A question we’ve heard many IT admins ask is, “Can I move my Active Directory to the cloud?”
This question has become even more relevant due to the ongoing desire of employees to continue to work from home (at least part of the week) on a regular basis. Likewise, some admins want to bring Active Directory (AD) into their cloud resources, because it’s the User Access Management system that they’re most familiar with.
Unfortunately, it’s not that easy to move AD to the cloud, nor have it function properly if you do. Microsoft sought to address this problem by modernizing Active Directory with a prescribed architecture for cloud identity and access management (IAM) and security services. It positions AD as legacy technology that’s “baked in” but vulnerable to attack … without adding multiple Microsoft services. The Entra ID directory service, which extends AD to the cloud, is at the center of it all.
Modernizing AD to support remote workers, all of the devices that they use, and cloud resources can be done without locking you into Microsoft’s expansive new architecture. This article describes how Microsoft says AD can work with cloud environments, but also outlines how you can meet those requirements (and more) with JumpCloud’s open directory platform. JumpCloud syncs/federates with AD and all of the cloud providers where your workloads run.
Check out JumpCloud’s Active Directory to cloud translation guide
You Can’t Easily & Fully Move Active Directory to the Cloud
Let’s examine some use cases for running AD in the cloud. AD can run as a managed service or as infrastructure-as-a-service in a virtual private cloud, which is a private environment that’s isolated within a public cloud. It can solve problems in a familiar way, but keep in mind that AD was never intended to work for the cloud. The approach has numerous pros and cons:
- Pros:
- AD can be automatically configured and managed, from replication and recovery to software updates. Cloud providers will optimize it for cloud workloads such as custom .NET and SQL Server-based apps, or even hosted instances of SharePoint. Cloud platforms that offer AD, such as AWS, make it possible to create a trust relationship with your on-prem AD.
- AD is familiar and many admins believe that it’s faster and simpler to get started with it. It’s something that’s worked for them in the past, so why not?
- You can manage remote users and Windows endpoints without breaking the bank to build out your server room and network hardware.
- Many legacy apps and systems support AD, and it’s tempting to “lift and shift” the resources that you already have into the cloud to avoid refactoring or replacing them with cloud services.
- Cons:
- AD doesn’t provide universal endpoint management (UEM), no matter where it’s being hosted. A Zero Trust security strategy doesn’t separate device management from IAM, and unmanaged devices present a serious security risk because they cannot be verified before they’re used to access your resources.
- Cloud providers operate under a shared responsibility model to address security. Using AD as a cloud IAM solution adds management overhead and risks, because the same problems that exist on-premises carry over to your cloud VM.
- AD doesn’t support single sign-on (SSO) to non-Windows resources, even if it’s hosted in the cloud. It won’t work with web protocols such as OIDC and SAML, and cannot automate user/group authorizations into web apps using SCIM.
- It can’t perform multi-factor authentication (MFA), let alone passwordless modern authentication or conditional access for privileged users. This can place identities and device credentials at risk, same as on-premises.
- It also lacks integrations with other cloud directories and HR systems for lifecycle management. Its classic group management, which was designed for on-premises environments two decades ago, carries over. Modern directory features that automate the identity lifecycle, such as dynamic groups, aren’t available in AD.
- AD must integrate with existing RADIUS infrastructure to access network devices or to be used as a second factor for authentication.
- A modern cloud directory and UEM solution may be more cost-effective for managing users and devices.
- Cloud providers integrate with cloud identity providers (IdPs) with less management overhead and less risk and responsibility for IT infrastructure. AD cannot do this on its own, even if it’s in the cloud.
- Using AD to enable legacy apps kicks the can down the road for cloud migrations and better security practice adoption. That can be a cloud adoption anti-pattern.
We get it. It seems easier to fire up a VM in AWS and use AD to manage your users there. Microsoft publishes a lot of guidance that isn’t followed in real-world IT environments. It can be difficult to keep up with all of those recommendations, and you’ve got other priorities. We suggest that you consider how this approach increases your attack surface area through AD’s server infrastructure and neglects to secure identities with Zero Trust controls. Microsoft isn’t wrong to call out AD’s vulnerabilities, which are well understood and exploited by bad actors. The optimal approach is to avoid the risks without taking on new costs and complexities.
The Microsoft Cybersecurity Reference Architecture (MCRA) no longer considers AD to be a standalone solution that’s separate from cloud services to modernize and secure it. It’s not a matter of if you’re using cloud services to modernize AD, it’s only a matter of when.
Microsoft’s Reference Architecture
Microsoft’s enterprise access model supersedes and replaces AD’s tier model where there’s a logical separation among AD assets within a single domain. The new model spans AD installations, is multi cloud, and includes users from several IdPs. Microsoft’s path to running AD in the cloud always includes Entra ID, in order to extend AD to support cloud apps and remote users. Microsoft recommends that you use Entra ID when you run cloud instances of AD, but its guidance doesn’t stop at access control.
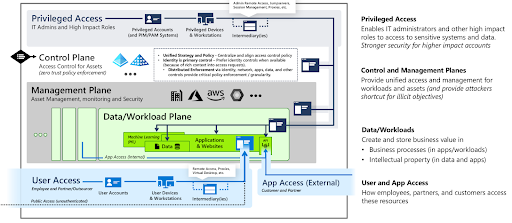
Tiering off domain controllers from application servers and end users systems is a legacy model. This is Microsoft’s new model for enterprise access control. Image credit: Microsoft.
Microsoft services that you’ll need for cloud-hosted AD:
- Microsoft recommends Entra ID Premium 2 to have Identity Protection no matter where AD is being hosted.
- Microsoft recommends Defender for Identity to safeguard AD from lateral movement by attackers and privilege escalation due to its endemic security problems.
- Microsoft recommends Defender for Servers to protect against threats when AD is running in Azure, AWS, or GCP. Microsoft Defender for Endpoints, its endpoint detection and response (EDR), is suggested to have complete threat protection. Another component called Azure Arc is required when your cloud platform isn’t Azure.
- Microsoft recommends Defender for Cloud to manage security posture management for workloads that run on other clouds such as AWS.
Running AD in the cloud may be more than you bargained for, or at the very least, a much more cumbersome way to manage your digital estate. IT admins want the flexibility to choose what solutions are best for their team. This starts with either modernizing AD by integrating it with a cloud directory that has UEM, or replacing Active Directory as the control point.
Gaining Flexibility with Your Directory
JumpCloud’s open directory could be thought of as Active Directory in the cloud that meets modern IT requirements. It’s focused on giving IT admins back control over enterprise IAM by creating a directory that can manage all major systems (Android, Mac, Windows, Linux), cloud and on-prem servers (e.g., AD, AWS, GCP, internal data centers, etc.), networks (Cloud RADIUS), data through physical and virtual file servers, single sign-on to applications (web and on-prem), and more through one central web platform. JumpCloud provides:
- Active Directory Integration (ADI) for your on-premise domains
- UEM for your devices with options for browser and OS patch management
- Dynamic groups for automation and lifecycle management
- OIDC, SAML, a RESTful API for web apps, and a password manager for instances where SSO isn’t a possibility
- JumpCloud Go, a phishing resistant, hardware-bound credential for passwordless logins
- Cloud RADIUS and LDAP
- Environment-wide MFA
- Option conditional access policies
- Reporting and telemetry
Through a unified cloud directory, admins, and perhaps more importantly, their end users have the ability to choose their solutions again.
Try JumpCloud’s Open Directory Platform
Don’t use a legacy on-premises approach in the cloud if you don’t have to. AD raises security risks, increases management overhead, and could potentially lock you into a suite of vertically integrated tools if you follow Microsoft’s recommendations.
If you want to learn more about how you can regain control over your IT infrastructure with a more flexible directory platform, drop us a note or get started with a demo. We’d be happy to talk you through the capabilities and solutions that a cloud directory platform can provide.




