Full disk encryption (FDE) is a disk-level encryption method that encrypts all hard drive contents including temporary files, swap space, and personal as well as system files. It encrypts data on the hardware level, thereby protecting the operating system and all the data from unauthorized access. This type of encryption is especially useful for laptops and desktops which can be physically stolen or lost. Data remains encrypted, even in the wrong hands.
In Linux, full disk encryption is achieved through LUKS encryption.
What Is LUKS Encryption?
LUKS, an acronym for Linux Unified Key Setup, is a high-performance and secure disk encryption method that offers block device encryption. It is the standard encryption method in Linux used for encrypting entire block devices. LUKS can encrypt any partition including the swap partition.
Full disk encryption protects a block volume in the event of theft or loss of a device. Should your laptop get lost or stolen, the drive remains in the same encrypted state. What FDE cannot do is protect your data if your device is left unattended and already logged into the operating system. You need file encryption for this. File encryption secures specific files on the operating system.
Full disk encryption can only be enabled during installation and not post-installation. Therefore, if you have an OS already installed, you can only encrypt specific block volumes and not the entire drive.
In this guide, we look at how to enable full disk encryption in RHEL 9.
Getting Started
Full disk encryption can only be achieved during installation of an operating system. Ensure that you have a RHEL 9 USB bootable medium before you get started with this guide. Plug it in and select the installation language.
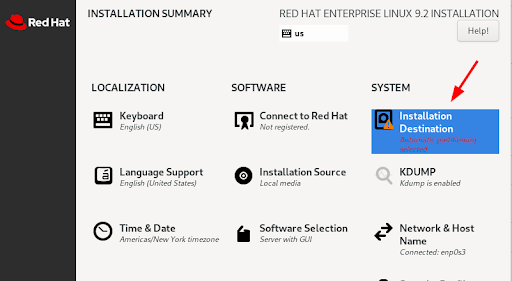
Next, you will be provided with the “Installation Summary” page as shown below. Under the “SYSTEM” section, be sure to select the “Installation Destination” icon.
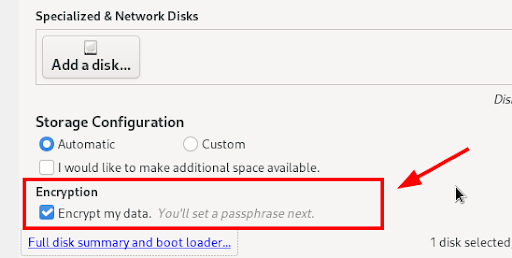
Navigate to the bottom and check the option that reads “Encrypt my data.”
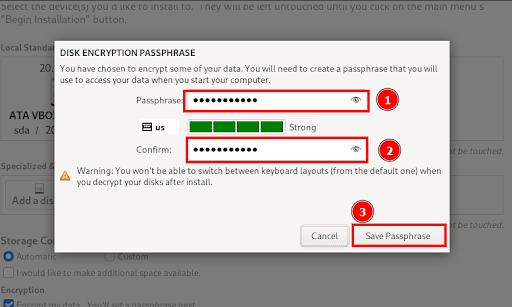
You will be prompted to provide a passphrase. This is the password that will be used to decrypt your hard drive. Be sure to confirm the password and click “Save Passphrase.”
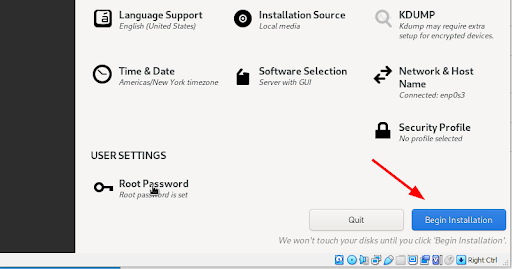
Ensure that all the key parameters are configured. Finally, click “Begin Installation.”
During the installation, the LUKS encryption will be applied to the entire root filesystem.
Once the installation is complete, reboot the system.
Note: The /boot partition may be encrypted if the bootloader supports LUKS encryption. This comes in handy to prevent unauthorized users from tinkering with the Linux Kernel.
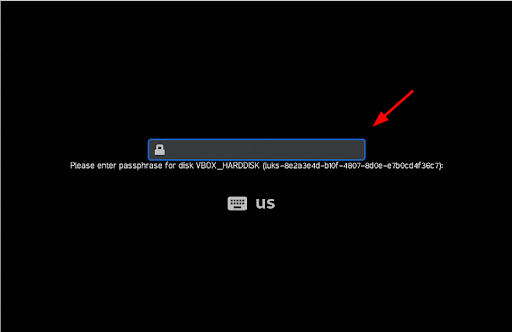
Once the system reboots, enter your passphrase and hit ENTER to continue with the booting process.
Conclusion
LUKS enables full disk encryption in RHEL 9 to secure your personal files or sensitive and/or protected information. FDE offers a reliable means of protecting your data in the event of a lost or stolen device.
Nevertheless, encryption is just one method for maintaining the privacy and security of your data. Be sure to explore additional security measures, including identity and access management (IAM), patch management, and Zero Trust controls such as multi-factor authentication (MFA).
JumpCloud’s open directory platform allows you to implement these measures and more, and ensure that FDE is activated across your entire device fleet. This applies regardless of the operating system, whether your environment relies on Windows, macOS, or Linux distros.
Learn more about how to configure data encryption for Linux systems using the JumpCloud platform, and sign up for free today to get started.



