Patch Management
Simplified, scheduled, and automated patch management and version control for Windows, macOS, Ubuntu Linux, (Chrome) browsers, and applications.
Full Patch Control In a Single Platform
Patch management is an ongoing, high priority task that deserves clear and simple workflows for admins. With JumpCloud, patch management is easier than ever - use it to simplify your patching process, secure your systems, and satisfy ongoing compliance standards.
Centralized Control
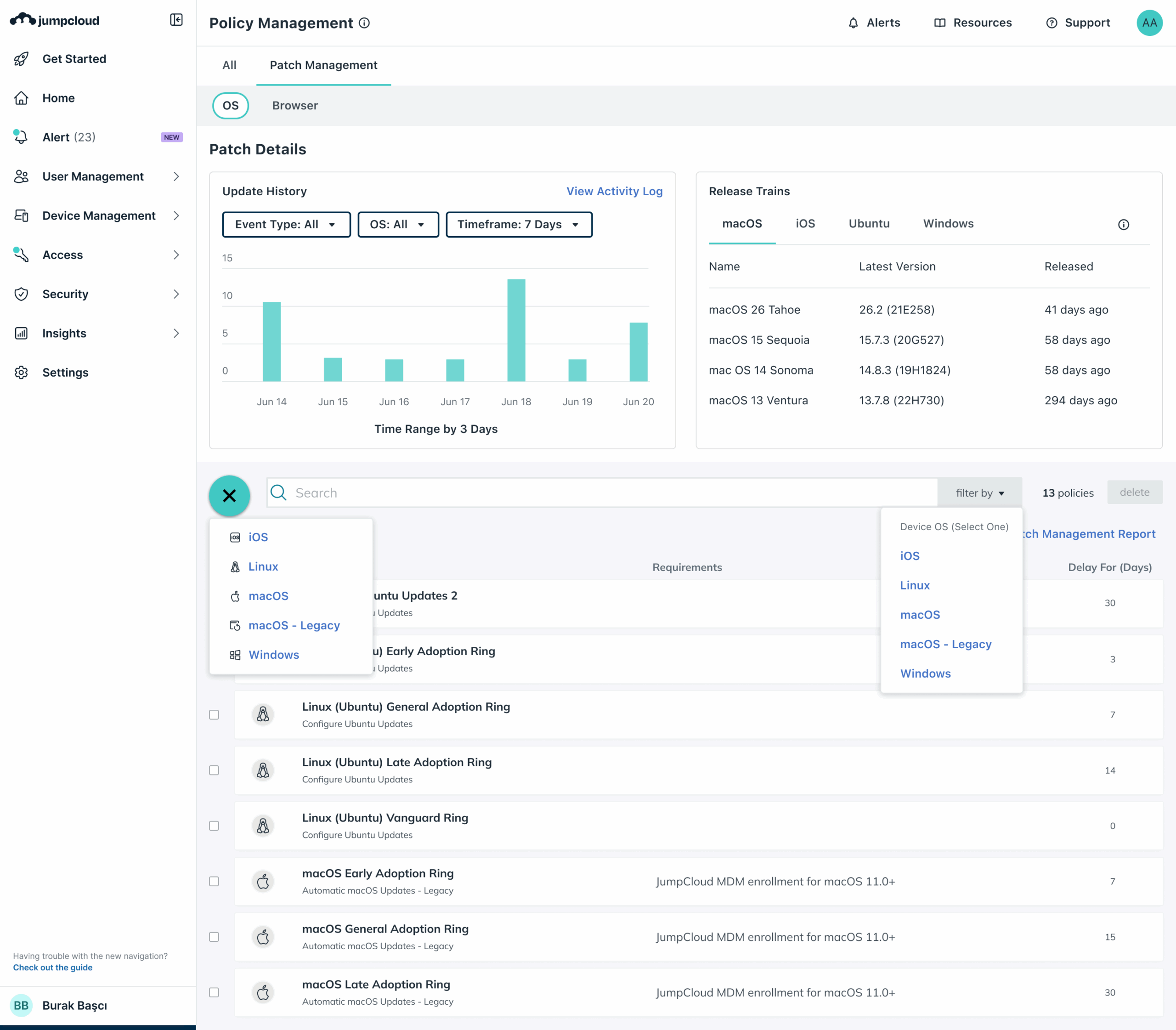
Patching is often fragmented and tedious, especially in diverse IT environments supporting hybrid users. JumpCloud’s unified endpoint management centralizes control and visibility for all of your Windows, macOS, Ubuntu Linux, browser, and application patches in an easy to use tool. JumpCloud also ensures a modern and reliable experience for Apple devices by leveraging Apple’s latest Declarative Device Management (DDM) protocol to deliver native OS patching for macOS, iOS, and iPadOS.
Feature Brief
| JumpCloud Patch ManagementPress Release
| JumpCloud Expands Directory Platform with Patch ManagementSupport Article
| Create a MacOS Patch Policy
Automated Patching
The key to successful patch management is minimizing user impact and maximizing delivery speed. To minimize manual processes, use JumpCloud’s out-of-the-box policies for automatic patching or create your own for a tailored, automated strategy.
Blog Post
| How to Develop a Patch Management ProcessTutorial Blog Post
| OS Patch ManagementSupport Article
| Create a Linux Patch Policy

Simplified Compliance
To meet compliance requirements, having easy access to the right data in a standard format is essential. JumpCloud provides complete visibility and control over operating system (OS), browser, and application patch versions, all from a single console.
Support Article
| OS Patch Management Policy ReportVideo
| The IT Hour: OS Patch Management EditionBlog Post
| How to Not Fall Victim to Browser Vulnerabilities

Explore JumpCloud Open Directory Platform Capabilities
Identity Management
Access Management
Device Management







