For most organizations, user identities — and more specifically their passwords — are the gateway into critical business resources. However, billions of passwords exist across work and personal accounts belonging to people all over the world, which means there are billions of attack vectors ready to be exploited by malicious actors.
Experts estimate that over 8 million passwords are stolen every single day.
The reason why just the sheer existence of so many passwords creates vulnerabilities is because the passwords employees use at work are often considered insecure, weak, common, or even reused, and so the myriad of techniques malicious actors have at their disposal to steal, generate, and then brute force systems with passwords they’ve acquired could easily grant them legitimate access to various resources. The seeming lack of effort end users put into password security is never malicious; instead, due to a variety of factors such as account sprawl, poor login experiences, and attempts to make day-to-day workflows easier, end users are not always incentivized (or empowered) to take password security seriously.
On average, most departments use 40-60 tools each, and even if a single employee only accesses a third of those, password fatigue is an ongoing problem. The average individual has too many accounts to keep track of password best practices for all of them. This can result in reusing the same password they use for personal accounts, to keeping a list of their passwords in a spreadsheet or even written down on sticky notes or shoved into a desk drawer. Whatever the bad practice is, it adds significant risk to your organization, which cannot be ignored.

On average, employees reuse passwords across 16 accounts.
For these reasons, the burden of ensuring password and resource security should not fall on the end user. End users care about accomplishing their work, and they’ll find ways to make their day-to-day lives easier (i.e., getting access to resources and apps quickly and easily) at any cost. For most, password security is simply not a priority, especially considering the number of passwords needed to access all of their resources.
Progress Toward Password and Account Protection
Account sprawl is a significant issue for many organizations, but cutting down on applications and tools is a short-term solution at best. That’s why, over time, significant strides have been made to better protect passwords.
Multi-Factor Authentication
One example of this is multi-factor authentication (MFA), which has been widely adopted across both organizational and personal accounts. While MFA greatly enhances security, the continued existence and use of passwords will keep creating security problems for businesses everywhere.
For example, say an employee’s information gets compromised in a data breach, and a bad actor gains access to their password. While MFA will help protect work resources, that bad actor may also have access to that user’s email and many other accounts, which can allow them to bypass MFA requirements. The password is still a single point of failure in this scenario.
Passwordless Authentication
Another strategy for protecting resources better involves passwordless authentication, a model where users no longer need passwords to gain access to their accounts. Instead, users authenticate with safer (and more convenient) factors such as secure tokens and magic links, delivered via email, text message, or an authenticator app. However, even as passwordless authentication gains traction and organizations switch over to it, passwords will persist for a long time, which means they need to be securely managed for the foreseeable future.
Password Managers
Password managers were specifically created to help solve this problem, or at least mitigate its risk wherever possible, by creating a better way for end users to produce unique, complex passwords for each of their accounts. However, the original intent of password managers doesn’t quite match the challenges organizations face today.
The Creation of Password Managers
The original purpose of password managers was twofold:
- Enhance password security and promote best practices among end users.
- Simplify the end user password management and login experience.
They enhance password security by making it easier for users to create strong, unique passwords without the need for memorization, and they improve the user experience through simplified, digital password management instead of requiring passwords to be manually recorded somewhere insecure (such as a notebook or spreadsheet). This helps prevent password-focused attacks used by hackers to compromise accounts.

By using a password manager, organizations can also enforce password policies, such as requiring frequent password changes or complex passwords, without imposing a burden on their employees (or themselves). In addition, password managers often include features such as two-factor authentication (2FA), which adds an extra layer of security that protects against unauthorized access. Overall, password managers are an important tool for ensuring the security of an organization’s online assets and protecting against cyber threats.
And yet, devastating breaches still occur each year, compromising millions of accounts, credentials, and other personal and company information. Why? Because at the end of the day, despite the many advancements in the functionality of password manager technology, most password managers require a master password from the end user to grant access to their vault.
The original purpose of password managers was to improve end user password habits, but with the key to the entire password vault being yet another password, the burden of password security still falls largely on the end user.
Something needs to change in order to better protect passwords in the workplace, and that next step involves reevaluating the architecture password managers are built upon. Password management architecture is just as important as the features and benefits the manager offers (i.e., password generation, autofilling, sharing, etc.) to end users. Over the years, significant innovation has occurred in the realm of password management features, but now it’s time for the next wave of architecture updates to take place.
Types of Password Managers
Currently, password management solutions fall into two categories: traditional password management solutions that are cloud-based or purely store passwords offline, and the newer, hybrid password management approach which is, as you might have guessed, a hybrid between cloud-based and offline password managers.
Offline Models
The first type of traditional password management solution is referred to as an offline model. Offline password managers are software programs that store login credentials on a user’s local device, rather than in the cloud.
How Offline Models Work
They work by creating a secure, encrypted repository on the user’s device, and that repository is accessed using a master password. Users can then add new login credentials to their password manager by providing the website or application name, their username, and the corresponding password. The password manager will then securely store this information locally, encrypting the data contained within the vault until the proper credentials (i.e. the master username and password) are used to decrypt them for consumption.
When a user needs to log in to one of their accounts, they can simply go to the website or launch the app and use their password manager to automatically fill in their login credentials. This saves users from having to remember multiple complex passwords, and it helps to prevent password reuse, which is a common attack vector for hackers.
Offline password managers offer the advantage of being completely independent of the internet, which can be useful for users who are concerned about their online privacy or security.
Limitations of Offline Models
With offline password managers, users will still need to create a master password that they can remember in order to access their vault. Another issue with offline managers is that they store passwords on the user’s device, with no way to sync the vault across multiple devices. Instead, users have to manually copy and paste their vaults on each device they use and then keep them updated manually after that, which is tedious and inefficient.
Offline password managers are not suitable for modern, business use cases for a few reasons:
- They require the user to install and maintain the password manager software on their device, leaving password management control solely up to the end users themselves.
- They do not offer the same level of convenience as their more modern counterpart, cloud-based password managers, which can be accessed from any device with an internet connection.
- They do not offer basic required business functionality such as centralized admin management of passwords, centralized audit logs, or password-sharing functionality between multiple users.
Let’s recap the main benefits and limitations of traditional, offline password managers:
Benefits of offline password managers:
- Local, offline password storage reduces the potential exposure of sensitive information.
Limitations of offline password managers:
- Passwords cannot be accessed on multiple devices without manual user effort.
- No centralized admin controls or usage logging make it challenging for IT admins to deploy and manage users effectively.
- No password sharing capabilities between users means resources that require shared accounts cannot be stored and maintained effectively or securely.
Overall, offline password managers are a good option for users who want to store their login credentials locally and who are willing to trade convenience for the added security of being disconnected from the internet. They can be a great first step toward password management in a personal context, but they become extremely inefficient in business contexts where there are many users, with multiple devices, using a hybrid or remote working strategy, that need to collaborate and share passwords easily — with IT overseeing all of this.
Cloud-Based Password Management Models
The second type of traditional password management solution is cloud-based. Over the years, cloud-based architectures were developed to expand password management capabilities even further (especially as smartphones and tablets became default devices in everyone’s lives). Cloud-based managers opened the doors for organizations to more effectively manage and deploy modern devices on behalf of their users.
How Cloud-Based Models Work
Cloud-based password managers work by storing encrypted login credentials in an online repository accessible from any device with an internet connection. Users can access their password manager using a web browser or a dedicated mobile app, and use the password manager to store and manage their login credentials for various online accounts.
Just like offline password managers, to use a cloud-based password manager users need to create, manage, and remember a master password, which is used to access their vault. This master password should be kept secret, as it is used to encrypt and decrypt all of the login credentials stored in the password manager.
Once a user has logged into their password manager account, they can add new login credentials by providing the website or application name, their username, and the corresponding password. The password manager will then store this information in the cloud in an encrypted form. Cloud-based password managers offer business features including centralized admin management, centralized usage logging, and password sharing between users.
Just like offline password managers, when a user needs to log in to one of their accounts, they can simply go to the website or launch the app and use their password manager to automatically fill in their login credentials.
Limitations of Cloud-Based Models
Due to cloud-based password managers’ reliance on users managing the “master keys” to their vault as well as the password management vendor storing encrypted customer vaults on their cloud servers, the security of cloud-based password managers can be an area of concern. Because of the architecture they’re built on, cloud-based managers offer multiple avenues for malicious parties to degrade and sometimes compromise the security of entire organizations.
Here are some of the risks associated with cloud-based password managers:
- Weak and reused master passwords, created and managed by end users, can easily be guessed which can compromise an organization’s entire password vault.
- Phishing end users allows hackers to potentially access business vaults even when employees use strong and unique passwords.
1.5 million new phishing websites are made monthly.
- The compromise of the cloud storage infrastructure of password management vendors can lead to malicious parties downloading the entire database of encrypted customer vaults, giving hackers an infinite amount of time to try to gain access by brute-forcing the master passwords of end users. It is important to note that in this case, 2FA does not help protect customer vaults.
Let’s recap the main benefits and limitations of traditional, cloud-based password managers:
Benefits of cloud-based password managers:
- Users can access password vaults from multiple devices, with credentials always in sync between them.
- Centralized admin controls and usage logging give IT admins better visibility and management capabilities to enforce best practices.
- Password sharing capabilities between users which helps reduce friction.
Limitations of cloud-based password managers:
- Vault security rests on end users’ ability to create, manage, and remember strong master passwords, which can be difficult to enforce beyond training.
- Phishing is a growing threat, and with users in charge of the master keys, we will continue to see more and more organizations get compromised.
- Password management service providers, if compromised, can lead to the mass exfiltration of encrypted customer vaults which gives hackers enough time to try to gain access to the encrypted vaults by attempting to guess weak and reused master passwords.
Overall, cloud-based password managers offer a convenient way for individuals and organizations to manage their login credentials. Cloud-based password managers make collaboration easier, and users can access their vault across multiple devices. However, the added level of convenience and sole focus on availability comes at the expense of security due to the heavy reliance on end users creating and protecting strong master passwords, as well as on the password management vendor itself.
The existence of user-created and user-managed master passwords and the centralized cloud storage of passwords are two risk factors that accompany the use of cloud-based managers.
The Challenge With Traditional Architecture
While both traditional password management approaches tend to focus on helping ease the threat of attacks by improving weak password habits, they still require users to remember (and thus create, on their own) a master password to access their vault. Passwords are the weak links in the access chain, so this method of password storage maintains the limitation password managers intend to mitigate: the reliance on a single password that an end user must remember and that provides significant access to sensitive information.
This master password is the ultimate gateway into the password vault, and it’s used to encrypt and decrypt all of the login credentials stored within the password manager. Yet, this master password cannot be stored in the vault, as it’s needed to get into the vault itself; this catch-22 may lead users to reuse or create weak master passwords, or store them in an insecure, easy-to-find place, and effectively eliminate the benefits the password manager has granted.
Even if users create strong and unique master passwords, phishing is still a common (and effective) attack tactic that has the potential to give hackers the golden key into enterprise vaults.
Password management architecture has to evolve in a way that leaves master passwords in the dust, or the trend in breaches will continue. The good news is that there is a new way for organizations to manage passwords: a hybrid approach.
Hybrid Models (Decentralized Architecture)
So, what exactly is a hybrid password manager? Hybrid models use a blend of features from offline and cloud-based models; however, unlike traditional models, hybrid password managers are built upon a decentralized storage architecture. This means that password vaults are stored locally on devices, while a cloud-based system seamlessly syncs passwords between devices accessing the same vault using end-to-end encryption.

Because this architecture stores passwords locally on user devices, there is no need for a master password. Passwords are encrypted using locally generated keys that are stored in the secure storage unit of the device the passwords are on, and the vault can be unlocked using biometrics or a local PIN code.
Hybrid password managers aim to bridge the gap between security and convenience for organizations looking to securely incorporate password management into their IT technology stack.
Better Together: Combine a hybrid password manager with single sign-on (SSO) capabilities to get the best of both worlds. Provide users with a simple, convenient way to access their resources, while ensuring that their login credentials are strong, unique, and managed securely.
Benefits of hybrid password managers:
- No master password required.
- Local password storage.
- Users can access password vaults from multiple devices, with credentials always in sync.
- Centralized admin controls and usage logging give IT admins better visibility and management capabilities to enforce best practices.
- Password sharing capabilities between users which helps reduce friction.
Overall, a hybrid, or decentralized, password management architecture gives organizations and end users the best of both worlds while eliminating some of the issues of traditional models. Hybrid password managers make collaboration easier, facilitate remote work, allow users to easily manage passwords across all of their devices, and give IT the control and visibility they need to maintain security. And, on top of all of these benefits, security is maintained and even enhanced through the elimination of the insecure master password that traditional models use, as well as the decentralized storage of passwords and encryption practices.
JumpCloud’s Hybrid Password Manager
JumpCloud’s open directory platform includes a password manager built on the decentralized architecture described above. Passwords are stored locally and synced in an end-to-end encrypted manner between the devices you choose, with no master password needed to access the vault.

This modern approach to password management architecture allows users to remain productive with an enjoyable, seamless experience, while promoting secure credential management practices. Enjoy the features you expect, such as autofill and auto-save, on top of easy password sharing, multi-device vault syncing, and more.
JumpCloud Password Manager also gives IT admins centralized visibility and control over password management and sharing, as well as a handful of other benefits. Some of these benefits include the abilities to:
- Easily enroll users and teams into the password manager.
- Terminate users’ access which results in their password vaults getting wiped from all devices.
- Get granular control over the access levels of users to shared folders.
- View password strength dashboards to spot weak and reused passwords.
- View password vault metadata to see which passwords are being managed and shared by users in the organization.
- View usage logs to see which users used or viewed certain passwords.
JumpCloud Password Manager introduces a novel approach to organizational password management that aims to reduce the reliance on end users and the service provider to protect vaults while enabling business use cases and introducing high levels of added convenience across the board.
JumpCloud Password Manager is managed within the JumpCloud Console and is available as an application on Mac, Windows, and Linux. Mobile applications are also available for iOS and Android, and there are browser extensions on Chrome, Edge, Firefox, and other Chromium-based browsers such as Opera and Brave.
Let’s take a look at the behind-the-scenes processes that power JumpCloud Password Manager’s hybrid approach.
Vault Storage
When users activate JumpCloud’s password manager app on a new device, an AES256 key is generated in order to encrypt the vault locally. An RSA2048 key-pair is also generated for that device, which is used to encrypt and decrypt passwords that sync between multiple devices. These generated keys are stored in the secure storage unit of their respective device, such as the Apple Keychain, the Windows Credentials Manager, and the Android Keystore.
Unlike with cloud-based password managers, the password vault is not uploaded to JumpCloud servers; instead, it remains locally encrypted (using the AES256 key) and stored on the device that the password manager was activated on. This is an important difference in architecture compared to traditional approaches.
Vault Syncing Between Devices
Modern employees use a variety of different devices for work, and they all need to remain in sync. JumpCloud Password Manager makes this a reality by allowing end-to-end encrypted password vault syncs between any devices.
When a user activates the password manager app on a second device, they pair their two applications by scanning a pairing code displayed on the secondary device.
This process:
- Generates new RSA2048 and AES256 keys in the app on the new device.
- Shares the RSA2048 public key of that new app with JumpCloud servers and with the first app.
- Prompts the first app to automatically encrypt the password vault using that new RSA2048 public key and relay it through JumpCloud servers to the new app, which receives the password vault and is now in sync with the first app.
Moving forward, the password vaults will remain synchronized across both devices. Whenever the user makes a change to the vault on one of the two devices:
- A new AES256 key is generated for this change, the change is encrypted with the new AES256 key, and the key is encrypted using the RSA2048 public key of the second device.
- The change is signed with the RSA2048 private key of the device the user is making the change on.
- The encrypted and signed “sync” message is relayed through JumpCloud servers to the second device, which proceeds to verify the signature, decrypt the “sync” message, and incorporate the changes in its locally stored vault.
The primary benefits of this approach are that it:
- Removes the need for users to create, manage, and remember master passwords. The encryption keys required are locally stored and unique to every device. The process relies on asymmetric encryption, which uses the public key of other devices to encrypt data as opposed to relying on the same key (aka a master password).
- Ensures that data is automatically synced between multiple devices.
- Greatly reduces the possibility of vaults getting compromised as a result of phishing.
Business Use Case Features
In addition to offering a secure and convenient way for users to access and manage passwords across devices without relying on master passwords, JumpCloud Password Manager offers all of the business features that organizations need.
These features include:
- Centralized admin controls.
- Centralized vault visibility.
- Password sharing between users and teams.
- Multi-tenant capabilities for managed service providers (MSPs) and value-added resellers (VARs).
- Unified access management from a single admin console.
Centralized Admin Controls
Modern workplaces include hybrid employees, a plethora of different devices, and a strong need for collaboration, so IT admins need an easy and secure way to view and manage access to set users up for success.
JumpCloud Password Manager can be centrally managed by IT admins from a cloud-based console. Admins have access to all major features that they expect out of a modern password management solution, including the abilities to:
- Enroll users and teams into the password manager.
- Terminate users’ access, which results in their password vaults getting wiped from all devices.
- Visualize and granularly control users’ access to shared folders.
Centralized Vault Visibility
On top of IT admins getting centralized control over who gets enrolled or removed from shared folders or even the password manager itself, they also need high visibility into user vaults to ensure that compliance and security initiatives are being met.
With JumpCloud, IT admins get full visibility over users’ passwords at the organizational level, at the shared folder level, and at the end user level. This does not mean that admins can see users’ passwords — rather, it means that they have the ability to:
- View password strength dashboards to spot weak and reused passwords.
- Monitor password vault metadata to know which passwords are being managed and shared by users in the organization.
- View usage logs to know which users used or viewed which passwords.
Password Sharing
An organizational password management solution isn’t complete without the ability for users to easily share passwords with each other. With JumpCloud Password Manager, users can securely share passwords with varying permission levels using a decentralized approach, similar to the process outlined above regarding cross-device password syncing.
When a user is added to a shared folder, they are granted one of three different permissions by the folder admin(s). Users can become a:
- Folder Member: Giving them only “usage” permission over passwords in the folder. This permission authorizes the password manager to autofill passwords on behalf of the user in web forms without granting “edit,” “view,” or “copy” permissions over the passwords to the user.
- Item Manager: Giving them control over the items in the folder (view, add, edit, and delete).
- Folder Manager: Giving them full control over the folder and the ability to make changes to the users and items in the folder.
How Password Sharing Works
When a change is made to a password in a shared folder, the app that made the change encrypts then signs a “sync” message with the public keys of every member of the folder. These “sync” messages are then relayed through JumpCloud servers to all of the apps of the different users in the folder.

Multi-Tenant Capabilities
It seems natural that modern password managers can support the needs of in-house IT departments, as well as MSPs and VARs, but this is not the case for many cloud-based managers.
However, JumpCloud Password Manager offers a multi-tenant admin console which allows partners to add password management to their service offering, while easily supporting and managing each client’s password manager setup, all from a single console, but within a unique interface for each.
This simplifies the task of deploying and managing a password manager across a wide range of clients without having to manage numerous parent accounts that each require their own set of unique credentials to access. Because of this, JumpCloud Password Manager is a perfect solution for MSPs and VARs that have previously struggled to include password management as part of their service offering.
Unified Access Management From a Single Admin Console
The needs of IT professionals vary, but they tend to intersect at the same place — finding a way to easily and securely manage identities, access, and devices without breaking the bank or adding too many different tools into their stack.
This is where JumpCloud’s open directory platform comes in handy — not only does JumpCloud offer a modern, decentralized password management solution as a core part of the platform, but it also includes all of the features you need and expect for comprehensive identity, access, and device management. This allows IT admins and MSPs to manage SSO, MFA, and password-based authentication across their organizations from one consolidated admin console.
Compare JumpCloud to Traditional Password Managers
| Feature | Offline Password Managers | Cloud-Based Password Managers | JumpCloud Password Manager |
| Storage of passwords | Local on a single device | The cloud | Local and automatically synced in an end-to-end encrypted manner across multiple devices |
| Access via user-managed master password | Yes | Yes | No |
| Centralized admin controls | No | Yes | Yes |
| Centralized admin visibility | No | Yes | Yes |
| Multi-tenant capabilities | No | Depends on vendor | Yes |
| Native integration with cloud directory, SSO, and MFA | No | No | Yes |
Take a New Approach to Password Management
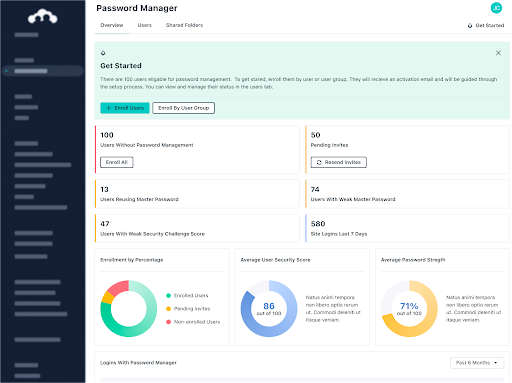
JumpCloud Password Manager’s hybrid, decentralized architecture is a new and modern approach to password management that was created with both security and ease of use in mind. It includes all of the business features you expect a robust password manager to have, while providing a new convenient and secure way to store, manage, and share passwords.
JumpCloud Password Manager is also part of a much bigger story. JumpCloud’s open directory platform houses its password manager among many other capabilities. Think: SSO, MFA, conditional access, open integration capabilities, robust identity and access management, cross-OS device management, Cloud LDAP, Cloud RADIUS, and so much more.
Why this matters: Technology unification is a popular strategy for eliminating unnecessary attack vectors that tool sprawl can create, and adding JumpCloud to the center of your IT technology stack is a great place to begin. Not only does JumpCloud offer a built-in hybrid password manager — it also includes many other native features that eliminate the need for point solutions.
Don’t get stuck in the past with traditional password management solutions — try JumpCloud Password Manager today, for free.
