The world is abuzz with the promise of artificial intelligence (AI).
From automating mundane tasks to providing deep business insights, AI is a powerful tool. Companies are jumping on board at a breathtaking pace, and according to the latest data, adoption is at a staggering 99.6%.
But with this rapid embrace comes a dark side. Our Q3 IT Trends Report found that an overwhelming 94% of IT professionals see large risks associated with AI in their organizations, especially its integration with sensitive systems without proper review.
But the key to success isn’t avoiding AI; it’s implementing it securely.
This blog reveals the single biggest pitfall of AI and provides four clear, actionable strategies to ensure you get the reward without the risk. Read on to know more!
The AI Explosion Is Already Here
The days of debating whether to adopt AI are over.
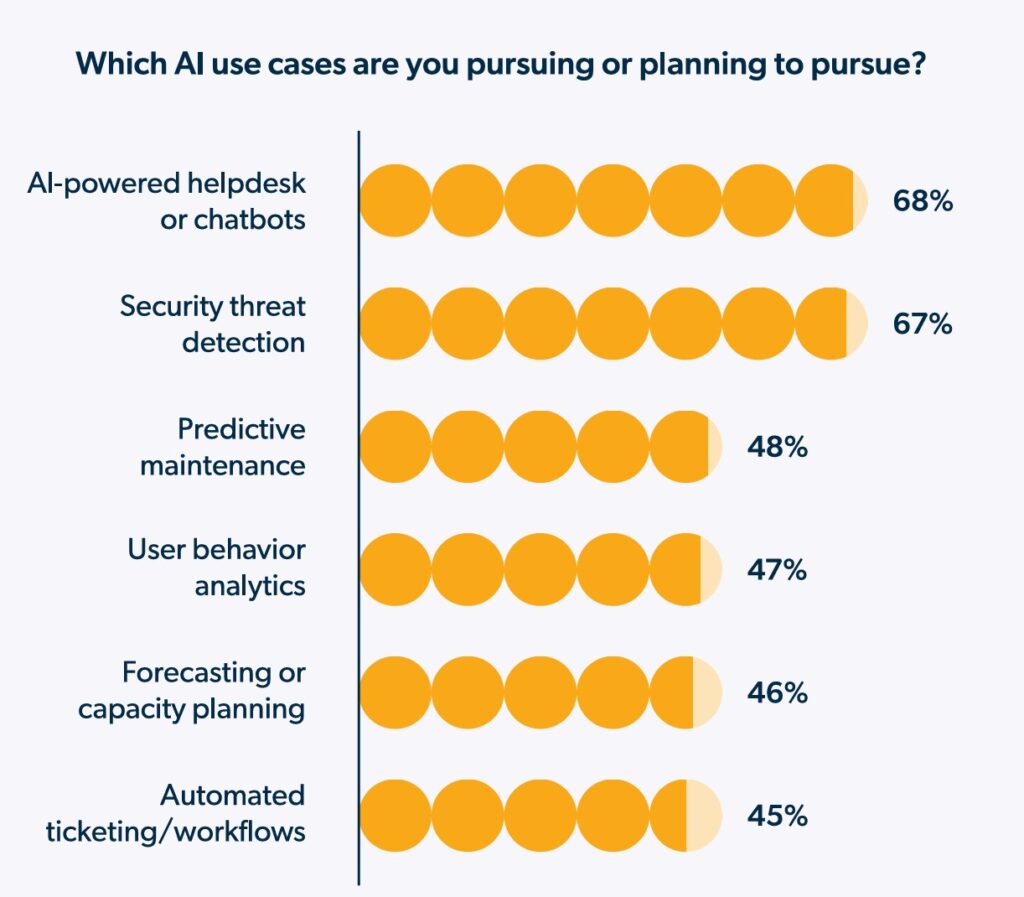
With nearly universal adoption, the question is no longer ‘if‘ but ‘how‘ to leverage this technology. Organizations continue to discover and deploy many practical applications, such as AI-powered chatbots and AI-driven threat detection.
Plus, predictive maintenance and user behavior analytics are helping IT teams to be more proactive and efficient. This explosion of diverse use cases creates a new landscape of complexity.
Without a solid security strategy, this complexity can quickly become a dangerous vulnerability.
The Most Dangerous Pitfall of Implementing AI
So, what’s the biggest risk IT professionals are losing sleep over? There’s one clear frontrunner: AI tools integrating with sensitive systems without proper review. More than half of IT professionals named this as their top concern.
Let’s imagine an AI-powered tool meant to automate simple workflows. If not configured properly, it might get access to sensitive customer data, HR records, or financial reports it was never intended to see.
This isn’t a hypothetical fear; it’s a very real danger that opens the door to data breaches and compliance violations.
This central pitfall is also directly connected to other top risks identified in the study. These include insecure default permissions and the lack of identity governance for non-human actors, which are the AI bots and agents themselves.
Alarmingly, the report shows that less than a quarter of organizations are currently taking action to manage or secure these non-human identities.
Your Four-Step Playbook for Deploying AI Securely
You can’t afford to be reactive when it comes to AI. The solution lies in proactive security measures. Here are four strategies to help you deploy AI safely and effectively:
Step 1: Prioritize Centralized Visibility and Auditing
You can’t secure what you can’t see. That’s why centralizing visibility and enhanced audit trails are a must-have for securing AI. It gives you a complete picture of every action an AI agent performs, identifies, and mitigates any unauthorized behavior.
Step 2: Implement Proactive Governance
This is your direct defense against the #1 pitfall. Clearly define the scope of any AI tool before deploying it and the permissions it needs to function. Following the principle of least privilege ensures the AI only has access to what is absolutely necessary, and no more.
Step 3: Secure Non-Human Identities
Recognize that AI agents are users, too, and you should manage them with the same level of scrutiny as human employees. They need their own managed identities and strict, monitored access controls. It prevents them from becoming a backdoor for attackers.
Step 4: Unify Your IT Architecture
This is the foundational solution that makes the first three steps possible. A unified IT platform provides a single source of truth for managing all your tools—including new AI solutions. It helps cut dangerous security blind spots, ensures policy enforcement, and simplifies securing a diverse, modern IT setup.
It’s Time to Lead with Intention
AI isn’t a futuristic concept anymore; it’s a present-day reality that is actively shaping the modern IT landscape. Securing your AI initiatives is no longer an afterthought—it’s a basic need for success. By grasping the key risks and using proactive security strategies, you can do more than just mitigate danger. You can position yourself as a strategic leader who knows how to safely and effectively use the immense power of AI to propel your organization forward.
This blog has only touched on the latest findings. To get a complete understanding of how IT admins are tackling the challenges of AI, security, and IT architecture, download the full Q3 IT Trends 2025 Report. You’ll get the data and insights you need to make smart decisions and stay ahead of the curve.





