Technology requirements may seem very different today than during the 1990s, but delivering strong security remains a foundational activity. RADIUS, which dates to that era, is a premier example of a forward-thinking concept for access control. It persists as an authentication, authorization, and accounting (AAA) protocol that is widely used to manage access to network access servers (NAS) as well as Wi-Fi networks. How RADIUS is implemented and managed has evolved to meet stringent security mandates and to support newer deployment models.
There are several options for RADIUS services, depending on your requirements. They consist of open source suites such as FreeRADIUS or the NPS server role for Windows Server. RADIUS may also be deployed as a cloud service that IT admins don’t have to maintain and support. For example, JumpCloud’s Cloud RADIUS services deliver extended security controls and flexibility, without the need for servers. This article explores what RADIUS is, what it does, and how JumpCloud has integrated additional identity and access management (IAM) capabilities that make RADIUS authentication even more dependable.
Why Use RADIUS for Networking?
RADIUS is a core part of the networking world that helps to manage remote access to resources, whether it be a NAS (such as a firewall or VPN) or to authenticate users into Wi-Fi networks.
This functionality has become increasingly important with the proliferation of Wi-Fi in the modern era, because networks are no longer mainly accessed via wired connections. While RADIUS can enable access to wired networks, a side effect of a wired connection is security via proximity (aka physical security).
Secure Wi-Fi and VPN Access
Anyone with a Wi-Fi-enabled laptop can attempt to access the network whether they’re in a vehicle in a parking lot or the next room over. The case for access control to establish perimeter security for Wi-Fi networks is evident, because not every user has good intentions. Every RADIUS user leverages a unique set of credentials to gain access to the network. That means no more shared SSIDs and password combinations found on the whiteboard or word-of-mouth password exchanges. Let’s face it: people talk, and new passwords don’t remain confidential for long. Risks are reduced and visibility into network activities is enhanced.
IT admins gain more control and know who is and who isn’t on the network, which is important for monitoring and auditing access to critical resources. This capability is essential for many IT compliance regimes. JumpCloud layers on additional access controls to help segregate networks using VLAN assignment (virtual local area networks) to logically separate access to sensitive IT resources from basic internet access. A VPN may be similarly organized into VLANs that assign access rights to user groups. It’s advisable to view this as a starting point.
There’s now consensus that perimeter security and single-factor authentication (SFA) aren’t sufficient to protect network resources. The threat environment has intensified and the most recognized cybersecurity consortiums are recommending stronger authentication and following a Zero Trust strategy.
RADIUS Deployments
RADIUS was intended to be easy to customize and has been maintained and improved upon multiple times since its inception. It began under the auspices of Livingston Enterprises in the early 1990s and was later standardized by Lucent Technologies. The protocol then began to gain industry acceptance and vendors developed their own variant(s) using customizations called vendor specific attributes (VSAs) to better fit their use cases. There are several popular options today that can be run on a server or consumed as a cloud service.
JumpCloud RADIUS
As the computing world migrates toward the cloud, companies and their IT admins are searching for ways to implement the best RADIUS server via a software-as-a-service (SaaS) delivery model. That’s because admins realize just how much time savings come from leaving on-prem implementations behind and leveraging a service to provide the functionality they seek.
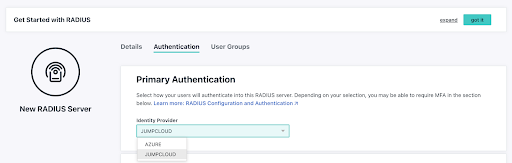
With JumpCloud, IT admins can bring their own user credentials from Microsoft Azure or Active Directory and pair them with JumpCloud’s Cloud RADIUS services for password-based authentication. JumpCloud introduced third party authentication to extend what’s possible with other identity providers. The initial use case is Wi-Fi authentication.
RADIUS has traditionally utilized usernames and passwords, or SFA, to authenticate users against a directory. Users that are provisioned within JumpCloud’s open directory are further protected by layers of Zero Trust security, including multi-factor authentication (MFA) and conditional access rules. These device management rules can restrict access cross-OS, enforce MFA for every login, as well as limit access to specific locations.
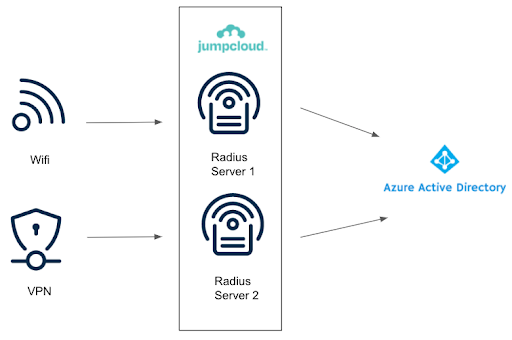
JumpCloud maintains multiple RADIUS servers, delivering significantly higher availability than a single on-premise server that could become a single point of failure. The platform also provides single single-on (SSO), which enables users to log in to their web applications using the same set of credentials for every resource. The JumpCloud User Console features applets for each integration, adding the assurance that users aren’t being phished when they log in.
A similar RADIUS implementation could be possible through assembling various open source technologies or managing cloud instances, but the onus is on administrators to deploy, configure, integrate, test, and maintain systems that provide comparable functionality.
FreeRADIUS
FreeRADIUS is used by over 100 million people on a daily basis, and has been in active development for over 20 years. It has an extremely flexible nature that includes a vast array of configuration options that make it daunting to work with.
In addition, actually implementing FreeRADIUS includes integrating it with a directory service, WAPs (wireless access points), routers, switches, and ensuring that each endpoint is running the proper RADIUS protocol. Administrative tools exist as separate applications. It’s a lot of work, and many IT admins want to save time and money by offloading the tasks to an SaaS provider.
Microsoft NPS
It’s possible to run RADIUS on Windows Server by deploying the NPS role and using domain Active Directory credentials for logins. Microsoft recommends installing NPS on a domain controller to obtain the best performance with network response times. It’s necessary to reboot your domain controller to complete the installation, causing potential network downtime.
Additionally, you may need to order more user or device CALS (Client Access Licenses). Installing NPS on a separate operating system environment will result in higher licensing costs.
It’s then mandatory to perform the requisite server maintenance and configuration steps as well as monitor the server for abnormal behavior or indicators of compromise and install an endpoint detection and response (EDR) system.
Try JumpCloud Cloud RADIUS
If you’re ready to secure your network with a hosted RADIUS server in the cloud that provides interoperability and Zero Trust security, sign up for a trial today. If you need additional information, feel free to consult JumpCloud’s Knowledge Base, or drop us a line.





