How do security policies become a tangled web? It’s easier than you’d think.
You add a new layer for every threat. A new rule for every edge case.
Before you know it, you’ve got dozens of access policies. They are difficult to manage, prone to overlap, and potentially impact user productivity.
But what if fewer policies were actually more?
A streamlined set of clearly defined conditional access policies makes all the difference. They can genuinely enhance your organization’s security posture.
Security has to exist without complexity. With JumpCloud, conditional access paves the way for a robust, Zero Trust framework that is effective and efficient.
The Problem with Policy Sprawl
Imagine a security guard at a building with 50 different, conflicting rules for entry. Some say show ID, some say biometric scan, and some say “only if it’s raining and you’re wearing a blue hat.” Chaos, right? That’s what happens with too many, poorly designed Conditional Access Policies. With policy sprawl, IT teams struggle with,
- Increased Management Overhead: More policies mean more to monitor, update, and troubleshoot.
- Configuration Errors: Conflicting or overlapping policies can accidentally grant unintended access or cause unintended lockouts.
- User Frustration: Inconsistent access can confuse users and lead to workarounds and new security risks.
- Reduced Visibility: It becomes harder to understand the overall security posture when you’re sifting through dozens of policies.
- Audit Headaches: Proving compliance is a nightmare when your policy logic is overly complicated.
The JumpCloud Philosophy: Smart, Streamlined Conditional Access
JumpCloud’s conditional access capabilities are built to help you simplify without compromise. We focus on key conditions that have high impact. They enable you to build powerful policies that adapt to your user needs without rigid rules.
Here’s how JumpCloud helps you achieve “less is more” with conditional access:
- Focus on Core Conditions (Identity, Device, Network): JumpCloud’s Conditional Access policies are anchored in the three pillars of Zero Trust:
- Identity Trust: Who is the user? (By leveraging JumpCloud’s unified directory and strong MFA capabilities).
- Device Trust: Is the device managed and healthy? (Through JumpCloud’s Device Management capabilities for Windows, Mac, and Linux).
- Network Trust: Where is the access attempt coming from? (By utilizing Named Locations/IP condition.
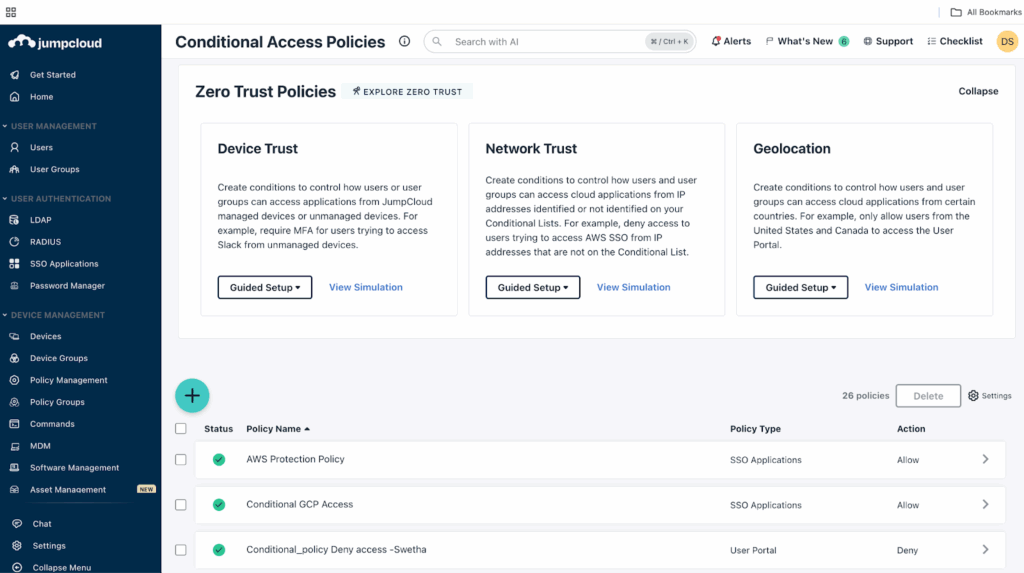
By focusing on these fundamental conditions, you can create a few robust policies that cover a wide range of scenarios. This is better than creating granular, application-specific policies for every situation.
- Intuitive Policy Builder: JumpCloud’s admin console makes building Conditional Access policies straightforward. You define:
- Assignments: Which users or groups does this policy apply to (or exclude)?
- Conditions: What are the criteria (Device Management status, IP address, OS, disk encryption, Managed Chrome Browser/Profile etc.)? For better flexibility, you can also combine conditions with “AND” or “OR” logic.
- Action: What happens if the conditions are met? (Allow access, allow with MFA, deny access).
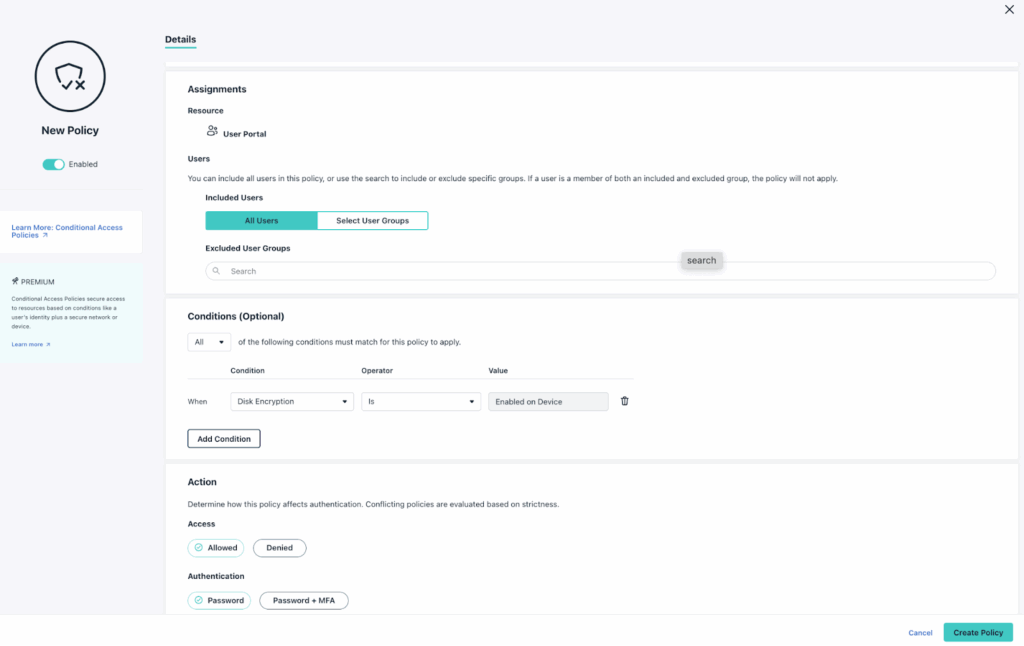
This clear structure helps prevent accidental overlaps and promotes a cleaner policy design. With the latest Google Chrome Enterprise integration, JumpCloud can secure applications on unmanaged devices. You can set the conditions and apply policies directly within managed Chrome browsers or profiles. This ensures your data stays safe wherever your users work.
- Device Trust for Seamless Security: By deploying JumpCloud’s agent and certificates to your devices, you can easily determine if an access attempt is coming from a managed, trusted device. This allows you to:
- Relax MFA for trusted devices: If a user is on a corporate-managed laptop within a trusted network, you might allow access with just a password.
- Enforce stricter policies for untrusted devices: If the same user attempts access from a personal, unmanaged phone, you can require MFA or even deny access entirely.
- Unified Platform for Holistic Control: JumpCloud integrates identity, access, and device management into a single platform. This means your conditional access policies leverage real-time data from your directory, device management, and even privileged access management (PAM) capabilities. You don’t have to rely on complex integrations with different point solutions to streamline your policy management. Instead you can view and manage everything in one place.
The Bottom Line: Efficiency Meets Robust Security
In the race to secure your organization, more policies doesn’t mean better protection. An overload of rules creates unnecessary operational overhead and can introduce new vulnerabilities.
You’re worse off rather than strengthening your defenses.
By adopting a “less is more” approach with JumpCloud’s conditional access policies, you can:
- Minimize your attack surface with Zero Trust principles.
- Improve user experience with adaptive security that prompt for additional verification when necessary.
- Boost IT efficiency with simplified policy creation, management, and troubleshooting.
- Strengthen your compliance posture: With clear audit trails and consistently enforced access controls.
If you are new to JumpCloud, sign up for a free trial today and explore how JumpCloud’s conditional access can streamline your access policies and empower your IT team.




