Zero Trust isn’t only for enterprises with massive budgets and complex stacks. It has become essential for organizations of all sizes that need to protect a modern, distributed workforce.
But while many organizations say they’ve implemented Zero Trust, the reality is that very few go beyond the surface. Most efforts cover only high-risk users or systems, leaving major gaps across the rest of the environment. As threats evolve and cloud adoption accelerates, these gaps become serious liabilities.
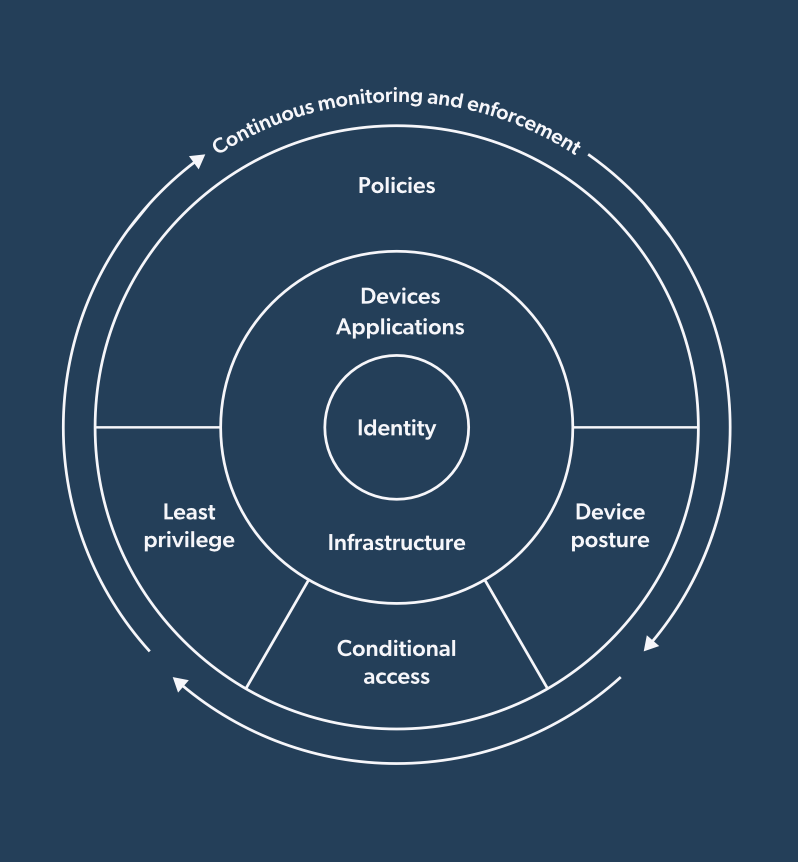
To build a Zero Trust program that adapts to risks and is scalable, you need more than multi-factor authentication (MFA) and a few access policies. You need complete coverage across five core areas:
- Identity and access management (IAM)
- Device trust
- Network and application access
- Privileged access management (PAM)
- Visibility and monitoring
These are the structural pillars that support long-term security, operational efficiency, and resilience in the face of evolving threats. Keep reading to dive deep into each of these focus areas.
1. Identity and Access Management
Everything starts with identity.
If you can’t confidently verify who’s trying to access your systems, nothing else matters.
A strong IAM foundation means enforcing MFA across all access points, not just admin accounts or remote logins. It also includes setting up conditional access rules that evaluate context — like device, location, and time — before granting access.
IAM is not just about access control. It’s about verifying that the right person, using the right identity, is requesting access in the right way.
2. Device Trust
User identity is only part of the equation. You also need to know whether the device being used is secure and compliant.
Device trust means verifying that endpoints meet your organization’s security standards before they’re allowed to access sensitive data or systems. This could include operating system (OS) version, patch status, encryption, or mobile device management (MDM) enrollment.
Without this layer, a verified user logging in from an unmanaged, compromised device can still create risk.
3. Network and Application Access
Legacy security models gave users broad access to internal networks through VPNs. That approach increases risk because it allows attackers to move laterally once inside.
In a Zero Trust model, users get access only to the applications and services they need, and nothing more. This limits lateral movement inside the network and reduces exposure.
Application-level segmentation and access policies tied to user context allow you to move away from broad, perimeter-based controls and toward more granular enforcement.
4. Privileged Access Management
Not all user accounts are equal. Admins and service accounts hold significantly more power — and they’re a prime target for attackers.
Zero Trust demands strict controls around privilege escalation. PAM should be integrated across your environment and include capabilities like just-in-time access, automatic revocation, session monitoring, and auditing.
Static admin credentials, especially those that never expire or are shared across teams, introduce long-term risk. They need to go.
5. Visibility and Monitoring
You can’t enforce what you can’t see. A Zero Trust program is only effective if you have complete visibility into who accessed what, when, from where, and how.
Centralized logging, real-time monitoring, and anomaly detection are essential. These controls help IT teams identify risks early, support audits, and continuously refine access policies.
Without visibility, enforcing policies consistently or responding to threats quickly becomes tedious.
Build a Stronger Security Posture
Implementing Zero Trust isn’t a one-and-done project. It’s an ongoing initiative that requires clarity, coordination, and scaling. Focusing on just one or two areas may create a false sense of security. To effectively manage today’s threats, your Zero Trust strategy must address all five core areas.
Most IT teams aren’t struggling with the “why” behind Zero Trust. It’s the “how” that gets complicated. Competing priorities, limited resources, and tool sprawl make it difficult to move beyond surface-level adoption.
That’s exactly why we created our latest eBook Where Zero Trust Falls Short. It explores each must-have in detail and outlines a phased roadmap for scaling Zero Trust across your organization. Download the eBook and take the next step towards a more resilient security posture.




