Browsers are the gateway to online productivity.
Without them, we would not be able to get work done. To that end, they are also one of the biggest attack targets for bad actors. If we are not careful, and do not make a conscious effort to upkeep web browser security, hackers can easily exploit browser vulnerabilities.
What makes browsers especially appealing to these individuals? Browsers access, collect, and hold lots of sensitive data — from personal credentials to company information — that cyber hackers can sell on the dark web and use to blackmail companies.
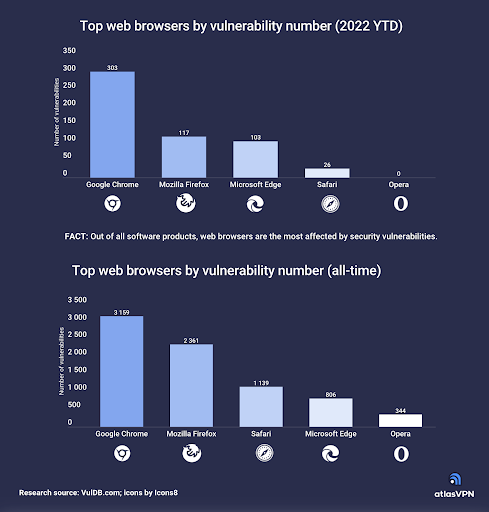
According to Atlas VPN, Google Chrome, the world’s most popular browser, has the highest number of reported (303) vulnerabilities year to date. Google Chrome also has a total of 3,159 cumulative vulnerabilities since its public release.
In this article, we’ll dive into the topic of browser vulnerabilities, the importance of patch management, and how to streamline protection.
A Closer Look at Google Chrome’s Latest Vulnerabilities
On November 8, 2022, the Center for Internet Security (CIS) reported finding multiple vulnerabilities in Google Chrome.
The most severe vulnerability within this group could potentially allow for arbitrary code execution in the context of the logged on user. What does that mean?
Depending on a user’s privileges, an attacker could install programs and view, change, or delete data. The bad actor could even create new accounts with full user rights!
Of course, users whose accounts have minimal user rights on the system would be less impacted than those with administrative user rights.
Multi-OS systems were affected, including:
- Google Chrome versions prior to 107.0.5304.110 for Mac
- Google Chrome versions prior to 107.0.5304.110 for Linux
- Google Chrome versions prior to 107.0.5304.106/.107 for Windows
First and foremost, CIS recommends applying appropriate updates provided by Google to vulnerable systems immediately after appropriate testing. See here for all the other CIS recommended actions.
The Need for Browser Patching
Here are the key reasons you should regularly update or patch your browsers:
- Enhance Security: Prevention of spyware, malware, and other viruses that could give someone access to your data or trick you into handing it over.
- Improve Functionality: Outdated browsers might not work (well) or support new apps or software.
- Boost User Experience: Older browsers usually do not support the latest and greatest code and will have trouble loading component files in the website. This might cause a website to freeze, crash or take forever to work.
For IT admins, security aspects are probably the most important reason to patch browsers. Keeping browsers updated with the latest version (i.e., downloading and installing all provided patches) goes a long way toward preventing cyber attacks and bad actors from exploiting known vulnerabilities.
How to Create Default Chrome Browser Patch Policies
One of the easiest ways to stay on top of patches, and reduce browser vulnerability risk, is to use the JumpCloud Directory Platform.
The latest capability addition to JumpCloud’s Patch Management solution provides a universal policy to keep Google Chrome up to date for macOS, Windows, and Linux.
A universal policy saves time by automatically scheduling and enforcing Chrome security patches on a large number of managed devices.
The platform’s four universal preconfigured default Chrome browser patch policies allow admins to deploy browser updates with different levels of urgency. Admins also have the option to configure a custom universal policy; this feature allows for easy modification of existing policy settings to tailor update experiences to organizational needs.
The four JumpCloud default Chrome browser patch management policies control how and when a Chrome update is applied. The recommended deployment strategies include:
- Day Zero: Deploy automated upgrades inside your IT Department the first day an update is available.
- Early Adoption: Deploy automated upgrades to early adopters outside of IT.
- General Adoption: Deploy automated upgrades to general users in your company.
- Late Adoption: Deploy automated upgrades to remaining users in your company.
Once you have created a Chrome browser patch policy, you can assign it to any devices, policy groups, or device groups. A policy group helps quickly and efficiently roll out existing policies to large numbers of similar devices.
Capabilities of JumpCloud Browser Patch Management
JumpCloud’s new Browser Patch Management also introduces the following features:
- Enforce Chrome updates and browser relaunch.
- Enforce or disable Chrome Browser Sign In Settings.
- Restrict sign-in to a regex pattern to ensure users sign in via company email accounts.
- Automate device enrollment into Google Chrome Browser Cloud Management, which unlocks limitless capabilities for browser and extension control within the Google Admin console.
Dive deeper into the new Universal Chrome Browser Patch Management Release by exploring the release notes for this feature in the JumpCloud Community.
Learn More About JumpCloud
The good news? Browser patching and patch management are included in JumpCloud’s affordable A La Carte pricing package.
Try JumpCloud for free for up to 10 devices and 10 users.
Complimentary support is available 24×7 within the first 10 days of account creation.




