RADIUS is a core protocol in the management of network infrastructure and Wi-Fi authentication, providing authentication, authorization, and accounting (AAA). The protocol was devised during the dial-up era, but it continues to evolve to meet the requirements of modern small and medium-sized enterprises (SMEs).
How it’s delivered to clients has changed with many organizations opting for the efficiency and security of a cloud-based service over self-managed servers. RADIUS servers remain a viable option for SMEs, but there are a multitude of requisite tasks for its setup and configuration, as well as extra steps for integration with identity stacks.
This article examines each of those deployment options with emphasis on their respective advantages and differences. It also discusses how cloud migrations can deliver additional value to enable IT unification and include RADIUS within a Zero Trust cybersecurity strategy.
What Is Cloud RADIUS?
Cloud RADIUS services are managed by a third party that provides high availability and standards of security compliance that are typically unobtainable by an SME. For instance, JumpCloud has completed independent assessments for SOC 2 Type 2 examination.
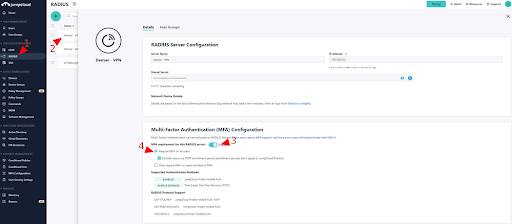
JumpCloud Cloud RADIUS is pre-integrated with directory services and multi-factor authentication (MFA). RADIUS has typically utilized PEAP or EAP-TTLS for authentication without MFA. MFA is a NIST (800-171 compliance) requirement for local and network access to privileged accounts and for network access to non-privileged accounts. In other words, use MFA whenever possible.
Zero Trust Security Controls
The effectiveness of MFA is bolstered by other security controls such as conditional access policies. These policies specify where a client may access resources from, can make MFA mandatory for groups of users, and can restrict access to managed devices. The JumpCloud platform makes these security capabilities immediately available without any additional installations.
It also includes features that manage devices running every major desktop and mobile operating system through Mobile Device Management (MDM) and GPO-like policies. MDM sets up, controls, and manages devices. Patch management is another feature.
Third-Party Identities
The JumpCloud RADIUS service also makes it possible to consume third-party identities via a username and password. This permits users to access Wi-Fi networks with the same credentials that they use everywhere else.
Having built-in options for authentication spares IT admins the difficulty of connecting to an external directory such as Microsoft Azure, which may be unsupported and require custom development or licensing a purpose-built third-party solution. A standalone RADIUS server cannot accomplish this without an associated LDAP server that’s specially configured for Azure AD (or another cloud directory platform).
How Does Cloud RADIUS Work?
IT admins consume and configure a service versus setting up servers. This example outlines how wireless access points are configured to use RADIUS authentication, but the process is the same for every network access server (NAS).
- The RADIUS in the cloud solution is a RADIUS server that is integrated with a cloud directory service. Access may be granted to groups of users within the directory that are bound to the RADIUS connection.
- IT admins simply point their WAPs to the virtual RADIUS server by entering one of its IP addresses.
- Choose to use either PEAP or EAP-TTLS for authentication and determine whether MFA should be required. Admins also generate a strong shared secret that’s kept confidential.
- The RADIUS server then automatically verifies the user’s credentials with the onboard cloud-based directory service.
From the end-user perspective, there is very little to do. The user enters their credentials — those that are used as their core credentials. After that, the user doesn’t need to re-enter their credentials until they change their password.
The user’s device will pass the credentials on to the WAP when they access the network. The WAP automatically forwards the credentials to the RADIUS server and then the identity is validated by the cloud directory.
What Is On-Prem RADIUS?
RADIUS implementations were first developed during the late 1990s and ran on local servers. FreeRADIUS is a popular free and open source example that’s still widely used today. Microsoft’s NPS server role for Windows Server is another option that’s been adopted by many IT admins.
RADIUS servers are sometimes accompanied by IPSec or WireGuard VPNs to ensure that MD5 hashed user credentials and user-specific attributes (such as VLAN memberships) remain confidential. Security is the sole responsibility of the administrator.
How Does On-Prem RADIUS Work?
On-prem RADIUS servers require additional software libraries to replicate the functionality of a cloud RADIUS service. There’s a need to implement FreeRADIUS, Active Directory®, and, often, a bridge between the two. Monitoring, uptime, backups, and security all need to be addressed. A local client might require installation on each device as well.
Microsoft NPS is installed on domain controllers for optimal network response times. It could be installed on another server, but that setup may require that you order more user or device CALS (Client Access Licenses). A separate operating system environment results in higher licensing fees. Federated cloud directory access requires integrations with Azure AD or AD FS.
Differences Between Cloud and On-Prem
Administrators maintain greater control over their environment when they implement RADIUS themselves. However, the administrative overhead is much higher and there’s the potential for a server to become a single point of failure in the authentication chain.
Additional Identity and Access Management (IAM) capabilities and security means purchasing software, standing up other servers, and possibly syncing your on-premise directory with cloud services.
JumpCloud RADIUS delivers security, high availability, and ease of use. An integrated RADIUS and directory service combination allows IT admins to offload the heavy lifting while still realizing all the benefits of RADIUS. And, the cloud RADIUS platform supports the common RADIUS protocols.
Learn more about different RADIUS server solutions.





