools out there that will provide all of these benefits, and more!
1. Automation Capabilities
Arguably, the most important benefit of an identity lifecycle management tool is automation. This is because automating ILM processes:
- Lessens the number of manual and tedious processes for IT.
- Reduces the chance for human error, thus improving security and compliance.
- Reduces burnout.
- Reduces long-term costs associated with hiring many security and IT professionals to handle manual workloads.
- Enables productivity.
- Improves the employee experience.
- … and more!
Access Automation
A modern ILM tool allows for access automation once an identity is created based on the role and group the identity is associated with. For example, IT adds a new user into their system as a new digital identity, and they place that identity into a group called “Marketing” which has certain resource access related to marketing tasks already provisioned to it. That’s all it takes for that new user to get access to all of those resources!
And later on, when that user departs from your organization, a member of the IT team simply removes their digital identity from that group, and all relevant access is revoked immediately upon removal.
Policy Automation
Another huge perk of an identity lifecycle management tool is automated policy management. Some examples include:
- Setting parameters so employees are required to update their devices within a certain time frame after an update is released.
- Creating stringent password policies, such as how often they need to be changed, how unique they must be, length, etc.
- Setting lockscreen policies that lock devices after a short period of time.
- Blocking the usage of removable storage devices.
These are just some examples of useful policies that can be created in an ILM tool. To further automate, you’d simply have to link these policies to the relevant device groups. The next time that a device is added to that group, the policies associated with it will then be pushed to that new device.
2. Risk Reduction and Improved Compliance
You can probably already see how an identity lifecycle management tool with automation capabilities reduces overall risk and improves compliance. By creating identities efficiently and provisioning access (either automatically or manually) based on attributes associated with that identity, greatly reduces risk that’s inherent in a more frivolous ILM approach.
On top of that, security and compliance can be significantly improved when you use an ILM tool to add single sign-on (SSO) and multi-factor authentication (MFA) as requirements for resource access. The best ILM tools also allow admins to monitor and report on all of this data for compliance audits and security checks. Having a simple way to view what identities exist, what they have access to, and what policies are pushed out to what devices, is all critical for remaining compliant.
3. Reduced Overhead Costs
Implementing a modern identity lifecycle management tool often allows you to get rid of existing single-use products in your tech stack. When the ILM tool you pick has a wide range of functions, there’s no need to continue paying for or managing other tools that are now obsolete in your organization.
On top of that, using your new ILM tool to automate processes frees your IT department up to deal with other important matters that can’t be automated. By consolidating your technology stack and reducing overall IT expenses, you’ll see a much better return on investment (ROI) than you would have otherwise.
4. Integrations with Other IAM Tools
A great ILM solution will allow you to perform lifecycle management tasks in batches across multiple integrated apps, cutting down significantly on the time and money spent managing identity lifecycles across departments.
For example, JumpCloud’s identity lifecycle management platform seamlessly integrates with internal and external applications. Some of those external integrations include popular platforms such as Google Workspace, Microsoft 365, CrowdStrike, HRIS systems (BambooHR, Personio, Namely, Bob, Workday), and others.
What are the Costs Associated with Identity Lifecycle Management Solutions?
The costs of identity lifecycle management without a comprehensive tool in place are:
- A substantial amount of wasted time on manual tasks.
- The monetary costs — both the upfront purchase and ongoing fees — of each one-off solution you use to try to manage identities and access.
- A negative user experience for employees that might cost you new hires.
This can easily add up to thousands of dollars and wasted man-hours spent.
However, the costs of a proper identity lifecycle management solution include:
- Purchasing it up front and any recurring fees.
The bottom line is that the costs you’ll incur by adopting an ILM solution are greatly outweighed by the time-savings you’ll enjoy. Getting rid of all of those unnecessary tools you have will free up a healthy amount of budget!
What are Some Solutions and Tools for Identity Lifecycle Management?
There are a variety of identity lifecycle management solutions and tools that exist to help you streamline the process in your organization. They are often called identity and access management (IAM) tools, identity governance and administration (IGA) tools, user lifecycle management tools, identity lifecycle management tools, cloud directories, or a variety of other names.
Some of these are more comprehensive ILM solutions, while others are partial solutions, but they’re all meant to make the process easier. To wrap up, let’s discuss IGA tools and JumpCloud’s open directory platform that functions as a core directory and comprehensive identity lifecycle management solution.
Identity Governance and Administration
There are different types of identity governance and administration tools — some are comprehensive and are typically used in conjunction with another IAM tool such as a modern directory, while others are built into a modern directory. We’re going to focus on the latter type, which usually looks like a cloud directory with comprehensive IAM functionality and light IGA capabilities, where you don’t need to buy or integrate any extra tools to handle identity lifecycle management.
Some key features of this kind of tool are:
- Streamlined user/identity lifecycle management via automation and grouping.
- Detailed event logging, analysis, and reporting.
- Improved compliance and reduced security risk.
- Scalable processes.
JumpCloud’s Identity Lifecycle Management Solution
One of the most comprehensive identity lifecycle management solutions on the market is the JumpCloud open directory platform. It’s a modern cloud directory, with a wide variety of IAM and IGA capabilities to help you manage, monitor, and secure users’ digital identities and the access that they have.
JumpCloud’s platform centralizes everything you need for proper ILM in a single location, allowing you to remotely manage identities and access on Windows, macOS, and Linux devices. Use it to provision, deprovision, and manage identities using SAML SSO, JIT provisioning, and SCIM, and enjoy easy-to-use, built-in monitoring and event logging capabilities.





