Device diversity has been a long-standing issue in the workplace — cross-OS devices, tablets and mobile devices, and personal devices all add distinct layers of difficulty into the device management process for IT. Due to ever-increasing device heterogeneity in the workplace on top of the COVID-19 pandemic and subsequent popularization of remote work, many organizations have been forced to rethink the way devices are distributed and managed.
More specifically, 2021 brought with it a widespread BYOD trend. According to Bitglass, in 2021, 47% of organizations saw an increase in the use of personal devices for work purposes. What’s important about this is that personal devices used for work purposes can’t be managed in the same way as corporate-owned devices.
This trend, and more importantly how we work today, has opened up new challenges (and opportunities) for IT orgs. The key here is to understand what devices exist in an organization, categorize them based on who owns and/or manages them and what their purpose is, and then decide how holistically they can be managed. Mapping all of this out helps you avoid confusion while minimizing unintentional attack vectors.
To do this properly, you need to first gain a full understanding of what device management options exist. This article defines and explains the following device acronyms: BYOD, COD, COPE, COBO, and CYOD. Once you have a clear understanding of the differences between each, you can take the next step in your device management journey by creating policies to manage and secure devices in each relevant category.
Understanding Device Terminology
There are two primary categories of devices used in the workplace: personal devices and corporate-owned devices (COD). What’s more, the COD category can be further broken down into even more specific groups. The variables that differentiate each type of device are:
- Who owns the device?
- Who owns the data on the device?
- Who maintains the device?
- Who pays ongoing bills associated with the device?
- Who owns the phone number registered to the device?
- What capacity is the device used in?
You can use this list in two ways. The first way is to figure out which types of devices are currently used in your organization and create a policy for each. The second way is to use your preferences to answer these questions, figure out which device type is associated with your answers, and choose to only allow that type in the workplace.
Let’s dive into the acronyms associated with each.
What is BYOD?
BYOD stands for bring your own device.
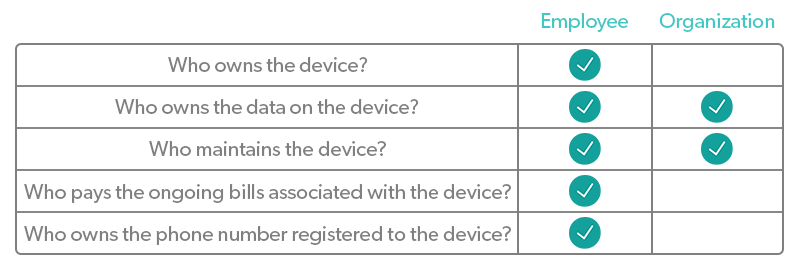

BYOD refers to the trend of employees using personal devices to access work-related systems and resources. These personal devices can be anything from laptops to tablets to smartphones to USB drives and more.
BYOD in the workplace typically requires that you draw a hard line regarding what will or will not be monitored to maintain employee trust. If you choose to install an agent on personal devices to monitor usage, implement conditional access policies, or something else, it needs to be clear what you can see and what you can’t. Monitoring personal use of the device is outside of the organization’s scope.
It’s also important to consider all of the advantages of BYOD, as well as the disadvantages before implementing it in your organization. And, if you choose to allow it, consider narrowing it down (e.g. the only BYOD allowed are laptops — no phones, tablets, or any other non-COD).
Advantages of BYOD
- Flexibility and Convenience: With BYOD, there are virtually no restrictions or limitations on device usage, making it a fan favorite among employees. It’s convenient for users to store everything they need in one place, from a device already in their possession. BYOD is also convenient for organizations that don’t want to deal with the costs and logistics behind providing devices to employees.
- Improved Productivity: BYOD has the fastest deployment time of all device types, because the device in question is likely already purchased and in-use by the employee. This means that users can be productive right away, instead of waiting for a new device to be given to them and configured.
- Device Familiarity: Not only is productivity higher on devices that people are already familiar with, but BYOD also means there’s no training required for the device itself. This saves IT time and resources that they can spend elsewhere and allows users to be productive from day one of BYOD implementation.
- Cost Savings: Typically, BYOD is the most inexpensive device strategy. If you go this route, you won’t have to purchase a new device for each new employee. Service and wireless carrier management costs will also be minimal.
- Happier Workforce: People tend to feel happier when they have choices and flexibility in their work. Providing new hires with the option to use their own devices for work will give them immediate feelings of freedom and familiarity that are then associated with your company. Giving the BYOD option to existing employees might also be the breath of fresh air that they’ve been waiting for.
Disadvantages of BYOD
- Security and Privacy: The primary disadvantages of BYOD revolve around security and privacy concerns. Though BYOD security risks can be mitigated through the use of a unified device management strategy that promotes good security practices and compliance, the idea of an employer monitoring data on BYOD devices can be unsettling for employees. To calm these fears, lay out the details of what information you will monitor and how in a comprehensive BYOD policy.
Shadow IT is another security issue with BYOD. For example, 80% of workers admit to using SaaS apps at work without getting approval from IT. It’s even more likely that those using personal devices will go down this path, because they have the freedom to download and use what they want, compared to using a more heavily configured and restrictive corporate-owned device. - Software Issues: The two main software issues organizations run into in respect to BYOD are software patch management problems and software installation problems. With a diverse fleet of devices that aren’t corporate-owned, it can be difficult to get visibility into patch status and convince users to install patches on BYOD devices, which can have devastating security implications.
Software installation can also be difficult, because the software chosen by the organization might not be suitable for certain systems or the user might experience problems with installation that they don’t know how to solve on their own. - Data Retrieval: Removing data from a personal device can be daunting and difficult if you’re unprepared. To avoid this, include a section in your BYOD policy regarding what happens with company data on an employee-owned device when that employee leaves the company. Employees’ personal data must be protected, so making this process as seamless and non-invasive as possible is ideal.
- Lack of Uniformity: The lack of consistency and uniformity inherent in BYOD can make devices difficult to manage and configure, which can be a burden on IT teams. Some users have brand new devices, while others have devices from 10 years ago, which can make life difficult for IT, even with a strong mobile device management (MDM) system in place.
Supporting every device employees own can also be extremely time-consuming and costly, because it’s impossible to have a specific process in place for each, especially in large companies with hundreds to thousands of different devices. - Distractions: Employees using BYOD devices might experience more distractions throughout the workday because all of their personal apps and resources live on the same device that they use for work. If this begins to affect work performance, it might be time to tell the user they need to change something or ultimately switch to a corporate-owned device.
What is COPE?
COPE stands for corporate-owned, personally-enabled.
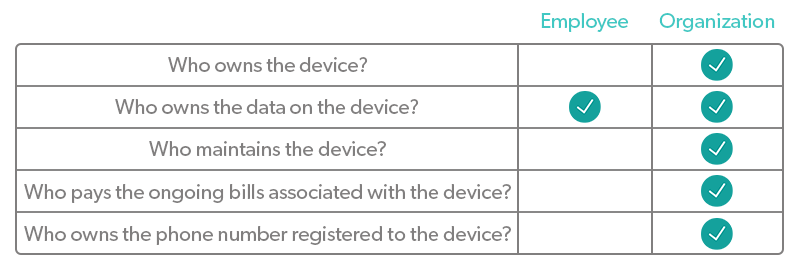

COPE devices are provided to an individual by the organization. They are used primarily for organizational purposes, but the individual is also allowed to use them in a personal capacity. It’s important to note that with COPE devices, privacy can be compromised, as the organization has visibility into everything happening on the device. However, privacy concerns can be mitigated with the proper containerization tools that separate work-related data and personal data.
One example of this is a role that requires the use of a smartphone. A COPE phone allows employees to carry a single phone on them during work hours, rather than two. The phone will be set up with work-related apps and abilities, but the user is able to make voice calls, send texts, check a personal email account, and download personal apps from it.
COPE devices can be a good compromise between a too strict COD policy and a too lenient BYOD policy. However, it’s still important to consider all of the pros and cons of COPE devices before making a decision.
Advantages of COPE
- Significant Control: COPE devices give IT a generous amount of control and authority which lessens the day-to-day burden IT feels when managing devices.
- Secure and Compliant: COPE is a great option for companies with heavy compliance and/or security requirements. The device usage restrictions that come with COPE devices keep users in check and help IT segregate, monitor, and manage organizational data.
- Minimal Personalization: COPE devices allow users to access certain personal resources, which cannot be done on the more restrictive corporate-owned, business-only devices that some organizations use. Though this may not seem like much, it can feel a lot more flexible to end-users than some other options out there.
- Cheap or Free for Users: With BYOD, some employees might feel cheated if they are expected to use their own device for work purposes, because they purchased it on their own and they pay for the ongoing bills associated with it. However, COPE devices come at little to no cost to employees, which can be an important benefit to some.
- Cost-Savings Potential: When you buy the same device in bulk, you’ll find that sizable corporate discounts are available, saving you a chunk of money. This is important to keep in mind if you’re leaning toward a device strategy that’s more restrictive than BYOD.
Disadvantages of COPE
- Limited Usage Capacity: While this can be an advantage for the organization, less freedom on devices is a disadvantage for employees. Plus, if you go the COPE route, you’ll need to implement detailed usage policies that users are expected to follow to keep the device and the data it holds secure.
- Lack of Flexibility: COPE provides users with little to no say in the device they get. While some people might not care, others might be unhappy with the operating system or type of device they’re given. If they’re used to something completely different, there will be a learning curve involved that can hinder productivity.
- Maintenance and Monitoring: Because COPE devices are corporate-owned, the organization is fully responsible for maintaining and monitoring them. This can be a heavy lift for IT, but it does go a long way toward improved security and compliance.
- Can be Costly: COPE devices involve relatively high costs. Purchasing devices for every user in your organization is pricey, but you can often find good deals on bulk orders. The organization will be responsible for device maintenance and repairs in the future, which are added costs to consider.
- Slow Deployment Time: COPE devices have the slowest deployment time frame compared to BYOD, CYOD, and COBO devices. This is because COPE devices are not already in the hands of employees, they must be configured in a very specific way to keep corporate and personal data separate, and then they must be distributed to employees. After that, some employees may need training on how to use the device, especially if they’re used to a different OS or brand.
What is COBO?
COBO stands for corporate-owned, business-only.
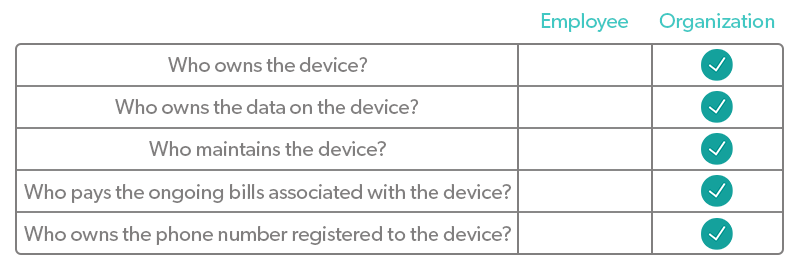

COBO takes things a step further than COPE by prohibiting personal use on the device. COBO devices often come in the form of kiosk tablets, Zoom Room controllers, and other devices that are used by the business at large, rather than by individuals. However, it is possible for individuals to have COBO devices, such as a company-issued smartphone with policies prohibiting personal use.
While COBO devices are great for organizational security and productivity monitoring, they significantly restrict users and remove the user’s ability to to use a single device for work and personal purposes. COBO is an adequate solution for organizations looking to step up security and compliance and/or organizations that lack the ability to keep personal and work data separate.
Learn more about some of the primary advantages and disadvantages of COBO devices:
Advantages of COBO
- Complete IT Control: COBO devices are the most restrictive of all device types, which gives IT total control over how they’re used, monitored, and managed.
- Improved Data Security: This complete control means that policies are easily enforced, improving data security significantly compared to other device strategies.
- Zero Risk of Mixing Personal and Organizational Data: Another reason data security is significantly improved on COBO devices is because there is no risk of personal data and business data mixing, solely because no personal data exists on the device.
- Lower Data Costs: Restricting devices to only hold business data lowers data costs compared to device strategies that allow or even encourage personal use.
- Cost Savings Through Bulk Purchasing: It’s likely that as an organization, you bulk purchase whenever possible to save the most money. Let’s face it — devices are expensive. Buying them, managing them, replacing them, it’s all expensive. So, when you’re able to buy one device in bulk to adhere to your COBO device policy, you can expect to save a lot of money compared to some of the other device strategies out there.
Disadvantages of COBO
- No Flexibility for Users: The elephant in the room regarding a COBO device strategy is its sheer lack of flexibility. This can be a huge deal breaker for employees, so it’s important to fully consider this disadvantage before implementing this strategy.
- Users Have to Manage Multiple Devices: Another related disadvantage is that with a COBO device strategy, employees will need to manage multiple devices which can be frustrating and hurt productivity.
- Organization is Fully Responsible for Devices: The last disadvantage we want to touch on is that your organization will be fully responsible for COBO devices — you will own, manage, and pay for everything associated with them. This con is relevant to every corporate-owned device strategy though; it’s not limited to COBO.
What is CYOD?
CYOD stands for choose your own device.
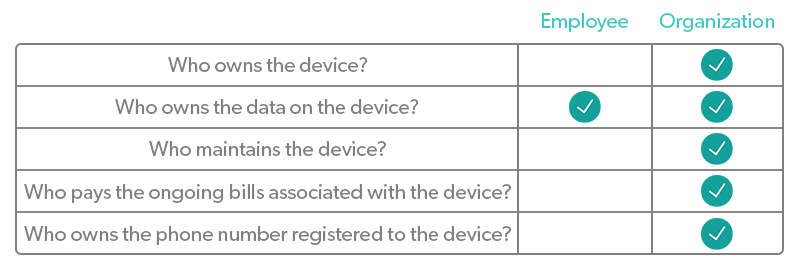

CYOD allows employees to choose from a list of devices specified by the organization. This gives employees more freedom and flexibility to choose the device(s) that works best for them, while staying under the umbrella of device management that IT has already established. This controlled approach keeps support costs low. Support technicians only need to be trained on certain devices, and fewer device types and configurations used means cheaper and easier to support.
In some cases, employees have the option to select and pay for the chosen device, which transfers ownership over to them. This approach is used as a compromise between the traditional BYOD and COD strategies. (This approach is not reflected in the table above.)
Let’s get a little deeper into some of the advantages and disadvantages of a CYOD approach.
Advantages of CYOD
- Some Flexibility and Convenience: Though BYOD provides far more flexibility, CYOD is the runner up in this category. Being able to choose a device (even if it’s from a pre-made list) is a great way to make users feel like they’re in more control of how they work.
- Potential Familiarity: Device familiarity will depend on what spread of devices and operating systems you offer to employees. It’s likely that they will feel drawn to at least one device on your list based on familiarity and experience with that brand or OS. This increases productivity and makes employees feel more comfortable with the device they end up with.
- Streamlined Support and Simplified Management: CYOD provides users with the power of choice, while forcing them to stay within the parameters that IT establishes. Knowing exactly which devices are used across the organization greatly simplifies device management for IT. Plus, support capabilities are widened when the device spread isn’t overwhelmingly large.
- IT Retains More Control: With the CYOD approach, IT maintains control over the devices from the very beginning. The devices are often corporate-owned, so IT can configure them in a way that’s secure and compliant before the device even gets to the end user. On top of that, a pre-made list of approved devices allows IT to proactively create a management plan for each so that no surprises surface later on.
Disadvantages of CYOD
- Limited Device Choices: Compared to BYOD, CYOD gives employees less freedom with device choice. However, compared to the other options of corporate-owned devices (COD), CYOD is much more flexible. This is only a con for users, as CYOD is easier on IT compared to BYOD.
- Semi-Efficient Deployment Time: CYOD involves slower deployment compared to BYOD, but it involves faster deployment compared to other COD strategies. Essentially, CYOD is the option to use when you want to meet employees in the middle without stretching the IT team too thin.
- Upfront Costs: CYOD includes more upfront costs compared to BYOD. These costs include purchasing the devices, getting them to remote users, hardware repair, and sometimes more. However, you might be able to get a bulk discount on devices depending on how many of each you intend to purchase.
Managing BYOD and COD
Use the tables above and the graph below to determine what level of flexibility you want to allow, as well as what level of ownership you want over the devices used in your organization. COPE and CYOD can vary in flexibility depending on the policies you enact, and BYOD can have more corporate control over it with the right device management tool in place.
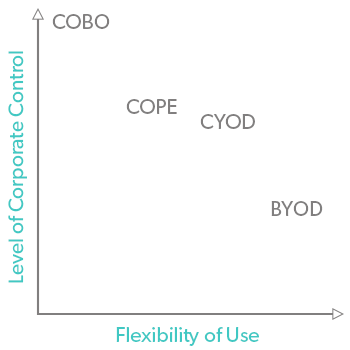
Keep in mind that you don’t just have to choose one type of device to allow. The rules can change from department to department, but don’t bite off more than IT can chew. No matter what direction you choose to go, create specific policies around devices to protect your organization and your employees. Be sure to also put a holistic device management tool in place to ensure that you remain as secure, compliant, and productive as possible, no matter what devices are in the mix.
JumpCloud offers cross-platform device management capabilities: Learn more and try JumpCloud free today.
Frequently Asked Questions
What is the difference between BYOD, COPE, COBO, and CYOD?
BYOD (Bring Your Own Device) lets employees use personal devices for work; COPE (Corporate-Owned, Personally Enabled) provides company-owned devices for both work and personal use; COBO (Corporate-Owned, Business Only) restricts devices to work use only; and CYOD (Choose Your Own Device) allows employees to select from a company-approved list.
What are the benefits of BYOD, COPE, COBO, and CYOD?
BYOD offers flexibility and cost savings, COPE provides control with some personal use, COBO enhances security by restricting personal use, and CYOD balances employee choice with IT management control.
What are the security risks associated with BYOD and COPE?
BYOD poses risks like data leaks, device management challenges, and shadow IT, while COPE can compromise privacy if not managed properly, as the organization may have visibility into personal and work data.
How do organizations manage devices under BYOD, COPE, COBO, and CYOD policies?
Organizations typically create specific policies for each type, incorporating mobile device management (MDM) tools to ensure security and compliance across all device categories.
Which device management model is best for my organization?
The best model depends on your organization’s security needs, budget, and employee preferences; BYOD is flexible, COBO is secure, COPE offers balance, and CYOD promotes choice within a managed framework.




