
We frequently hear this question from companies: “We are shifting our business to the cloud and leveraging Microsoft Office 365. Do I need Active Directory (AD) if I have Office 365?”
You don’t need to continue to leverage Active Directory as you make the move to the cloud. You have the opportunity to reimagine your infrastructure to meet modern IT requirements by:
- Making identity the new perimeter.
- Making devices a secure gateway to resources.
There’s no obligation to continue using AD if you’re migrating IT management to the cloud. Cloud migration can be a confusing topic and there have been some big changes in IT. Microsoft’s identity management plans and licensing can be difficult to understand and are centered around Azure Active Directory (AAD), which is the user management substrate for Office 365 (O365). Microsoft has a wellspring of cloud services that flow from AAD, and the options may not be clear. What is clear is that Microsoft favors cloud-based authentication using its platform.
This article outlines Microsoft’s way of doing things versus an open directory approach and how IT teams benefit from the freedom to migrate away from O365 or Microsoft, or to select the subscription that works best for them without paying for unnecessary add-ons.
Active Directory and Office 365 Are Evolving
Active Directory is Microsoft’s on-prem identity management software that has been used for just about two decades now (it was released in early 2000). It dominated as the de facto system to manage Windows® machines, and gave Microsoft a strong grip on the market. As a result, Active Directory is the only directory service that many IT admins have experience with.
Microsoft developed AAD in response to a shift to the cloud. This product doesn’t share the same code base, and is largely meant to serve as a complement to existing on-prem AD implementations. AAD’s highest cost premium plan extends AD with identity protection and governance and both of its premium tiers integrate cloud identity with legacy Windows apps. Hybrid integrations may meet the requirements of small and medium-sized enterprises (SMEs) that have a need for AD, but it otherwise entwines SMEs more deeply into the Microsoft stack.
It’s also possible to leave AD behind. AAD’s not a replacement for AD on its own, but it can serve as a standalone directory when it’s paired with several SKUs of add-on Azure services or Microsoft 365 plans. However, this migration isn’t 1:1. For instance, groups work differently in AAD. Concepts such as Organizational Units are replaced with Administrative Units in AAD and tenant-wide management. This shift can be difficult and compel SMEs to dedicate significant resources to AAD/AD migrations. Admins often require consultants for this transition.
These are the available AAD plans (note that full AD integrations require Premium plans):
Azure AD’s (AAD) Tiers
AAD Free Tier
AAD’s free tier provides single sign-on (SSO) for SaaS applications using your Microsoft identities with multi-factor authentication (MFA).
It offers basic reporting on their substrate identity management solution as well as security and usage reports. It leaves out group assignments, omits custom conditional access rules, and limits how users can be provisioned. It doesn’t provide device management, which leaves admins without device management for endpoint security posture (outside of a hybrid AD configuration). The Free edition won’t work with Microsoft Sentinel, Azure’s security information and event management (SIEM) platform.
AAD Premium 1 (P1) Tier
Premium (P1) adds the ability to configure Intune, provisioning for Windows devices, more advanced MFA configurations, conditional access policies, end-user self-service, advanced group management, and more thorough alerts and reporting.
Azure AD Password Protection is also fully enabled versus limited in the Free edition, but it doesn’t extend to AD. Other features are intended to enable hybrid scenarios for on-premises domain controllers that aren’t possible with the free edition.
Microsoft obligates its customer to adopt its Edge browser in order for its conditional access policies to work.
AAD Premium 2 (P2) Tier
Premium 2 (P2) includes all of the features of P1 but adds identity governance features including risk-based conditional access policies, conditional access based on device state or location and group, privileged identity protection, Windows Defender for Cloud Apps, and more. Privileged Access Management (PAM) to manage, control, and monitor access administrative roles is only available in this SKU, and only this SKU protects AD against identity compromises.
Security and compliance reporting is more extensive to audit sign-ins, user risk, and abnormal activity. It’s possible to integrate with SIEMs, perform access certifications and reviews, and investigate risk events. Lifecycle Workflows, a beta lifecycle management service, is also included. P2 is necessary in order to apply identity governance to external directories/identities.
If all of this sounds like too much “stuff,” it just may be. P2 is an enterprise-grade solution that could contain more extensive features than an SME requires or has the capacity to implement and use. You could find yourself paying for services that you don’t need to get the one that you do. The breadth of P2 is significant, and hybrid AD configurations can become expensive.
AAD Can Be a Tollbooth for Google Workspace/Cloud
Suppose you decide to drop MS Office and adopt an alternative such as Google Workspace, but you like using AAD as your directory (maybe it ties back to your old on-prem AD rack). AAD is not all inclusive when it comes to integrating with non-Microsoft identities; Microsoft charges extra to manage external identities (with more charges for some authentications). Entra is its solution to apply enterprise-grade identity governance to external identities. This means you’ll pay Microsoft a premium if you decide to manage another directory using its AAD/Entra services.
It’s possible to use AAD for user provisioning and SSO for Google Workspace, but there’s configuration involved. The AAD ecosystem, by default, tethers SMEs to MS Office. AAD is in effect replicating AD’s legacy lock-in. Here’s the billing model for AAD External Identities.
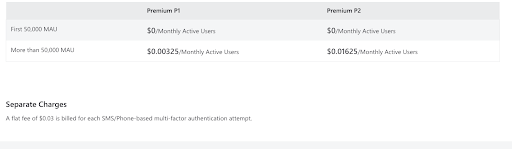
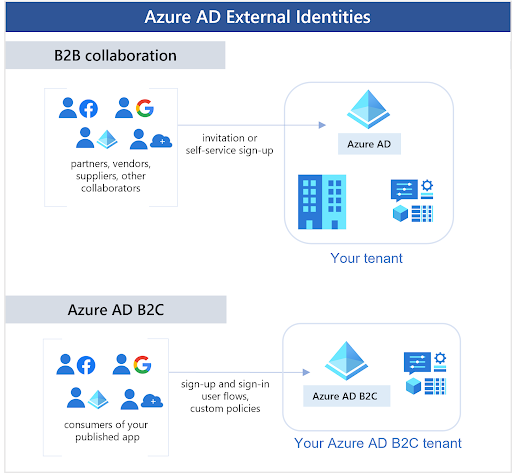
Microsoft permits federation with Google identities (for use on its sign-in pages) for the express purpose of setting up guest users to access Microsoft resources such as O365. AAD’s B2B collaboration places Microsoft apps and resources at the forefront.
Intune Is Required for Device Management
None of the AAD plans include Intune, Microsoft’s device management service. It’s only available as an add-on, per user, per month, or bundled with premium Microsoft 365 plans. AD manages Windows devices, but it cannot manage Android, Apple, or Linux based services. Customers have observed usability issues such as 8-hour polling for policy refresh internals.
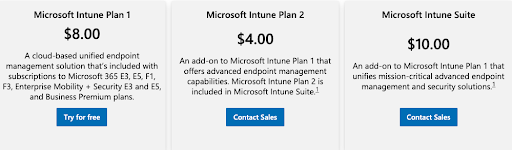
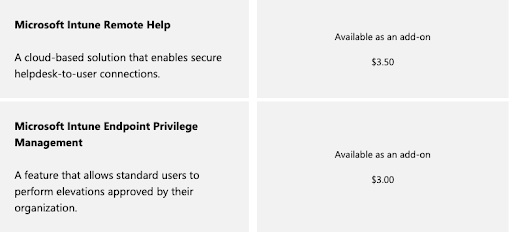
If you’re solely focused on leveraging Azure and don’t need system management for Linux® and macOS® systems, cloud servers at AWS®, Google Workspace integration, or any number of non-Microsoft solutions, then AAD may fit your requirements. However, you’ll pay more in the future if those requirements change. There is no AD equivalent within the Azure ecosystem, as evidenced by the vast expanse of Azure’s identity, device management, and security services.
Legacy Office 365 Licensing
It’s important to note that some legacy Office 365 plans only include AAD’s Free tier, which limits what’s possible for device management and more.
For instance, Office 365 E3 doesn’t include an entitlement for Intune and P1. IT admins must change their license, which can be confusing. M365 plans aren’t the same as O365 plans, and the licenses are also different.
Bridging the Gap with an Open Directory Platform
Microsoft isn’t the only directory option, even with O365. IT stacks have become more heterogeneous with devices and apps from other best-of-breed platforms and vendors. SMEs will have to dedicate significant time and money to migrating AAD to AD, which can also serve as an inflection point to pivot away from being a purely Microsoft shop (while still keeping O365).
That’s where JumpCloud’s open directory platform comes in. As a SaaS-based cloud directory service, you don’t need to have both Active Directory and Azure AD. You can leverage JumpCloud as your identity provider (IdP) and connect it to Office 365, which integrates with Azure AD. Or, save your budget with the Free tier of AAD and federate identities to JumpCloud.
This connection allows you to provision, deprovision, and sync to Office 365 from JumpCloud, which is ultimately a tight integration with Azure AD. This integration allows you to shift your business completely to the cloud, rather than have one foot in the cloud and another on-prem. Note: JumpCloud integrates with AD to extend its capabilities if that’s right for you.
Modern organizations depend on their Workspace and/or O365 implementations — after all, those solutions are core productivity solutions. The challenge is how to effectively manage those resources, particularly users and what they need to access. Creating users and managing them in Workspace or O365 results in a silo, and you’ll end up constructing a number of “mini directories” rather than a centralized identity and access management (IAM) platform.
O365 Without Microsoft Lock-In
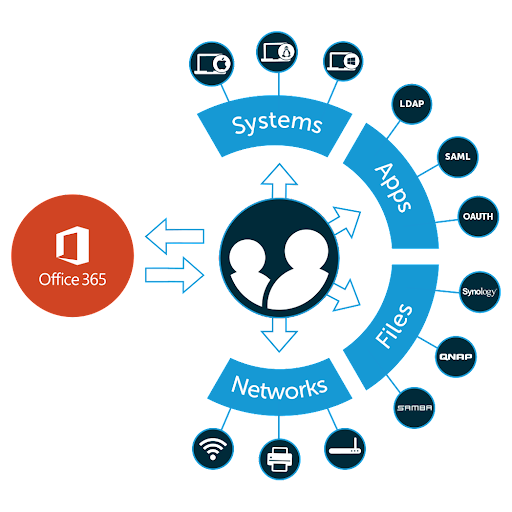
Organizations that are considering Office 365 don’t need AD, and it’s not necessary to pay for Microsoft’s Premium subscriptions and add-ons. Rest assured, you can make the move to O365 without being locked into Microsoft’s ecosystem of Azure subscriptions. JumpCloud unifies identity, access, and device management capabilities, regardless of the underlying directory, authentication method, or device ecosystem. The platform delivers frictionless access and authenticates users whether they use biometrics, digital certificates, passwords, or SSH keys.

The JumpCloud platform treats identities as the new perimeter with integrated device management and delivers secure, frictionless access to your resources (even O365 and Google). JumpCloud also ensures that every resource has a “best way” to connect to it.
For example:
- Servers use SSH keys, which are more secure than passwords
- Cloud LDAP with platform-wide MFA
- Passwordless certificates can secure cloud RADIUS Wi-Fi access
- Web applications use SAML and OIDC for authentication
- Optional conditional access rules (CA) for privileged access management
- JumpCloud’s decentralized password manager is an add-on for scenarios where SSO costs too much or isn’t available
In another departure from Microsoft, JumpCloud’s pricing is workflow-based, versus SKUs of gated off features that can raise costs. Identities are managed, with devices as the gateway, whether you prefer MS Office or opt to try Google Workspace.
A Secure Identity Lifecycle
In addition, JumpCloud groups leverage attribute-based access control (ABAC) to automate entitlements. ABAC is a more mature approach to user lifecycle management than AD, which includes manual processes that increase the possibility of mistakes, stale users, or over-provisioning. The platform can either send suggested changes or can be set to become fully automated. AAD defaults to role-based access control, which isn’t automated, and permissions are assigned. Microsoft only provides its Dynamic Groups for P1 or above.
Device Management Is Included
Fortunately, there’s no need for additional device management subscriptions such as Intune. JumpCloud provides standard integrated reporting, cross-OS device management with GPO-like policies (such as full disk encryption), remote assistance, and more. An optional universal patch management subscription keeps operating systems and browsers up to date, in defense against zero day attacks and potential software supply chain risks.
Try JumpCloud’s Open Directory Platform
Give JumpCloud’s open directory platform a try for free today by signing up for a free demo. Additionally, if you need some technical information, be sure to check out our Knowledge Base or drop a line to one of our product experts.





