RADIUS servers are a key part of the identity management and user access control process. Historically, RADIUS has been used to manage network access and networking infrastructure. On-premise RADIUS servers have also been used to secure networks through 802.1x port access control and with Wi-Fi networks, but those may introduce additional management overhead and higher licensing costs.
There’s also the potential for security and operational failings. For instance, stand-alone RADIUS servers may result in siloed, non-centralized login credentials that inconvenience end users or require workarounds in order to be interoperable with access control. These setups often exist independent of existing identity practices and infrastructure, which creates security and governance challenges.
Cloud RADIUS Solves More Problems
Cloud RADIUS ensures that all of your users can access critical RADIUS-based resources (such as Wi-Fi and VPNs) seamlessly, while maximizing security and availability, and removing the burden of user and password management from your IT staff.
JumpCloud’s open directory platform makes it possible to bring your own credentials from Microsoft Azure AD via delegated authentication, and you can accomplish even more when JumpCloud is your identity provider (minus the hardware).
For example, includes fine-grained user group management, the ability to access other IT resources through single sign-on (SSO), device management, Zero Trust security controls, including multi-factor authentication (MFA), and logical network segmentation.
JumpCloud’s focus on small and medium-sized enterprises (SMEs) and flexible infrastructure makes it easier to operationalize RADIUS and extend centralized access control without cumbersome server management … or workarounds to integrate with other cloud-based identity providers.
The Case for RADIUS
Let’s first evaluate why RADIUS in the cloud should be a part of your access control landscape. It’s important to establish more than simply a secure network perimeter. Access control that incorporates SSO and Zero Trust security helps to ensure RADIUS is implemented in a manner that secures identities and reduces the potential attack surface area.
Wi-Fi Improves Flexibility and Productivity, Reduces Costs
Modern networks are now moving to wireless infrastructure, and the benefits of Wi-Fi are significant for organizations, including the flexibility and productivity users have in accessing the network. Employees become more productive when Wi-Fi is available, and are more likely to collaborate because they can move around and meet anywhere in the facility.
IT organizations enjoy the benefits of less management overhead and reduced costs of network infrastructure. Unfortunately, password sharing or intermingling guest Wi-Fi access with production may expose your network (and confidential data) to bad actors.
Hackers Can Plug Into Wi-Fi Insecurities
There are challenges to using Wi-Fi, and the main one is its lack of security. Wi-Fi signals often radiate outside the office walls, which helps employees with remote access but enables others to pick up the signal as well. This means that hackers can find a way into the network without physically being in the building.
Wi-Fi security is unlike wired security where you need to uniquely authenticate to have access. A shared passphrase is generally all that is needed to access the network, and that shared passphrase is often rotated as people leave the organization, allowing hackers to glean passwords easily or, even worse, spoof the network’s SSID.
As a result, IT organizations are never fully confident in their Wi-Fi security. When your IT organization begins to fear that the Wi-Fi network might not be secure enough, that’s when to look at using RADIUS.
VPNs and ZTNA Are Vital for Remote Work
Work from anywhere has become an indefinite fixture in many SMEs. Distributed teams expand the talent pool and employees tend to be more productive when relieved of their daily commute. VPNs have been an IT workhorse over the past several years as more employees access internal resources from home.
Cloud RADIUS can improve the authentication process and add additional security elements such as MFA or conditional access policies. VPNs also help to secure information that’s being transmitted during RADIUS authentications. Zero Trust Network Access (ZTNA) is an alternative approach that creates secure boundaries around specific applications. An open directory that seamlessly supports SSO makes it another option.
Cybersecurity Requirements Are More Challenging
RADIUS with MFA may also be mandated by cyber insurance providers. Insurance coverage is denied to organizations that fail to meet stipulated security controls. It’s not uncommon for IT teams to have to integrate network infrastructure, such as switches and firewalls, with their access control solution. Not every RADIUS solution can easily accomplish this. For instance, some solutions require an authentication proxy server to incorporate MFA into the login process.
Connecting Wi-Fi and VPNs with Directory Services
IT admins are connecting their Wi-Fi networks with their directory service to require unique logins for each person. The process works as follows:
- The wireless access points are connected to a RADIUS server.
- The RADIUS server is then integrated with the identity provider.
- A user’s laptop or desktop securely sends credentials to the RADIUS server via the Wi-Fi access point.
- The RADIUS server confirms with the directory server that the credentials are correct. If they are, the user is allowed onto the network. If not, they are denied access.
The user only has to input their credentials into a supplicant on the device once. There is little to no hassle for the end user, and now IT organizations can control exactly who has access to their network versus trusting that nobody has shared the Wi-Fi password with an unauthorized user. They also avoid managing siloed credentials (without modern security controls) to remotely access hardware.
It is clear RADIUS can solve many security and access-related issues. The next section addresses how to implement RADIUS and why cloud RADIUS is the ideal solution.
Self-Hosting RADIUS Can Be a Heavy Burden
When organizations want to access RADIUS resources the traditional approach is to implement a dedicated authentication tool. Some popular options are FreeRADIUS and Microsoft’s NPS. These systems have distinct advantages and disadvantages, but administrative overhead will likely increase. These solutions often require heavy IT intervention and physical servers and are independent of existing identity practices and infrastructure. NPS may even require additional licensing, depending upon how it’s hosted. Either way, your allocations tend to increase.
Stand-alone cloud RADIUS is an alternative option, but generally the solutions do not support delegated authentication via an in-place IdP (such as Azure AD), further fracturing the access control landscape. Attempting integration often introduces an unsupported, custom solution.
In contrast, JumpCloud Cloud RADIUS provides seamless and secure access to Wi-Fi, VPNs, and ZTNAs through established authentication practices and passwords without increasing demands on IT staff. These practices may also incorporate Zero Trust security controls. JumpCloud Cloud RADIUS makes it possible to leverage delegated authentication for Azure AD users. JumpCloud also integrates MFA into the authentication chain so users whose identities reside within the open directory platform can be challenged to provide TOTP and Push MFA responses every time they log in.
Tap Into the Benefits of JumpCloud Cloud RADIUS
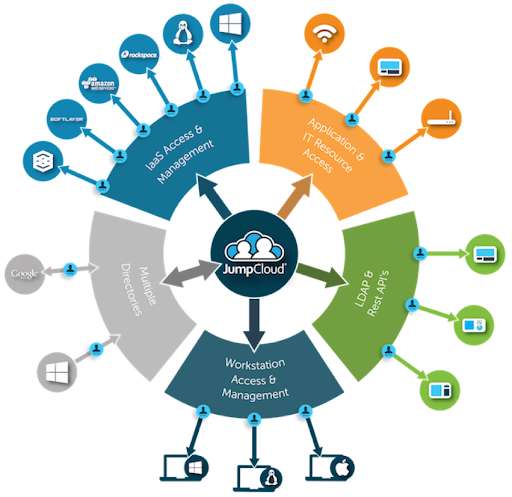
Managing the entire Wi-Fi authentication process can be time-consuming and costly. Hosted RADIUS is a key function of JumpCloud’s open directory platform, delivering maximum scalability and flexibility to deploy, manage, and support dedicated RADIUS servers and device endpoints. The hosted RADIUS server is pre-configured and managed on an ongoing basis by JumpCloud, which extends SSO to other resources and protocols.
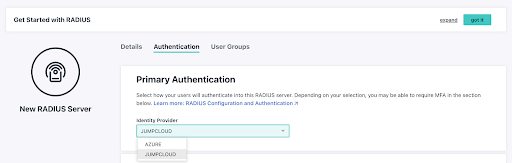
IT organizations simply point their WAPs to the cloud RADIUS server. The directory service is also integrated into the cloud service. The entire process takes a few minutes to set up and enables IT organizations to add a critical security element to their Wi-Fi network.
JumpCloud’s open directory makes unified device and identity management achievable without the typical heavy lifting and burden on IT. IT admins can easily add RADIUS access control, including delegated authentication, to established identity management programs. You access what you want, how you want. There are several other benefits that JumpCloud provides RADIUS users:
- JumpCloud deploys secure EAP-TTLS/PAP protocols and will soon be introducing certificate-based authentication to help achieve a true passwordless experience when accessing RADIUS resources.
- User groups define and enforce the authentication that’s necessary to secure RADIUS resources by roles and attributes. Groups incorporate established policy and identities.
- VLANs segment your Wi-Fi network and secure connections for minimal cost and maximum manageability.
- MFA secures access to RADIUS resources without the cumbersome deployment or heavy management burden of integrating MFA and RADIUS.
- JumpCloud’s applets reside in a user console, adding security against phishing attempts.
Try JumpCloud Cloud RADIUS
If you’re ready to secure your network with a cloud RADIUS server that provides interoperability and Zero Trust security, sign up today for a JumpCloud account. It’s free for up to 10 users or devices. If you’d like additional information, feel free to consult JumpCloud’s Knowledge Base, or drop us a line.



