Offices in prior decades were built primarily with an on-premises state of mind. In order to do work, you had to drive to the office, work on a desktop or stationary computer, and authenticate locally to your on-prem Active Directory® or LDAP server.
Beyond the fact it doesn’t easily accommodate remote work, the on-prem model has other downsides, including forcing admins to manage multiple different passwords for applications and connect their users to WiFi via an unsecured passphrase like WPA2. As technology evolved, cloud applications, varying operating systems, and disparate resources became more common in the workplace, and they challenged the on-prem model as well.
Desktops evolved into laptops, installed versions of applications became web browser-based, and WiFi protocols evolved to become more secure. Offices, too, have started evolving to allow for work-from-home or multiple remote branch offices.
The JumpCloud® open directory platform was built to allow employees to work remotely from home, on the go, or at a remote branch office. This is made possible with a 100% cloud-based directory and secure solutions for the various IT resources at your company’s disposal.
General Security Best Practices
When working in any IT environment, especially environments with remote workers, there are several things you should consider configuring and enforcing. This guidance applies whether you are using JumpCloud or not, so we’ll go through this before going through JumpCloud-specific guidance.
Strong Password Policies:
Different security compliance regulations may require different levels of password complexity. For example, section 8.x in the PCI DSS 3.2.1 compliance requirements recommends the following list be enforced on passwords used in a secure environment:
- Minimum of seven characters, generally 10 characters or more is best
- Numbers
- Lowercase and uppercase
- Special characters (examples: . ! ; _ -)
- 90-day password expiration
- Prohibited reuse of previous four passwords used for the account
- User lockout after six failed login attempts
It should be noted that you can always make these requirements stricter based on the security compliance and policies you want to enforce in your environment. Our advice has alway been and continues to be to create long, strong passwords. Ideally, end users are creating a sentence or combining multiple words together for a long password (greater than 16 characters is always preferable, but note that Office 365 limits passwords to 16 characters).
Anti-Phishing Security Policies:
In recent years, there has been an increasing number of attacks and successful attacks using phishing or spear-phishing. In 2017 alone, according to a PhishLabs report, there was a 237% increase in SaaS app mimic attacks. Beyond that, phishing and pretexting were responsible for 93% of breaches in social attack incidents, Verizon found in one security study. There are many ways bad actors can use social engineering, spam email, or URL redirection to get information out of your employees and into their own hands.
Ensure the safety of your users and your business by enforcing good security practices and taking measures against phishing and other cyberattacks. Create a policy that users must forward suspicious emails to your IT admins or security team, and remind them not to click suspicious emails or URLs. Manage your email with good spam filtering, and regularly check in with employees to assess whether they’ve recently received phishing emails. Continually educate, train, and reinforce your employees’ understanding of the dangers of phishing attacks and how to be secure.
You can also recommend that employees limit their social media use at work, including Facebook, Twitter, and LinkedIn. This reduces your attack vectors and helps in securing your employees’ information and confidential corporate information.
To secure your employees’ identities and thwart attempted phishing attacks, enable local user password resets on the system itself. You can train employees and create a workflow for easy password resets on the system locally, which helps encourage users to properly update passwords and automatically distrust any suspicious password-reset emails.
Beyond educating your employees about good anti-phishing practices and requiring strong passwords, you can enforce multi-factor authentication, keep anti-virus software updated, and use only HTTPS.
System Security Policies:
Locking down your employees’ systems is as important as creating strong passwords for their user accounts. A few of the top policies generally recommended to enforce include:
- Set lock screen for 120 seconds or less
- Disable USB mass storage devices
- Disable CD/DVD drive (if applicable)
- Disable control panel access/system preferences access
- Restrict App Store
- Implement strong password policy
- Configure system MFA
- Disable local guest and administrator accounts
- Turn off AutoPlay
- Disable sharing
- Default users permissions as standard non-admin/non-sudoer accounts
- Enforce full disk encryption
If you want to achieve a higher security standard across your systems, you can reference the CIS Benchmarks for your operating system and leverage those policies too.
Multi-Factor Authentication:
Configuring multi-factor authentication (MFA) across IT resources is a good policy because it prompts users during authentication for something they know (password) and something they have (MFA via Duo, TOTP, or other methods). This creates a secondary required authentication method, which helps lock down systems, applications, and other resources and make access more secure.
Enforcing MFA on systems is a great way to ensure users have both their password and MFA app ready before they’re fully able to log in to secure company resources. You can introduce several layers of security by applying other policies in addition to MFA — like enforcing full disk encryption — to ensure your data and user accounts are safe in the event something happens to the system.
Secure Network Authentication:
It’s highly recommended to move away from using WPA2 shared keys to authenticate to wireless networks. This is a key all users who need to connect to the network share. The passphrase is rarely if ever changed, which leaves the network vulnerable to disgruntled former employees and makes it easier for a bad actor to socially engineer and manipulate their way into getting the shared key from someone in your workforce.
Individualizing secure access to networks can be handled several ways, two of which are common standards: secure LDAP and RADIUS.
RADIUS allows your users to authenticate to the wireless network SSID via their own set of secure credentials. This makes it easier to track and manage who has access to your networks. Secure LDAP is another means of individualizing access, though it’s more common in VPNs than wireless access points.
Full Disk Encryption:
Data encryption is key to meeting virtually any type of compliance regulation. Full disk encryption (FDE) secures the data on systems at the lower levels. It keeps your data safe and secure when at-rest. If a system is stolen but has FDE enabled, an attacker cannot decrypt the data without the password or recovery key.
Both Windows® and macOS® have methodologies to encrypt the disk with utilities native to their operating systems. Windows’ BitLocker and macOS’ FileVault are both great tools to enable and leverage in your work environment.
Recovery Keys should be protected and secured as well. Having them on loose paper or spreadsheet on a shared drive are two ways to fail a security audit. Keeping Recovery Keys out of sight and secure can be done in a multitude of different ways, some better than others.
Many security compliances will require you to store your recovery keys in a secure vault. These vaults could be a physical safe or vault, 3rd party application which securely vaults recovery keys, or securely stored in a directory. You should keep these keys as safe as possible as these recovery keys are the only way to decrypt the disk in a recovery or repair scenario.
No Shared Accounts:
Shared accounts can be a security risk, impossible to audit appropriately, and out of compliance. If you’re currently leveraging shared accounts for any of the resources in your environment, WiFi or otherwise, consider migrating to individual accounts. If you audit your organization and find shared accounts are used widely, you’ll struggle to tell who was accessing resources at any given time.
Secure Application Authentication:
There are thousands of cloud-based applications available on the internet today. Small and medium businesses might be using five to 50 — or more — of these applications across their departments. In tandem with strong password policies, they should enable secure authentication methods backed by protocols such as SAML 2.0.
If you don’t have a central directory or access management platform in use, then it’s more than likely each of your users manages their own passwords, which may or may not meet your security compliance requirements. It’s crucial to centralize access control to these applications to dictate what types of passwords and authentication methods are used, as well as have the ability to suspend access across applications quickly for any reason.
You can also layer MFA on top of single sign-on (SSO) application authentication to increase the security of your cloud applications. We’ll now explain how to put JumpCloud to work to manage remote workers as easily and securely as possible and put these guidelines into practice.
How does JumpCloud help me meet security requirements while allowing employees to work remotely?
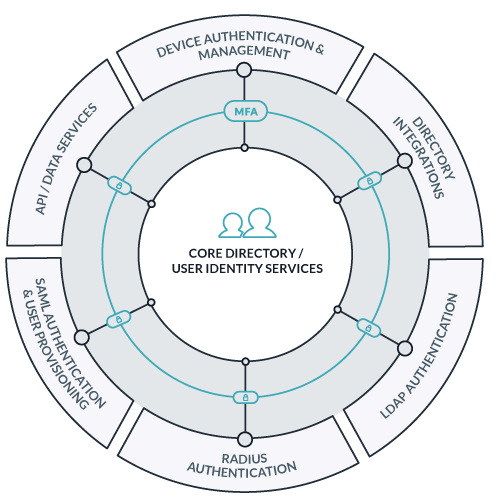
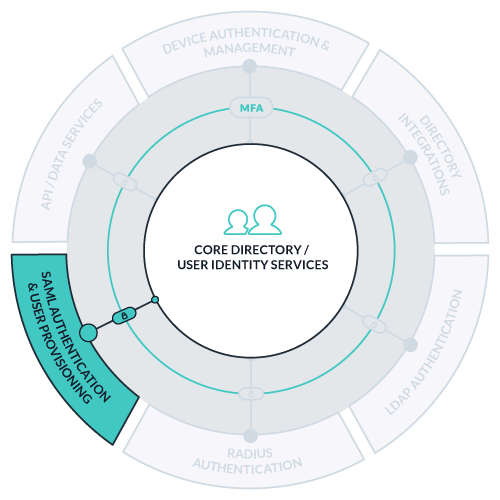
JumpCloud’s cloud directory platform allows you to manage your company’s identities, resources, and systems via an easy-to-use Admin Portal via your favorite web browser. The above diagram outlines the different resources you can connect to JumpCloud’s core directory.
This guide will help cover the following topics to ensure your JumpCloud organization follows some of the basic best practices for enforcing security while working remotely:
- Building the Core Directory
- Setting secure password policies
- Utilizing user and system groups
- Configuring Directory Integrations
- Enabling Multi-Factor Authentication
- System Management & Policy Enforcement
- Change passwords on system
- JumpCloud policies
- Full disk encryption
- JumpCloud commands
- Managing applications with JumpCloud & Chocolatey or AutoPKG
- SAML 2.0 Application Authentication
- Network Authentication
- RADIUS
- Secure LDAP
Building JumpCloud’s Core Directory
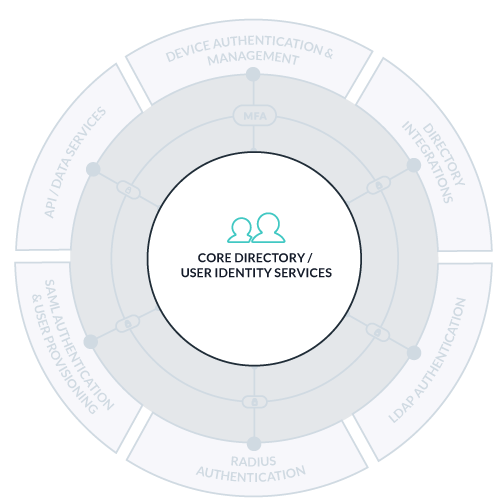
Users are the core of any directory. With JumpCloud, you can ensure users have access only to the specific resources they need, and are blocked from ones they shouldn’t, and follow strict password complexity policies. With JumpCloud, you can also create user groups that allow you to control which users have access to specific applications, systems, file servers, and networks.
Setting Strong Password Policies in JumpCloud
It’s a best practice to configure your JumpCloud organization’s password complexity settings before getting started with creating or importing your users. By creating strong password policies up front, your new JumpCloud users will have to abide by those policies on day one. This way, users only need to set their password once to meet your requirements, and this password will then become their password for all other interconnected JumpCloud resources, systems, and applications.
JumpCloud gives you the ability to configure password policies as you see fit under the Org Settings tab on the left side of the Admin Portal.
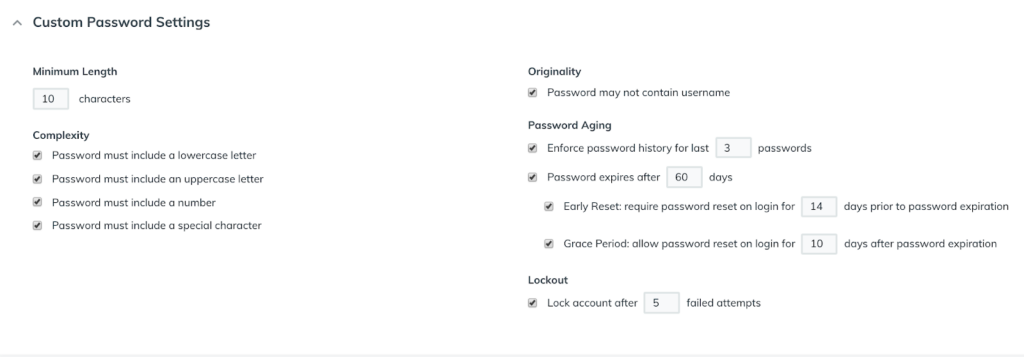
Password settings and Policies are under the User Accounts section within the Custom Password Settings dropdown. Here, you can set the minimum character limit, types of characters required, maximum number of failed login attempts, length of password history, and more.
Creating JumpCloud User & System Groups
JumpCloud User Group Recommendations
User Groups in JumpCloud give you the control as an administrator to configure which users have access to which resources in your JumpCloud organization. Creating User Groups is simple and quick within the JumpCloud Admin Portal. To begin, navigate to the Groups tab in the left menu.

Whether the group is based on department, location, or application need, you can create user groups with a few clicks. If you’re just starting out with JumpCloud, there are no pre-created groups, which gives you the flexibility to create custom groups specific to your organization.
Generally, you’ll want to create an “Everyone” or “All Employees” group. This group will make it easier to control access to different resources the entire company would require, such as the corporate HR application, chat solution, and conferencing application.
User groups can also be bound to RADIUS networks, whether they’re VPNs or WiFi access points. This helps secure your WiFi and the remote worker’s connection with a VPN, which you may already have implemented. Another example group might be “Remote Employees,” to give them access to the secure VPN to use when they work with non-secure or public internet access.
Tip: You don’t need a VPN to use JumpCloud. However, if you have a large user base who travels abroad and might need to use café or other public WiFi networks, then a VPN would be recommended for an extra layer of security.
Leverage Office 365 or G Suite? Using the Directories tab, you can easily sync your JumpCloud user groups with your O365/G Suite directory to consolidate users’ passwords, control user IAM, and provision new users to their target directories.
JumpCloud System Group Recommendations
System Groups in JumpCloud are primarily used for two purposes: User Group access on multiple systems and enabling security policies on systems bound to the System Group.
To create a System Group, navigate back to the Groups tab on the left side in the JumpCloud Admin Portal.

Generally, it’s a best practice to organize your systems into different system groups based on operating system, location, or department. You can easily manage User Group access to multiple systems, such as with DevOps team members accessing multiple Linux servers.
Depending on the operating systems your organization uses, you should create System Groups for each OS. If you use System Groups labeled with their correlating OS, you could then apply the correlating security Policies on each system group. The group model of managing Policies and systems is much easier than configuring each system individually.
Configuring Directory Syncs in JumpCloud
JumpCloud has three primary directory integrations: Office 365 / Azure Active Directory, G Suite, and Active Directory. With these directory syncs in place, you can import pre-existing users into JumpCloud. You can also provision new users directly in the JumpCloud Admin Portal, where they can then be provisioned in the connected directories via bi-directional syncing.

If you’re working remotely or from home, you can use JumpCloud’s singular dashboard to easily import, create, revoke, or suspend user accounts. The User’s workflow is unaffected when logging into Office 365/Azure Active Directory, G Suite, and-or Active Directory. JumpCloud manages the user account and password sync at the API level with these Directories and their connected resources.
Connecting and configuring your current directories in JumpCloud will make it easier for you and your team to manage user accounts remote/abroad.
Enabling Multi-Factor Authentication in JumpCloud
If you’re looking at moving into a more remote or full-time remote work environment, it’s highly recommended to set multi-factor authentication for all users who are accessing your company resources. MFA increases the security of your company’s users and resources because it ensures authentication requires not only a password but also a secondary factor.
JumpCloud has TOTP MFA built into the platform natively. JumpCloud’s TOTP MFA can be enabled on a wide variety of resources connected with JumpCloud, and it’s supported by many different TOTP applications, such as Google Authenticator, Duo Mobile, Authy, FreeOTP, and more.
You can also enable this secondary layer of security on user or admin authentication into their JumpCloud portals.
System Management & System Policy Enforcement
One of the greatest benefits of using JumpCloud is the ability for deep system management and control over user access, system policies, and remote commands on your remote fleet without the need for RDP, VPNs, or SSH. This is all done through JumpCloud’s lightweight system agent. Users can easily change their password natively within Windows using ctrl-alt-del and macOS users can use the JumpCloud Mac App in their menu bar. If you enable users to change their password with common workflows in the OS, you help dissuade users from clicking any suspicious email that asks them to change their password via the web.
The JumpCloud system agent communicates to JumpCloud through secure channels over HTTPS/443, which ensures all updates, changes, removals, and additions to systems are carried out in a secure method. The agent communicates with JumpCloud in a 60-second cadence, meaning any changes you make to the system, bound users, or Policies are all updated within 60 seconds.
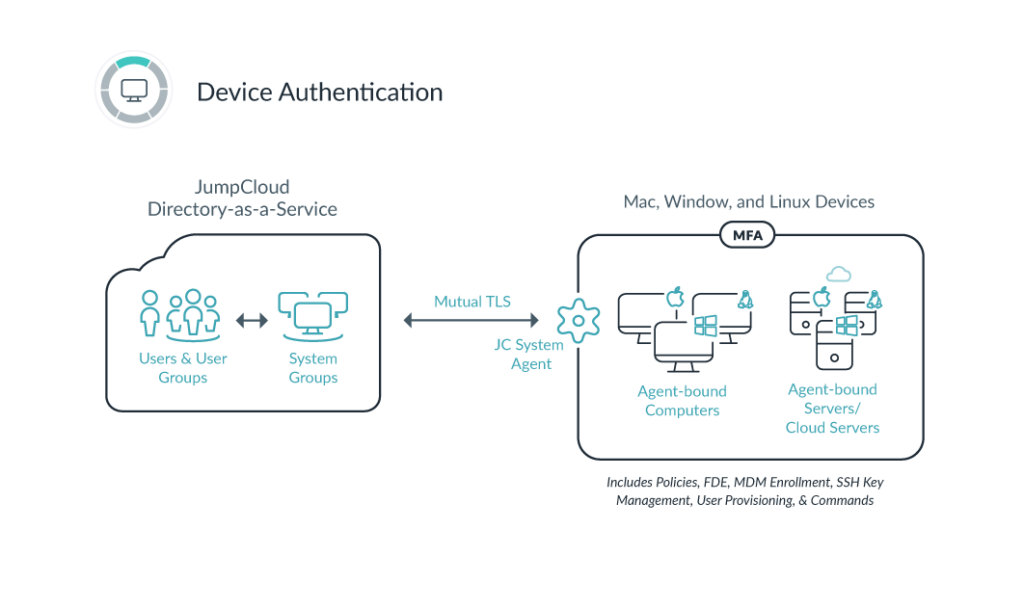
Many current JumpCloud customers leverage the system agent to ensure remote offices, work-from-home employees, and company-owned systems are secure, managed, and following the best practices for security. All system management can be done 100% from the Admin Portal in your favorite web browser.
Need to do something a bit more advanced like custom scripting? Not a problem. JumpCloud also gives admins the ability to write, execute, and schedule custom bash, PowerShell, and command-line commands all from the Admin Portal. These commands could be anything from mapping printers to mounting file shares, or pulling information off a system.
Pairing JumpCloud’s system agent with the premium System InsightsTM feature gives you a much deeper look into the health and status of your systems. You can see installed applications, hardware information, hard disk space, and more for systems — directly from the Admin Portal. This way, you can take inventory of your systems and resources, as well as troubleshoot as needed.
With a few clicks you can ensure your company’s employees have access only to the systems they need, enforce security policies across your fleet, run remote commands, enforce system MFA, and more.
Changing Passwords on the System
As JumpCloud manages systems through the lightweight agent, Users are able to change their password through their logged in session within the operating system. By enforcing password changes and reminders inside of the operating system, users will easily adapt to this already standard workflow knowing to change it locally. Whether your users are using macOS or Windows, they’ll be able to change passwords locally.
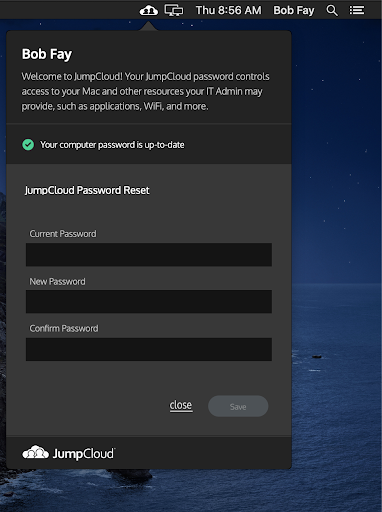
Mac Password Change
Windows Password Change
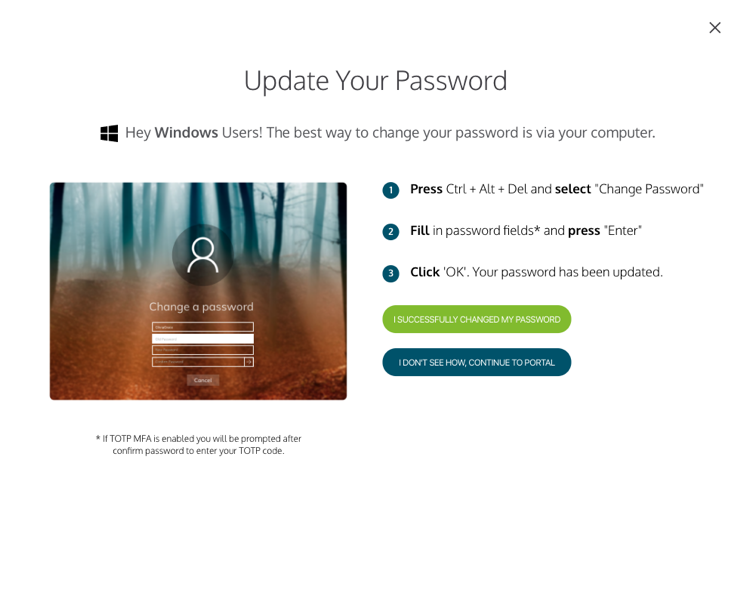
Local password changes can help dissuade users from falling for phishing attacks. Users are less likely to be swayed to change their password if it comes through a suspicious email, knowing it’s changed locally in-system. The ease-of-use and convenience of changing your password locally keeps it easy for the users, but also easier for the admins as reminders, self-serve, and changes can all be done self-serve for the end-users.
JumpCloud System Policies
Built to be vendor-agnostic, JumpCloud allows you to configure system policies for Mac, Windows, and Linux systems remotely. There are many different system Policies you can configure within JumpCloud’s Policy menu. When creating new Policies, we recommend applying them to System Groups, so all associated systems are covered. This can be done within the Policy’s System Group tab.
To get started enforcing good security practices and locking down systems, we recommend configuring and implementing these beginning policies below that were annotated in the first section of this Admin Guide.
- Set lock screen for 120 seconds or less
- Disable USB mass storage devices
- Disable CD/DVD drive (if applicable)
- Disable control panel access/system preferences access
- Restrict App Store
- Implement strong password policy
- Configure system MFA
- Disable local guest and administrator accounts
- Turn off AutoPlay
- Disable sharing
- Default users permissions as standard non-admin/non-sudoer accounts
- Enforce full disk encryption
You can enforce more policies as needed, which is a great way to ensure your work-from-home users’ systems are as secure and locked down as possible. It’s also recommended users are set to “standard user” when you bind users to systems. You should only give sudo/administrator-level permissions to users who require it, such as developers and administrators.
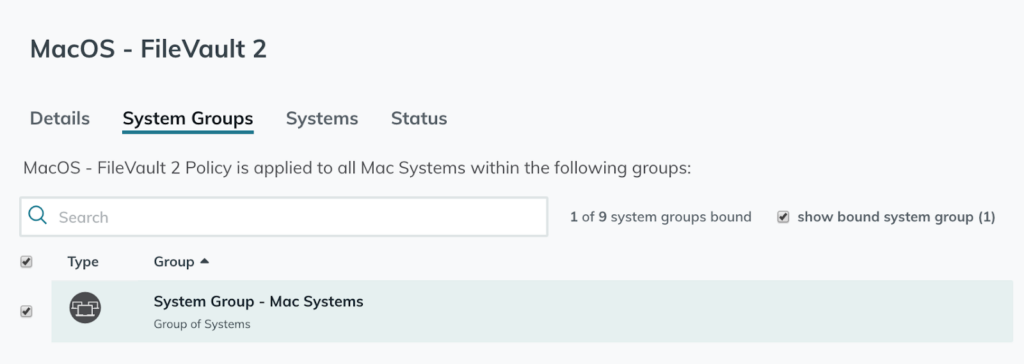
Enabling Full Disk Encryption on JumpCloud Systems
If you’re running Mac and/or Windows systems in your JumpCloud organization, you can easily enable full disk encryption via JumpCloud Policies: Create the BitLocker (Windows) or FileVault 2 (macOS) policy within the Policies menu in JumpCloud and apply it to your JumpCloud “Windows System” and “Mac System” groups to fully encrypt the disks.
Once the Policy is applied, the recovery key is securely escrowed into JumpCloud and appended to the system. The recovery key can be viewed through the “Show Recovery Key” link within the System’s Details tab. If you already have FileVault 2 or BitLocker enabled before JumpCloud, JumpCloud cycles the key and escrows the new key into JumpCloud.
This way, you don’t have to manage any spreadsheets, sticky notes, or other legacy means of managing your recovery keys — and the whole process can be done 100% remotely and easily through JumpCloud’s Admin Portal while being highly secure.
Full disk encryption enforces strong methods built in natively within Windows 8.1/10 and macOS 10.13.6 or higher. If the system were to be lost or stolen, you have the assurance the data on the disk is safe because of the JumpCloud FDE policies applied to the systems. Only the user or admin can decrypt the volume, and the recovery key is only available to view for JumpCloud admins through the Admin Console.
Generally, if the system travels outside of the office, including in remote work scenarios, it’s highly recommended to enforce full disk encryption. This way you are implementing security at the lower levels on the disk and the laptop is secure-at-rest. Check out JumpCloud’s guides on full disk encryption for BitLocker and FileVault 2 for more details.
JumpCloud Commands
If you’re looking for more granular control or the ability to run scheduled tasks, JumpCloud gives you the ability to configure commands for Mac and Linux® (Bash) and Windows (PowerShell or command-line). These commands are remotely executed on either singular or multiple systems, all backed by the JumpCloud agent. To get started, navigate to the Commands tab in the left menu in the JumpCloud Admin Portal.
In a work-from-home or remote work environment, you can pull system or user information on the system using these remote commands. If you leverage JumpCloud’s System Insights, you can do this natively within the Admin Portal.
JumpCloud has a commands gallery on GitHub, so you can copy and paste example commands. These are basic commands to get you started, but if you’d like to write your own custom commands or tasks via Bash or PowerShell, you have the possibility to do so, all from the Admin Portal in your favorite browser.
Managing Applications with JumpCloud & Chocolatey or AutoPKG
Although JumpCloud does not function as a system’s application manager, it can pair with third-party, open-source package managers such as Chocolatey for Windows systems and AutoPKG for macOS systems in your JumpCloud environment. This is done leveraging JumpCloud’s Commands in the Admin Portal.
Managing Applications with Chocolatey with JumpCloud Commands
For Windows systems, using Chocolatey is straightforward and simple. You can install Chocolatey remotely and then begin to provision applications to your users’ systems remotely through JumpCloud. For example, if you want to install Notepad++ or Chrome, you can use the following two lines in a JumpCloud command once Chocolatey has been installed.
choco install googlechrome -y
choco install notepadplusplus -y
With JumpCloud Commands, you can also call Chocolatey to update Chocolatey-managed applications on a specific schedule, such as everyday at 0500 UTC as shown in the following example.
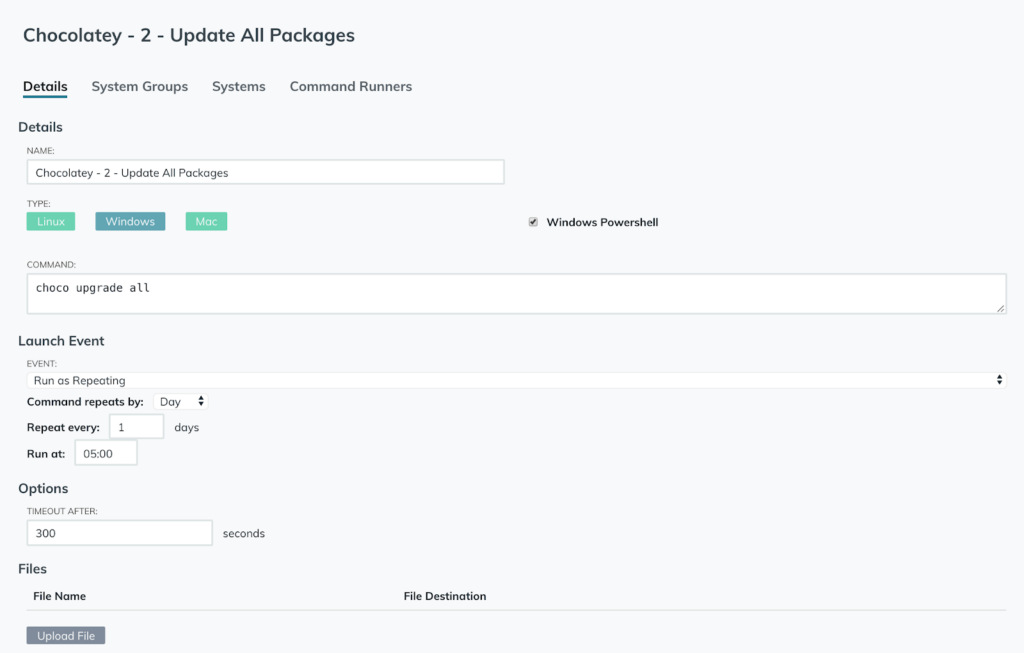
This allows you and your IT admins to ensure the appropriate applications are installed and available for your remote workers, even though your users might be standard users within Windows. Chocolatey’s open repository has more than 7,000 applications in their public list, and they continually update what’s available.
Although JumpCloud doesn’t natively manage the installed applications on Windows, it acts as the vehicle to pair with Chocolatey’s package manager to help consolidate your administrative tasks in JumpCloud’s Admin Portal.
Managing Applications with AutoPKG with JumpCloud Commands
For macOS systems, JumpCloud Commands can be paired with AutoPKG to help manage and install applications remotely on the macOS systems in your company’s fleet.
Once AutoPKG has been installed, you can then create specific JumpCloud Commands which will use AutoPKG to deploy applications across your macOS fleet. To leverage AutoPKG to the fullest, you’ll want to ensure your environment has the appropriate requirements in place. For example, if your repository has the latest version of Firefox, you can install it across your systems using the following AutoPKG recipe:
autopkg install firefox.install
By combining both solutions, JumpCloud and AutoPKG, you can create application installs and updates for your macOS environment without needing your macOS users to have sudo privileges. Although JumpCloud isn’t a full application manager, like with Chocolatey, it acts as the vehicle for AutoPKG to do its magic.
SAML 2.0 Application Authentication with JumpCloud
Most companies use a catalog of web applications, such as Slack, Zoom, Salesforce, AWS, GitHub, and more. In most scenarios, you can access these applications from anywhere in the world, as long as you have internet access. JumpCloud was built in the same way of being 100% cloud-based.
JumpCloud allows you to configure SAML 2.0 application connectors for SSO to the resources your company uses. There are hundreds of pre-configured connectors for applications in JumpCloud’s catalog, with Just-in-Time provisioning for select apps, as well as a generic connector for applications not already pre-configured.
By leveraging JumpCloud user groups, you can associate specific application access only with the groups that need those applications. As seen in the example below, Group 1 has access to Box, AWS, and Zendesk, but does not have access to Slack, Salesforce, or Atlassian Cloud. Keep in mind, JumpCloud users can be placed in both Group 1 and Group 2 to gain access to both sets of resources, depending on the requirements and use cases.
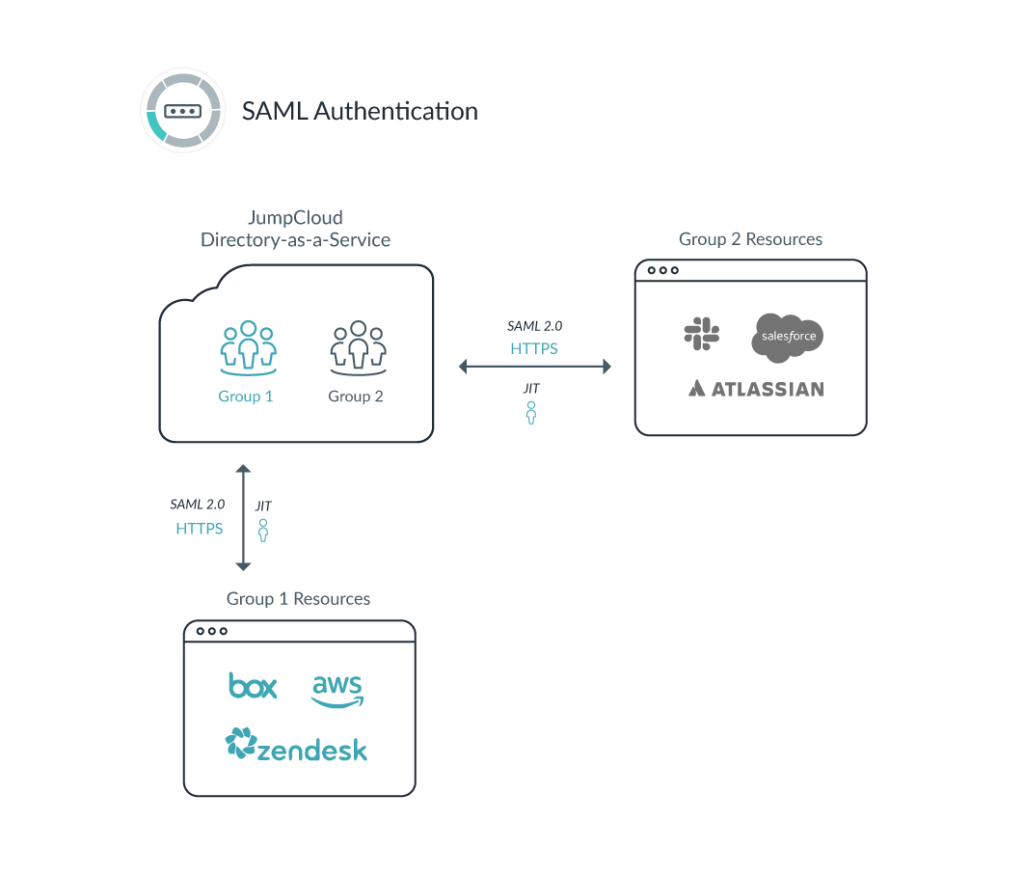
With this workflow, JumpCloud becomes the identity provider to the SAML application (otherwise known as service provider). JumpCloud users can then access the applications they need through the JumpCloud User Portal. This allows access to all of their cloud-based applications using their individual, secure credentials for JumpCloud.
You can easily control all your company’s applications, enforce MFA on SSO Apps, and manage user access all from a single pane of glass with JumpCloud’s Admin Portal. With JumpCloud, you’ll gain assurance all application access is secure for all employees, even those who are working from home or remote.
Network Authentication with JumpCloud
If you’re currently using either WiFi, firewall, or VPN, you can point your network resources to JumpCloud for authentication. There are two main methodologies when connecting networking hardware to JumpCloud: RADIUS and secure LDAP.
Both of these authentication mechanisms help secure your network, as well as the traffic by your users. Enabling a VPN for remote workers, though not mandatory with JumpCloud, is a great way to ensure your employees’ traffic is encrypted through your company’s VPN tunnel.
In this scenario, remote employees launch the VPN client and connect to your company’s VPN by authenticating using their JumpCloud username and password. The authentication request is then sent to JumpCloud to ensure they have the appropriate credentials and rights to gain access to the VPN.
Again, just like all other modules in JumpCloud, you can enable this remotely through the JumpCloud Admin Portal.
Network Authentication via JumpCloud’s RADIUS-as-a-Service
You can also easily work with the networking gear your company is already using by pointing either your VPN or wireless access points to JumpCloud’s RADIUS servers. JumpCloud will then handle all network authentication to the specified network via the RADIUS protocol.
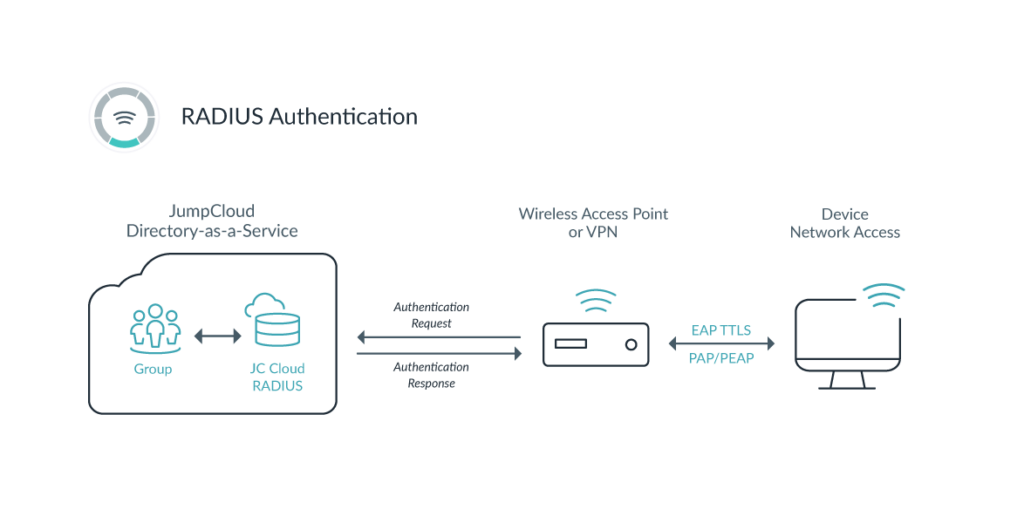
In a work-from-home environment, you can point your VPN to JumpCloud’s RADIUS server for authentication. JumpCloud’s RADIUS works with any VPN vendor, as long as the VPN server can be configured to authenticate using the RADIUS protocol. For example, if you’re using OpenVPN, you can easily direct authentication to JumpCloud.
Along with individualizing access for networks, JumpCloud has the ability to configure MFA for RADIUS authentication. Harden your VPN’s security by requiring both a user’s strong password and their MFA token during authentication through the VPN client.
Network Authentication via JumpCloud’s Secure LDAP
Another route to take is through JumpCloud’s Secure LDAP-as-a-Service. In this methodology, you would point your networking hardware or software to JumpCloud’s secure LDAP servers to handle authentication. This methodology is common among most VPN and firewall vendors.
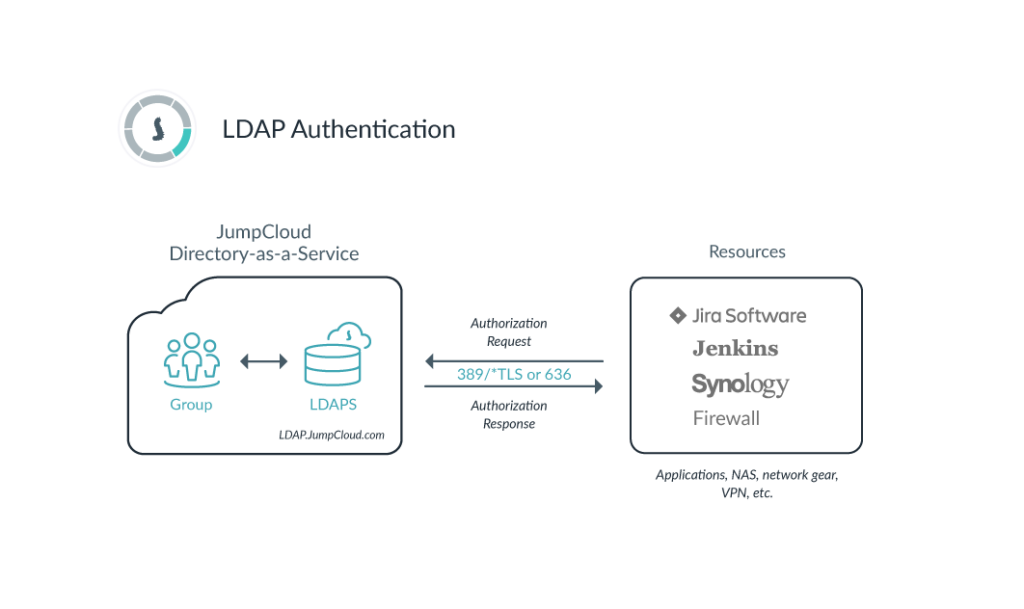
You’ll have to configure JumpCloud’s LDAP-as-a-Service before configuring your network to point to JumpCloud. This methodology is also secure and easy, as we use OpenLDAP RFC-2307 over the secure port of LDAPS/636. This way, any authentication to and from the VPN or firewall is encrypted and secure. OpenVPN is another example of a vendor that can integrate with JumpCloud’s secure LDAP-as-a-Service.
A Secure Domainless Enterprise Directory
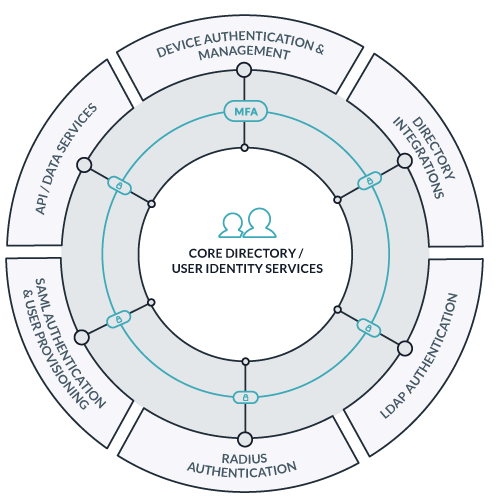
Moving into a domainless enterprise or full work-from-home model is secure and efficient with JumpCloud’s cloud directory platform. Protect your IT resources and employee identities with an entirely cloud-based solution, backed by secure protocol standards. Enforce security policies and allow users to change passwords on the system to help prevent web-based phishing attempts. Whether a company is five or 5,000 users, JumpCloud allows IT admins to manage their resources from anywhere on the planet from a single pane of glass via the Admin Portal.
You can secure systems with JumpCloud’s lightweight agent, enforce security policies, and ensure good security practices across your system fleet with a few clicks. You can also integrate your current applications, network hardware, and other directories with JumpCloud to consolidate your users’ credentials safely. JumpCloud is specifically designed to increase security without sacrificing simplicity.
JumpCloud was built to be the first cloud-based directory solution, and we can also assist a migrating company looking to move into a flexible, work-from-home environment. You can sign up with JumpCloud and begin testing on your own. If you’re looking at implementing JumpCloud for an organization with more than 10 users, check out JumpCloud’s various pricing plans and only pay for what you need.
Additional Resources
If you’re looking for additional reading beyond what’s included here, we’ve compiled other resources to help ensure you get the most out of your JumpCloud experience and make the transition to remote work as seamless as possible:
