Change is one of the most challenging aspects of IT. Not every employee is tech savvy or open-minded about trying, or even accepting, new things. File servers are oftentimes critical infrastructure and users are accustomed to working with them.
That’s why uninterrupted access is important when a small and medium sized enterprise (SME) is considering making the “jump” away from Active Directory. Fortunately, an easy configuration accomplishes just that.
The solution is a trick that veteran Windows admins are familiar with: using commands to map network drives, which fixes the problem of missing desktop drive icons among VPN users. The same solution can be applied when transitioning from Active Directory to JumpCloud.
It’s an approach that keeps users happy, workflows uninterrupted, and reduces support calls. More importantly, it provides a runway to a longer term strategy for file sharing and collaboration.
Maintaining Windows Files Shares with JumpCloud
The following steps make it possible to use Windows File Shares with JumpCloud, even after detaching users and devices from Active Directory. When this work is completed, JumpCloud will become the single “source of truth” for your users to access devices and other IT resources.
Prerequisites
The initial steps will include installing JumpCloud agents on your domain controller(s).
Install JumpCloud Agents
- An understanding of JumpCloud Commands
- Configure JumpCloud’s AD Sync and AD Import agents:
- AD Sync is used for user provisioning and SSO. It enables you to maintain your existing directory within JumpCloud, which will become your IdP (SAML SSO). In this case, you will no longer be managing your users from AD. For example, if you make a password change to a user in JumpCloud it will sync to AD.
- AD Integration integrates AD with JumpCloud
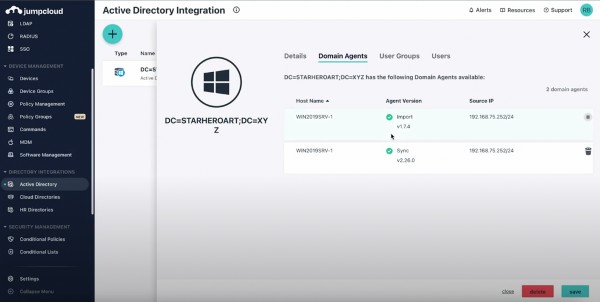
A sync user is used to set up the agents:
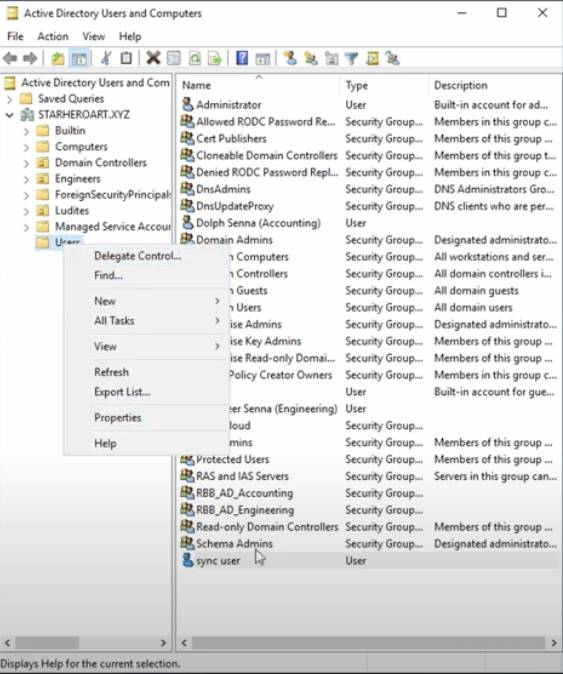
Replicating Windows Server Groups
- Verify which AD security groups are given rights/privileges to each file share on the Windows File Server.
- Add those security groups as member(s) of a “JumpCloud” group in AD
- This may be a good opportunity to address any poor naming conventions
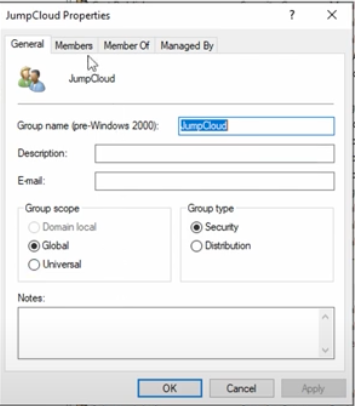
You’ll notice that groups (rather than users) are contained under the “Members” tab with inherited rights and privileges.
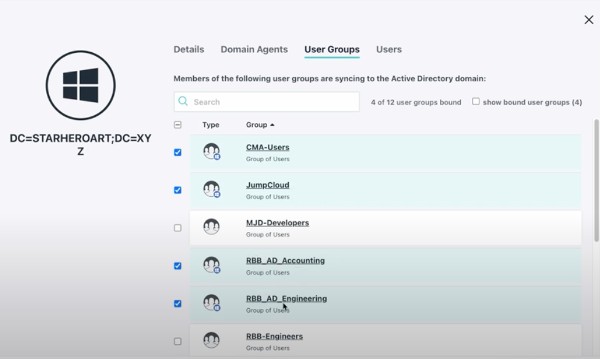
- Verify that proper users are members of the specified groups, noting that users display “Name” inside of AD and account names aren’t the same thing.
Configure Your JumpCloud Command to Map File Shares
We’re assuming that you’ve already created your shares. The next step is to create a command to map drives within JumpCloud. This knowledge base article outlines the requisite step to do that. Windows will run a batch file upon each user login on every device in the user group.
Those steps include:
- Create a batch file containing the following, replacing the net use path as necessary:
echo off
reg add hklm\software\microsoft\windows\currentversion\run /v mapdrive /t REG_SZ /d c:\scripts\netuse.bat /f
mkdir c:\scripts
echo net use * /delete /yes > c:\scripts\netuse.bat
echo net use g: “\\fileserver\share” /user:DOMAINNAME\%%username%% >> c:\scripts\netuse.bat
You’ll be using the NETBIOS server name.
For this example, name it mapdrives.bat
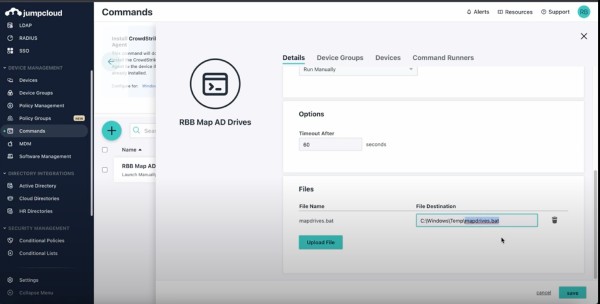
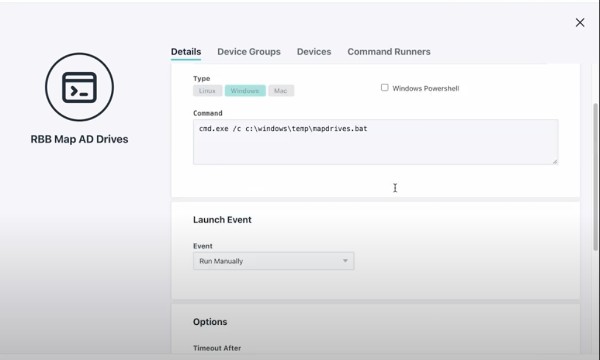
- Create a Command in the JumpCloud admin console, deselect powershell. The contents of the command as follows:
cmd.exe /c c:\windows\temp\mapdrives.bat
Go to the file upload section and upload your mapdrive.bat to c:\windows\temp and run it on any target system where drives need to be mapped.
*If running a 32-bit operating system modify the command in Step 2 to:
%windir%\sysnative\cmd.exe /c c:\windows\temp\mapdrives.bat
A registry entry will be added to run scripts every time any user logs into the PC. Windows will generate another batch file for the login command after you run this the first time.
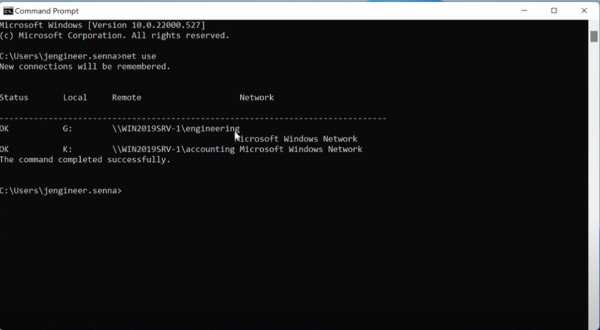
You can verify that drives are mapped on a user device by running the net use command. Note that all drives will be mapped, but access will be restricted by the share’s permissions.
Users will receive an error message when attempting to access a drive they don’t have access to. This is a common user experience for Windows File Shares, but you can avoid this scenario by creating individual batch files for each shared drive. You’re not changing your file server at all.
Migration Away from Active Directory
Your ultimate goal is a full migration away from Active Directory. The linked article covers that in more detail, but your steps are essentially:
- Use ADMU to detach each user/computer from AD.
- Follow the steps outlined above to map network drives after binding the user to a windows device in JumpCloud.
- Voila – Drives are mapped to local on-premise Windows file shares that your remote users may access over your VPN.
Try JumpCloud Without Disrupting Your Operations
JumpCloud offers true SSO, RADIUS services, integrated MFA, patching, MDM, smart groups, and much more. JumpCloud can extend Active Directory with these services or help you to modernize IT and decommission legacy servers. To try it for yourself, sign up for a trial of JumpCloud.



