Being an IT admin can sometimes feel like running a circus.
Rather than scheduling performances, taking care of animals, and keeping an audience entertained, you’re managing networks/devices, ensuring they’re secure and up to date, troubleshooting issues, and keeping employees productive.
Managing devices is more critical than ever because they contain everything a user or an employee needs to get work done. While many pundits make the mistake of assuming contemporary device management solely concerns managing phones, tablets, and other “network computers,” IT admins know better.

The power of desktops and laptops are conducive to productivity at a rate that mobile devices still can’t match. The big question: If Mac, Windows, and Linux systems are here to stay, how can an IT manager best manage them all in the same environment?
Luckily, unlike a circus manager, IT admins have a Swiss Army knife to help manage their digital circus: an open endpoint management system. This article will discuss open endpoint management systems, how they work, and identify the best ones and their key features.
Pros and Cons of Open Endpoint Management Systems
“Open software” has a publicly available and modifiable source code.
Therefore, open endpoint management systems enable IT administrators to centrally manage and monitor endpoint devices such as laptops, desktops, mobile devices, and servers.
Admins use them for software deployment, patch management, remote control and support, security management, etc.
Pros
The benefits of open endpoint management systems are:
- Low fees: Thanks to the large developer community working on them, open source endpoint management software is often free or affordable.
- Active community: The active community created by users and developers ensures that they release bug fixes, new features, and more use cases faster than proprietary software developers.
- Transparency: Open source endpoint management systems are publicly available for review. This makes it easier for developers to examine it for vulnerabilities. Plus, they can always check to see that the software behaves as advertised and doesn’t do anything malicious.
Cons
And the downsides are:
- Security concerns: The transparency described above is rather two-edged. While some people may check for vulnerabilities to close them off, malicious actors can also look into the endpoint management’s source code to find and exploit vulnerabilities.
- Lack of customer support: The biggest downside to open source endpoint management systems is that users can not always be assured support when issues arise. Or in instances where customer support exists, the user will have to pay a fee and might wait for significant periods before getting help.
- Non-comprehensive solutions: Most open source endpoint management systems tend to provide only one service. Some focus on providing antivirus protection, while others may focus on patch management. Thus, you may have to cobble together tools from different sources for comprehensive endpoint management.

How to Choose Open Endpoint Management Software
There are several factors to consider when choosing endpoint management software. However, we’ll focus on three which we think apply to most organizations:
1. Assess Compatibility
It’s a no-brainer that your management system must be compatible with the devices that make up your workforce.
While a few workplaces still use a homogenous fleet of devices, most organizations have shifted toward a heterogeneous collection of Windows, Mac, Linux, and even Android.
Regardless of the case, you will want to select a system compatible with the devices that the employees in your office use.
Most endpoint management systems cater only to specific operating systems, while others, such as JumpCloud, provide coverage for a broader range of devices.
2. Identify Integration Options
You should also consider the variety of integrable tools the management system provides. Many management systems come bundled with solutions that give IT admins seamless management capabilities.
For instance, with JumpCloud, IT admins can do more than just manage devices; they can also leverage multi-factor authentication (MFA), single sign-on (SSO), and password managers to improve security.
Besides these factors, also consider integration with third-party tools that provide other solutions. For example, an admin who integrates their endpoint management systems with security tools such as antivirus software or threat detection platforms can proactively identify and address security threats on endpoints better than those who don’t.
3. Evaluate Scalability and Flexibility
Lastly, ensure your preferred endpoint management system can handle more or fewer devices without compromising performance or features.
Also, the management system should be flexible in its pricing models. This means you shouldn’t get locked into a one-size-fits-all structure. Instead, you should be allowed to pay only for the features and endpoints you need.
JumpCloud, for example, provides multiple pricing options that allow organizations to select the solutions they want for as many users as they need.

The Best Open Endpoint Management Systems of 2023
So here are our top three open endpoint management systems of 2023.
1. JumpCloud Directory Platform
Strictly speaking, JumpCloud isn’t open source since its source code is proprietary. However, it leads a new generation of endpoint management systems, thanks to its revolutionary approach of focusing on users in addition to devices.
This approach positions it to be the best fit for heterogeneous work environments as it helps users have seamless access to the resources that they need irrespective of their device or location.
A few upsides to JumpCloud besides the ones pointed out above are that organizations can implement a Zero Trust security approach with the tools that the platform provides such as MFA and Password Manager.
Also, admins can consolidate their tool stack and beat down the attendant costs that come with using several tools that can be replaced with one.
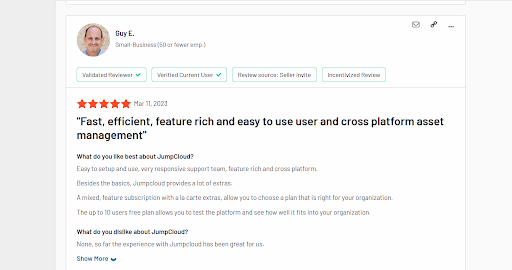
Lastly, users don’t have to bother with the headache of remembering passwords for different devices because JumpCloud uses a single set of credentials for logging in. A bonus to this is that when integrated with JumpCloud’s SSO, they can access other applications and resources under the same conditions.
2. Wazuh
Wazuh is a cloud-based and free open source endpoint management system that is primarily focused on security capabilities. Its main functions include monitoring, detecting, and providing alerts about security events.
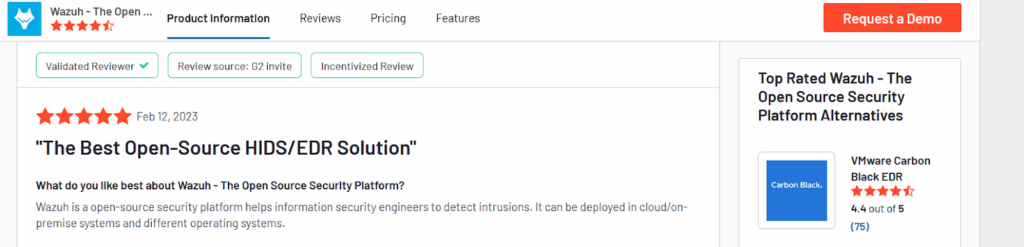
Wazuh also monitors file integrity by detecting changes in file ownership, attributes, permissions, and content. With its assessment tool, Wazuh finds weak spots in assets and helps admins tighten them up before attackers exploit them.
Also, Wazuh provides compliance management features such as improved security controls, log analysis, and incident response, which help organizations to meet regulatory requirements.
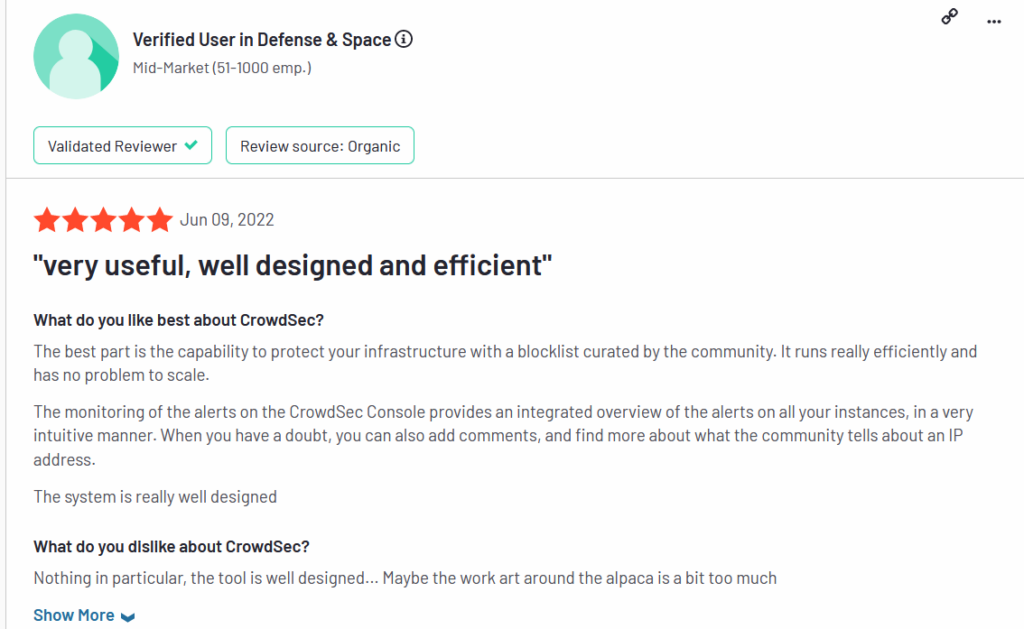
3. CrowdSec
CrowdSec is another open source security solution designed to protect servers, containers, and virtual machines from various types of attacks.
It works by detecting and blocking suspicious traffic that may be trying to get access to a server through brute force, HTTP attacks, website scalping/scrapping etc. It also registers IPs that it recognizes as threats, as well as those pointed out by other CrowdSec users, and denies them access to servers on which it is running.
CrowdSec is an easy-to-set-up solution that requires minimal configuration. Its greatest advantage, however, lies in its community support. Not only does its community contribute new features, but it also actively shares threat intelligence by reporting dangerous IP addresses. This improves the detection capabilities of the platform’s “bouncer” and helps it shoot dangerous IPs on sight.
Jump Ahead with JumpCloud
Open endpoint management systems provide the tools that IT admins need to deploy and enforce network-wide policies on devices.
JumpCloud stands out as the device-agnostic solution that helps admins manage users from a single, unified platform. Besides flexibility, it offers the tools needed for organizations to unify their IT stack with MFA, SSO, MDM, identity lifecycle management and more. Are you one of the 85% of IT leaders who say they’re adding technologies faster than they can productively use them? If so, we invite you to sign up for JumpCloud today and become the true ringmaster of your digital circus.




