Today, we’re happy to announce that JumpCloud’s LDAP services can now be leveraged to securely authenticate users accessing their digital assets stored on Samba File Servers and NAS appliances. Setup and configuration guidance can be seen in this Knowledge Base Article.
JumpCloud’s update to its LDAP services focused deeply on security in this latest release, ensuring that the required SMB/CIFS authentication transaction between a client host (e.g. Windows) and a Samba-based File Server (e.g. Synology, QNAP or a Linux Samba server) is a protected transaction.
The SMB/CIFS authentication protocol is widely known for its ill-equipped security protections, primarily based on its use of the Windows NT password utilizing MD4 hashing. This was deployed at a time where the Internet (e.g. ‘the cloud’) played virtually no role in IT services, especially authentication and directory services. Today, the Internet plays a major role in IT. However, there is still a wide ecosystem of Linux Samba servers and Samba-based commercial Network Attached Storage (NAS) appliances available and in heavy use. The primary OS requiring SMB is Windows, an OS which composes a large majority of our customer base and thus requires SMB authentication with the Linux Samba server. As a result, JumpCloud pushed deep into the realm of securing the authentication transaction between these on-premise resources to our cloud-based authentication services. The end result of the implementation now enables IT admins to securely map a wider array of resources to a user. This ranges from providing access to the user’s Mac, Windows, and Linux systems, to the networks they need access to, to authenticating their on-prem and web-based applications, and now, with this release, secure authentication to traditional file storage resources.
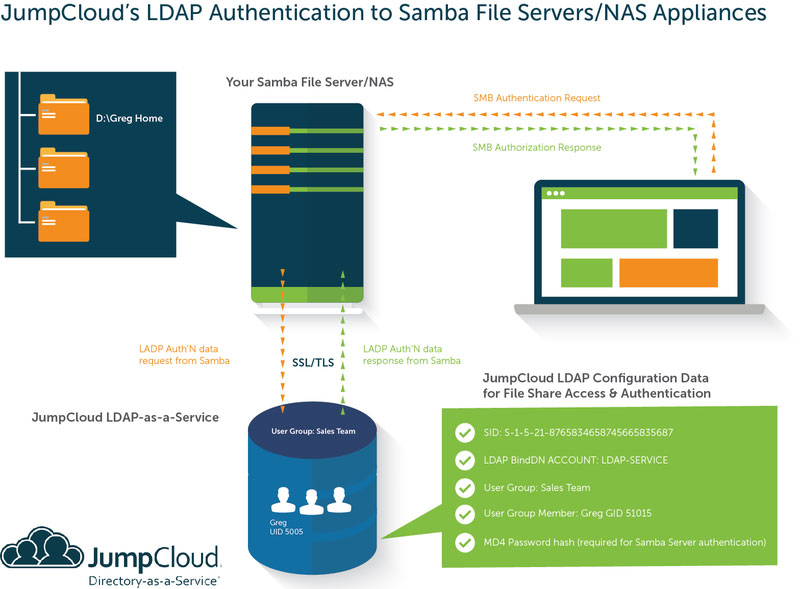
Today’s release announcement focused primarily on our LDAP endpoint, to enable the required Samba/SMB needs while ensuring its security. From a reference architecture diagram perspective, please refer to the following chart to understand the basic authentication flow:
As shown in the ‘Your Samba File Server/NAS’ visualization above, an IT admin will configure the server to have its authentication deferred to an external LDAP directory, instead of utilizing the servers own locally stored user accounts. You can see an example of this utilizing Synology here on our Knowledge Base. JumpCloud’s user object as represented in our LDAP service will contain the appropriate Samba attributes required to complete the authentication request, as shown in the graphic above. The sambaNTpassword is one of these attributes which is conditionally applied for security reasons. To the topic of security, JumpCloud has laid in place numerous layers of protection for the Samba-specific information. These include:
- Samba BindDN: A new class of LDAP BindDN has been introduced in this release. The Samba Service Account will enable one of your designated LDAP Bind DNs to act as the authoritative service account with the only access to search/see the sambaNTPassword data. Other LDAP Bind DNs will not be able to see or gain access to this information.
- Group-based Restriction: Only users in specific User Groups denoted with ‘Enable Samba Access’ will have their LDAP user objects decorated with Samba attributes. Admins must elect to enable this feature and can control exactly who can gain access to file shares requiring Samba data transactions.
- LDAPS / Start TLS Only: JumpCloud will only allow SSL (port 636) or Start TLS (port 389) connections to our LDAP from Samba servers to have the opportunity to access the appropriate Samba attributes. While non-secure port 389 will enable a positive connection between the server and JumpCloud’s LDAP endpoint, it will not be able to return any Samba attributes and therefore will not complete the authentication chain to the workstation.
You may also feel free to review this Whiteboard Video presentation to dive into details of the implementation: