Trust nothing and verify everything.
Does this sound like the maxim of a bleak, dystopian society? It’s actually the core philosophy behind the increasingly popular Zero Trust security framework.
Zero Trust involves implementing several controls designed to ensure only verified network users can access limited organizational resources on trusted devices. It also promotes safeguarding data infrastructure with practices like microsegmentation of “east-to-west” traffic protection measures to reduce the severity of potential breaches.
Random take: William Shakespeare totally would have embraced Zero Trust. The playwright shrewdly recognized that kindness isn’t synonymous with unearned trust.
Love all, trust a few, do wrong to none.
William Shakespeare, All’s Well That Ends Well
Starting any new endeavor can feel overwhelming, especially when one wrong move could cause productivity to come to a grinding halt.
This article will highlight seven simple action steps — emphasis on the word simple — for small-to-medium-sized enterprises (SMEs) wanting to move toward a Zero Trust security framework.
The FBI, 792K Cybercrime Complaints, and Zero Trust
Did you know the FBI received nearly 792K complaints of “suspected internet crimes and losses” in 2020? The average total loss exceeded $4.2 billion.
Translation: Your coworkers themselves can be trusted, but unverified logins from unfamiliar networks and devices should now be assumed guilty until proven innocent.
On-premise security solutions were not built to handle modern security threats that are only being amplified within vulnerable remote workforces. Statistics like these, and well-known brands making newspaper headlines, that have brought a proven cybersecurity framework to the forefront of public conversation.
John Kindervag, Forrester Research analyst, coined the “Zero Trust” term back in 2010.
As shown in the graph below, the term didn’t gain notoriety until around 2018:
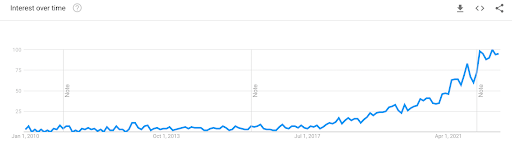
Nonetheless, only 23% of small and medium enterprises (SMEs) have fully embraced Zero Trust. Overcomplication of Zero Trust, lack of strategy, and misunderstanding among executive leadership are some of the reasons for the slow adoption rate.
7 Simple Action Steps to Build Zero Trust
Does any of that sound familiar? If so, consider focusing on the seven simple steps below to move your SME in the direction of Zero Trust.
1. Take Stock of Digital Assets
Zero Trust authority Forrester recommends creating a roadmap based on five categories:
- Networks
- Data
- Devices
- Workloads
- Identity
The catch is you can only do this exercise if you have good visibility. Users often access resources from multiple devices across various networks and apps. Create a comprehensive inventory for all of the above to inform strategy around how to best take baby steps toward a Zero Trust network.
More importantly, know where your most sensitive data is, how it flows across the organization, the users accessing it, and the devices they use to access it. Taking an inventory will help you to prioritize and focus on your digital assets that need more protection.
It’s essential to recognize that Zero Trust implementation isn’t a one-off event. As mentioned before, Zero Trust is not a product but a framework. It’s a gradual process that can take years to fully implement. Google, for example, took about six years to shift from its VPN and privileged network access model to its own Zero Trust network.
2. Focus on Identity and Access Management
Have you heard of the principle of least privilege (PLP)? It’s a way to ensure employees have access to just enough resources they need to do their job — coincidentally, this is also the core element of identity and access management (IAM).
IAM securely manages and connects users to the right IT resources at the right times and for the right reasons. These resources include identities, networks, files, apps, and devices. Each user receives controlled access to the digital assets they need, while simultaneously being locked out of those they don’t need.
IAM is one of the most important IT functions, especially in an increasingly hybrid workplace. When implemented correctly, it prevents sensitive resources from landing in the wrong hands. For example, contracted administrative workers gaining access to a company’s financial records.
Here are a few tips to build an effective IAM system:
- Start with directory services and organize identities into logical access groups.
- Use directory extensions to increase functionalities.
- Implement PLP to ensure every user gets the right level of access.
- Streamline access to different web apps with single sign-on (SSO).
- Leverage password vaults to increase convenience without jeopardizing security.
- Deploy multi-factor authentication (MFA).
It’s worth emphasizing that implementing IAM in a remote work environment can be extremely complex because remote employees work on multiple platforms using various devices. Leverage a platform like the JumpCloud open directory to streamline IAM in heterogeneous environments.
3. Enable Multi-Factor Authentication
Multi-factor authentication (MFA) is a core component of IAM that requires users to provide more than one verification method before accessing a resource.
Authentication requires any of the following additional elements of information:
- Knowledge: Things users know, such as a PIN or passcode.
- Possession: Things users have, for example, a smartphone or a badge.
- Inherence: Things users are, such as voice recognition or fingerprints.
MFA requires additional verification factors beyond a basic username and password because this has been proven to decrease the likelihood of a security breach. One of the most common MFA methods is one-time passwords (OTP).
Multi-factor authentication is one of the most critical steps toward Zero Trust.
According to Google, MFA can stop all automated attacks, 96% of bulk phishing attacks, and 75% of targeted attacks.
At least 57% of companies globally are already implementing MFA.
4. Beef Up Credentials
Weak passwords compromise the security of your systems and make it easy for malicious characters to gain access to your network resources. The stronger your password, the harder it is to crack and the more effective at preventing breaches.
Weak passwords, such as “123456” or “admin,” are a hacker’s paradise because they are easy to guess. Other common password mistakes users make include using:
- Default passwords that come with the device.
- Short passwords.
- Passwords that don’t contain numbers or symbols.
- Passwords substituting letters with numbers, for example using 4 for the letter A.
- Passwords that contain personal information.
- Passwords that follow a pattern, for example, Qwerty098765
With so many accounts to keep track of, it’s often difficult for employees to remember their passwords. This is why we recommend using a password manager. A trusted password manager creates and stores strong, lengthy passwords for users. The user simply memorizes a single master password to gain entry into multiple accounts. Keeper and OnePassword are user-friendly password manager vendors worth considering.
5. Prioritize Mobile Device Management
Mobile device management (MDM) is a toolset that enables IT managers to secure, control, and enforce policies on mobile devices. It is a core component of enterprise mobility management (EMM) that helps to optimize the functionality of enterprise mobile devices while protecting the company network.
MDM makes it possible for organizations to manage end-user devices without disrupting their workflow. With remote and distributed workforces becoming the norm, MDM helps securely onboard employees and configure devices. It enforces cybersecurity by only allowing conditional access and protecting lost or misplaced devices through shutdown, lock, and wipe commands.
Several MDM solutions offer different features and capabilities in the marketplace. When evaluating your options, consider a solution such as JumpCloud that offers a unified platform for managing Windows, Apple, and Linux devices behind one pane of glass.
6. Reduce Your Attack Surface
An attack surface refers to the area of your organization or system that’s vulnerable to unauthorized access. It’s the entry point that malicious actors use to enter systems and manipulate resources or download sensitive data. And it’s, basically, the entire external-facing area of your system.
Common attack surfaces include corporate websites, virtual private networks (VPNs), employee portals, expired security certificates, and stolen employee credentials. The smaller the attack surface, the easier it is to protect.
Below are a few ways to reduce your attack surface:
- Conduct a surface attack analysis to identify your vulnerabilities.
- Implement privileged identity management.
- Limit authentication access entry points.
- Segment your networks.
- Protect backups.
- Use strong authentication policies.
7. Prioritize Patch Management
IT admins must continuously monitor your devices, apps, and systems to identify and address security vulnerabilities. This is why patch management is an integral component of Zero Trust.
Patch management is the process of coordinating software patches and updates on devices, apps, and systems. It includes testing, rollout, monitoring, and in some cases, rollbacks across the organization.
Patch management helps make patching more predictable, visible, efficient, compliant, insightful, and automated. It also makes the process less error-prone and easier to reconfigure.
The best practice is essential for organizations that have adopted remote work and bring your own device (BYOD) policies. It can be done in a piecemeal or orchestrated manner; piecemeal patch management means initiating different processes for different operating systems, while orchestrated patch management requires coordinating across different operating systems, applications, and devices.
Tools such as the JumpCloud open directory platform automate cloud patch management so IT admins and MSPs can focus on other high-priority tasks.
Simplify Zero Trust with JumpCloud
Rome wasn’t built in a day, and neither are the strongest Zero Trust network architectures. Zero Trust isn’t a single switch you can turn on. It’s a combination of several best practices that work together to tighten network security.
But you can enhance your organizational security by taking any of the small steps discussed in this article. Have your organization’s Zero Trust initiatives stalled because of tool sprawl? It’s not uncommon for SMEs to postpone security initiatives due to both budgetary constraints and unsynchronized stacks.
If this is your dilemma, we invite you to try the JumpCloud Directory Platform. JumpCloud consolidates your most crucial Zero Trust point tools into a centralized platform for IAM, MFA, SSO, and patch management implementation at a fraction of the cost.





