JumpCloud RADIUS gives you the power and security of RADIUS network authentication without the need for physical servers. Learn how to configure OpenVPN Access Server to use JumpCloud RADIUS for authentication.
Prerequisites:
- A configured JumpCloud RADIUS server using the public IP address of your OpenVPN appliance. See RADIUS Configuration and Authentication to learn more.
Considerations:
- When using MFA for RADIUS authentication with OpenVPN:
- Push MFA (JumpCloud Protect) using MS-CHAPv2 is the recommended RADIUS authentication method in the OpenVPN configuration.
- TOTP MFA is not recommended for security reasons. See Authenticate to RADIUS with MFA to learn more.
Configuring OpenVPN for RADIUS Authentication
To configure OpenVPN Access Server to use JumpCloud RADIUS:
- Sign in to OpenVPN Admin Web UI.
- Go to Authentication > RADIUS.
- Toggle On Enable RADIUS Authentication.
- Under RADIUS Server, enter the JumpCloud RADIUS server IP addresses. See JumpCloud RADIUS Server Details to learn more.
Use multiple JumpCloud RADIUS IPs for redundancy.
- Enter the Shared Secret from your JumpCloud RADIUS server. To view the Shared Secret:
- Log in to the JumpCloud Admin Portal.
- Select USER AUTHENTICATION > RADIUS from the left-hand navigation.
- Click to select a configured RADIUS server.
- The Shared Secret is below Server Name. Click the eye to make the characters visible.
- Under RADIUS Authentication Method, select MS-CHAP v2.
MS-CHAP v2 is the recommended authentication method.
- Click Save Settings and Update Running Server.
- Set RADIUS as the Access Server authentication method. See OpenVPN’s Tutorial: Configure JumpCloud with Access Server via RADIUS to learn more.
Testing OpenVPN Authentication
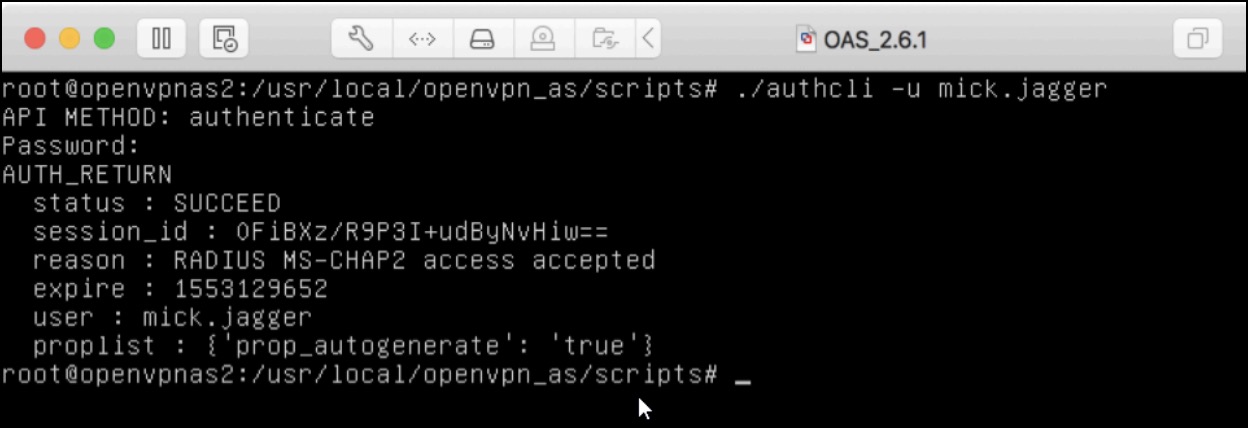
The OpenVPN Access Server provides the command line utility "authcli" to validate your JumpCloud authentication and authorization configuration.
PATH: /usr/local/openvpn_as/scripts/authcli
USAGE: authcli --user JumpCloud_Username
Troubleshooting OpenVPN Authentication and Authorization
For additional diagnostic information, you can enable Debug Level logging in the OpenVPN Access Server 'as.conf' configuration file, restart the service and review the log messages within the default "/var/log/openvpnas.log" file.
$ sudo echo "DEBUG_AUTH=true" >> /user/local/openvpn_as/etc/as.conf
$ sudo service openvpnas restart
When troubleshooting is complete, edit the configuration file to comment out the DEBUG reference, and restart the service to return to normal operation.
#DEBUG_AUTH=true
$ sudo service openvpnas restart
For additional information on troubleshooting authentication and enabling debug level logging, see OpenVPN Troubleshooting Authentication Related Problems (authcli) to learn more.