Updated on August 14, 2024
If you spend enough time in an IT environment and with the rise of cloud infrastructure such as AWS, you will likely come across the term SSH keys. If you’ve already come across this IT term, then you might find yourself wondering, what are SSH keys?
SSH (Secure Shell) keys are an access credential that is used in the SSH protocol and they are foundational to modern Infrastructure-as-a-Service platforms such as AWS, Google Cloud, and Azure.
Before this post delves into an explanation on what are SSH keys, let’s take a quick look at the SSH protocol.
The History of The SSH Protocol
The first version of the SSH protocol was developed in the summer of 1995 by Tatu Ylonen. Tatu was a researcher at the University of Helsinki when a sniffing attack was discovered on the university network. A sniffing attack intercepts and logs the traffic that takes place on a network and can provide attackers with usernames and passwords which can then be used to gain access to critical IT assets.
Thousands of credentials were impacted, including those belonging to community partnerships. This sniffing attack motivated Tatu to figure out how to make networks more secure, and this ultimately led to the creation of the SSH protocol (SSH.com).
Today, the SSH protocol is widely used to login remotely from one system into another, and its strong encryption makes it ideal to carry out tasks such as issuing remote commands and remotely managing network infrastructure and other vital system components. This is especially important in the era of cloud infrastructure and remote work.
To use the SSH protocol, a couple pieces of software need to be installed. The remote systems need to have a piece of software called an SSH daemon, and the system used to issue commands and manage the remote servers needs to have a piece of software called the SSH client. These pieces of software are necessary to create a proper communication channel using the SSH protocol (DigitalOcean).
Essentially, SSH keys are an authentication method used to gain access to an encrypted connection between systems and then ultimately use that connection to manage the remote system.
What are SSH keys?
SSH keys come in many sizes, but a popular choice is an RSA 2048-bit encryption, which is comparable to a 617 digit long password. On Windows systems, it is possible to generate your own SSH key pair by downloading and using an SSH client like PuTTY.
On Mac and Linux systems, it is possible to generate an SSH key pair using a terminal window. Watch the video below to find out how to generate your own RSA key pair on Mac and Linux.
SSH keys always come in pairs, and every pair is made up of a private key and a public key. Who or what possesses these keys determines the type of SSH key pair. If the private key and the public key remain with the user, this set of SSH keys is referred to as user keys.
If the private and public keys are on a remote system, then this key pair is referred to as host keys. Another type of SSH key is a session key. When a large amount of data is being transmitted, session keys are used to encrypt this information.
Now let’s take a closer look at how a private key and public key work. To keep things simple, we will focus on how user keys work.
How User Keys Work
In a user key set, the private key remains on the system being used to access the remote system (i.e. the user’s desktop or laptop) and is used to decrypt information that is exchanged in the SSH protocol.
Private keys should never be shared with anyone and should be secured on a system – i.e. the system is secured (full disk encryption, MFA), in the user’s possession, and the private key is secured via passphrase.
A public key is used to encrypt information, can be shared, and is used by the user and the remote server. On the server end, the public key is saved in a file that contains a list of authorized public keys. On the user’s side, the public SSH key is stored in an SSH key management software or in a file on their computer.
Using SSH Keys
First Steps – SSH Key Generation
Before you can start using SSH keys, first you need to generate your own SSH key pair on the system you would like to use to access a remote system. Please see the instructions below.
Linux/Mac Instructions:
Recommended: Install or Update OpenSSH
sudo apt-get update
sudo apt-get install openssh-server
First, load a command line terminal and type the following command:
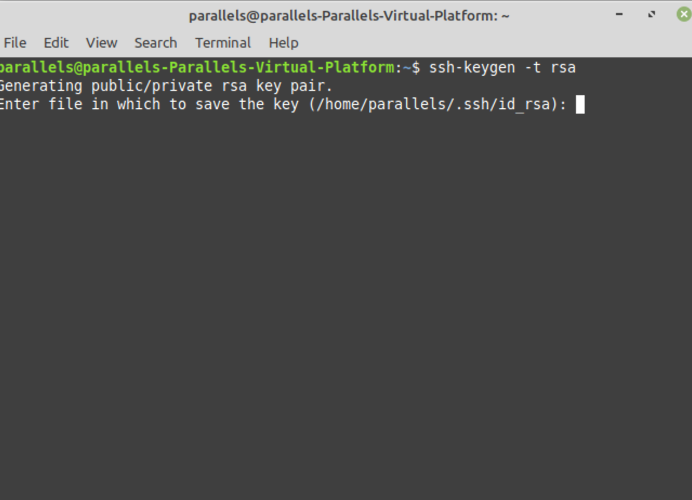
Your two key files will be created in the /HOME/.ssh/ directory by default, including your private key, but you may specify a direct location. Never share your private key.
$HOME/.ssh/id_rsa.pub (public key
$HOME/.ssh/id_rsa (private net)
Per above, you’ll be given the option to set a passphrase to make it more difficult for unauthorized users to log into your accounts by protecting the confidentiality of your keypairs.
Your public key is uploaded to your server to use SSH key authentication for access control. The ssh-copy-id command, which is part of the OpenSSH package, can be used to automate the transfer process in the syntax of:
ssh-copy-id username@host
You may also add the key to your account using JumpCloud, or by manually placing the public SSH key on the remote server (DigitalOcean).

Mac and Linux with CLI – jumpcloud-1
Windows Instructions:
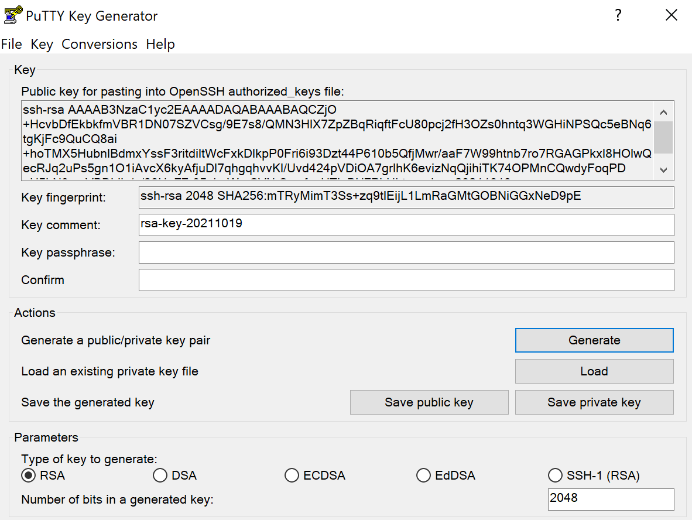
Download and install the PuTTY SSH keygen program.
- Load the PuTTYgen program
- Click the Generate button and select RSA (SSH-2)
- You may opt for a 4096 bit key, but some applications may not accept it and it may result in increased CPU usage during the ‘handshake’ process.
- Key in a passphrase for additional security
- You must select Save private key and specify a location
- Do not share this file with unauthorized individuals
- You can copy and paste your public key from the field above with Select All or hit the Save public key button.
- You may add the key to your account using JumpCloud
Windows SSH Pair Keygen using PuTTY – jumpcloud-1
How SSH Key Authentication Works
After completing the steps mentioned above, use your terminal to enter in your ssh username and the IP address of the remote system in this format: ssh username@my_ip_address. This will initiate a connection to the remote system using the SSH protocol.
The protocol and specified username will then tell the remote server which public key to use to authenticate you. Then the remote server will use that public key to encrypt a random challenge message that is sent back to the client. This challenge message is decrypted using the private key on your system.
Once the message is decrypted, it is combined with a previously arranged session ID and then sent back to the server. If the message matches with what the server sent out, the client is authenticated, and you will gain access to the remote server. This process proves to the server that you have the corresponding private key to the public key it has on file.
However, the security that this authentication process provides can be undermined when SSH keys are not properly managed.
SSH Key Management
Generating SSH key pairs always creates a secret private key that you need to keep secure. Anyone who gains unauthorized access to a private key can immediately compromise the corresponding SSH system.
Why Is SSH Key Management Important?
SSH key management is vital to operational security because SSH keys often grant access to mission-critical digital assets. Keeping track of these keys is not always easy because organizations often have a huge number of individual keys. In fact, it’s common for Fortune 500 enterprises to have several million private keys in their environment.
Despite the difficulty in trying to manually manage millions of SSH keys, having an SSH key management system in place is continuously overlooked. For example, SSH.com did some digging and discovered a company that had 3 million SSH keys “that granted access to live production servers. Of those, 90% were no longer used. Root access was granted by 10% of the keys.” An effective SSH key management system in place would have gone a long way in reducing this concerning security risk.
IT has a couple options to gain control over SSH keys in their environment. One of these includes using an SSH key management tool. However, this means having to manage one more platform in addition to managing an SSO provider, a directory service, and maybe a system management solution.
Fortunately, new options like the JumpCloud Directory Platform provide a streamlined alternative for automating some of the most important steps in SSH key management.
Best Practices for SSH Key Management
Here are three effective ways to improve the security of your private SSH keys:
1. Generate Strong SSH Keys
Passphrases can add randomness and unpredictability to your SSH key pair, making it more secure. They also add an additional layer of protection against unauthorized users.
Passphrase generator tools like Diceware can help you create strong keys that are very difficult to break. You can also create strong keys manually, but you’ll need to create a formula capable of generating a large number of keys.
2. Regularly Review and Rotate SSH Keys
As your organization grows, it will need to secure an increasing amount of information using public key cryptography. If you don’t periodically review access control policies for the keys that secure these assets, they may eventually fall into the wrong hands.
Key rotation policies help reduce this risk by making old keys invalid. The process involves changing the password, regenerating the SSH key pair associated with it, encrypting the private key with a new passphrase, and then updating the public key on the SSH server.
Rotating SSH keys on a regular basis and swapping them makes stealing private keys much less attractive to threat actors. The Windows SSH key application PuTTY supports key rotation as part of its core functionality.
3. Properly Store and Secure SSH Keys
Once you have generated a set of private SSH keys, you must keep them secret. Consider saving them on an encrypted hard drive with very strict access controls. Anyone trying to access this data should provide ample evidence of their authenticity and be able to justify their need for access.
Managing SSH key sprawl is critical to enterprise security because every time you add an SSH key to an account, your organization’s attack surface expands. As the number of SSH keys under management grows, your organization’s SSH security risks will also grow.
Auditing SSH Key Usage
As your organization collects more and more private SSH keys to secure, there will come a time when you can no longer manage them manually. You’ll need to automate the process and then periodically subject that automated process to audit and review.
Monitor and Log SSH Key Usage
Deploying an effective monitoring solution is the first step to securing SSH key usage. When a user or application accesses SSH keys, you need to see who they are and when that access occurred. This data should be logged and kept in a separate, highly secure storage environment.
When the time comes to run an audit, you will review those logs to identify suspicious activities and detect data security policy violations. Not all violations are data breaches, but you should investigate them thoroughly as if they are. Your investigations should provide you with insight you can use to update your SSH configurations and policies accordingly.
Revoke and Disable Unused SSH Keys
Part of your monitoring and logging practices will involve handling inactive and unused SSH key pairs. These keys may provide access to sensitive data and assets, so you can’t simply ignore them.
Instead, part of your auditing process should include systematically identifying, revoking, and disabling keys that are not in use. If you already rotate SSH keys, this process can be automated securely.
Cloud IAM Offers SSH Key Management
Managing large numbers of SSH keys is an impractical and error-prone experience. Growing cloud-based organizations need to deploy identity and access management (IAM) solutions that automate SSH key provision and management.
JumpCloud can help automate the process of creating, securing, and deprovisioning SSH keys from a single centralized access management solution. This makes it much easier for IT administrators and security teams to ensure the organization’s SSH keys are secure, even across multiple platforms and operating systems.
JumpCloud allows organizations to consolidate SSH key management and user authentication to Mac, Linux, and Windows devices, cloud servers, wired and Wi-Fi networks, web-based and on-prem applications, and virtual and on-prem storage.
From the JumpCloud dashboard, deprovisioning users from all of their resources — including SSH key access to remote systems — takes no more than a few clicks. Complex enterprise security teams can even automate SSH key provisioning and deprovisioning directly.
Learn More about SSH Key Management with JumpCloud
You are more than welcome to reach out to us if you would like more information on how the JumpCloud Directory Platform can simplify your SSH key management. If you’re ready to start testing our modern IAM platform, sign up for a free trial.





