Zero Trust (ZT) has risen in popularity over the past few years. Not only does it improve your company’s security, but it also lends itself well to the remote work environments many of us are now facing. But before you can implement Zero Trust in your clients’ (or your own) business, you need to know where you’re starting from.
That’s where our Zero Trust Assessment Tool comes in. Use this tool to show your clients where they currently stand on their ZT journey, and where they have opportunities to grow in the future.
What Is Zero Trust?
Zero Trust is a security model that, while around for a while, was popularized with the growth of remote work, because it relies on maintaining security, regardless of where the resources live. The framework is based on the concept of “trust nothing, verify everything.” Basically, all identities must be continually authenticated and verified while accessing organizational data and resources.
As an MSP, the most important thing to understand is that Zero Trust isn’t a product, but a method of approaching security. The concept centers around the idea that employees should have the lowest level of security and identity clearances necessary to do their jobs — and no more. As such, implementing Zero Trust should be understood as a journey, not a destination. And any good journey has pivotal milestones along the way, marking successes and helping identify areas of priority.
What Is the JumpCloud Zero Trust Assessment?
This assessment is designed to discover which stage of the Zero Trust journey your clients are in, by answering a series of questions about their current IT and security posture. The tool helps you, their trusted advisor, establish their current baseline, and provides tips on how to get to the next stage within the framework.
- Time investment: Expect the assessment to take 5-10 minutes to complete.
- Questions: The questions will ask about current identity and access management strategies, device management policies, and security strategies. You must answer every question honestly and completely for accurate results.
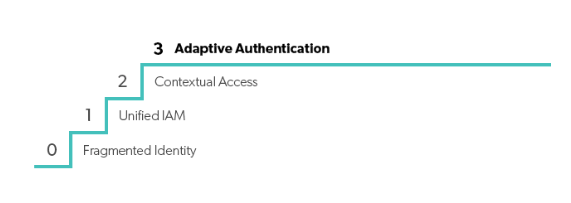
- Results: The assessment will give you a score based on the following stages:
- 0: Fragmented Identity
- 1: Unified IAM
- 2: Contextual Access
- 3: Adaptive Authentication
Don’t worry about these scores just yet — we’ll go over what they mean in the next section.
How to Use the ZT Assessment Tool
The assessment shows you what stage of Zero Trust your client’s organization is in based on their current identity, device, access management, and security strategies. It also serves as an objective measure of their security posture that can start the conversation around upgrading their tech stack.
Step 1: Use the Assessment to Begin the ZT Conversation
If you’re working on selling a Zero Trust overhaul to your clients, using the Zero Trust Assessment Tool is a great way to start the conversation.
Instead of simply telling them they need to upgrade their security practices, beginning with the assessment to gauge their current standing gives you a tangible score to work with, and helps them conclude they need increased security on their own.
Talk to your clients about their current security posture, and where you see room for improvement in their strategy. There is always more to be done from a security perspective — especially if a business has yet to implement Zero Trust.
Step 2: Take the ZT Assessment with Your Client
Once the assessment has been introduced to your clients, use it to guide your audit of their current security posture. Walk through the assessment together, so you can help them objectively and honestly answer the questions.
For example, one of the assessment questions is, “Where have you focused your security controls?” In a MSP-client relationship, your client may not be able to answer this more technical question by themselves, since you have managed most of their tech stack. But you can step in to offer your expertise in explaining to them how their current framework is set up, to help them choose the most accurate answer.
While some questions have “not sure” as an answer option, choosing more definitive answers will make for the most accurate end score. That’s why your experience as an MSP is so critical in this step.
Step 3: Make Recommendations Based on Assessment Results
Once you’ve answered all the questions in the assessment, you’ll receive a final security stage of 0, 1, 2, or 3, with 0 being the lowest Zero Trust score and 3 being the highest.
0: Fragmented Identity
This is where most organizations that don’t have a Zero Trust strategy score. Note that it doesn’t mean these businesses have no security; just that there is work to be done at the foundational level to grow in their Zero Trust security journey.
The most common cause for a “0” score is that the organization is still using on-prem solutions, like Microsoft Active Directory. In the past, this was the gold standard in security, but with the growth of the remote workforce and cloud-native software, it’s become easier than ever for cybercriminals to infiltrate these legacy systems. Implementing Zero Trust means upgrading to a security framework that better fits our evolving environments.
1: Unified IAM
To move from 0 to 1, the organization must have an evolved identity and access management (IAM) strategy that centers around a unified identity storage solution. Managing all identities in one location gives cybercriminals fewer opportunities to attack, and applying additional security strategies like single sign-on (SSO) and multi-factor authentication (MFA) makes for an even more secure environment.
2: Contextual Access
To move from 1 to 2, your client has to layer their IAM strategy with conditional access policies. Instead of allowing any logged in user to access resources, these policies look for any anomaly or unusual activity that may suggest a false identity. If abnormalities are found, the user has to re-verify their identity before accessing the resource.
These policies also automatically block access to verified users attempting unauthorized activities, making for more seamless security. Stage 2 also includes automated provisioning and deprovisioning, so you can quickly grant or revoke privileged access as needed.
3: Adaptive Authentication
Stage 3 is the gold standard in Zero Trust evolution. It’s the stage all MSPs should strive to get their clients to, because it represents the utmost in security, safety, and efficiency. The key to reaching stage 3 is having a security solution that can evolve and change in response to our changing business environments. This stage also includes implementing features like adaptive authentication and risk-based access policies.
The assessment will give you some tangible suggestions of how to improve the score. But as an MSP, you can provide even more personalized solutions based on your tech stack recommendations and your SMBs’ unique needs. This positions you as an experienced and valuable guide, and sets the groundwork for a Zero Trust overhaul.
Next Steps for Zero Trust Client Implementation
Encouraging your clients to implement a Zero Trust framework sets them up for security success, and positions you as an educated, experienced, and trusted MSP. This assessment tool can help you start the conversation, but it’s only the first step in a Zero Trust implementation.
To help you get to the next steps, we recently released a free whitepaper, Zero Trust for MSPs. This roadmap explains what Zero Trust is (and isn’t), the key benefits of using the framework, how to package and sell it to clients, and the three critical steps to implementation. The resource also includes suggestions for further reading, and free downloadable templates for use in your business. Download the whitepaper today.



