Updated on December 8, 2025
This article was also contributed by Samantha Morgan, Senior Product Manager at JumpCloud
AWS is the largest cloud provider in the world. According to Synergy Research Group, AWS has a 32% market share of the cloud provider (IaaS or infrastructure as a service) industry. For organizations managing user and group permissions, access to accounts, and resources, AWS offers two services: AWS Identity and Access Management (IAM) and AWS IAM Identity Center.
There are several similarities between the services: both oversee access management, ensure their users only have entry to the resources they need, and can be centrally managed with an external identity provider (IdP). Given the similarities, why would an organization choose one over the other?
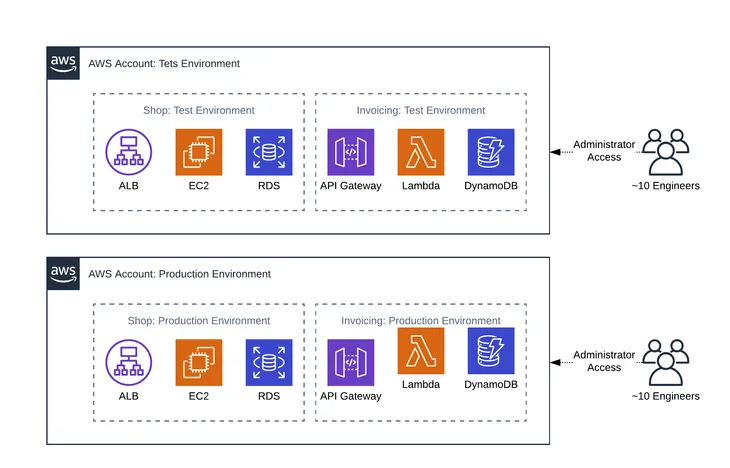
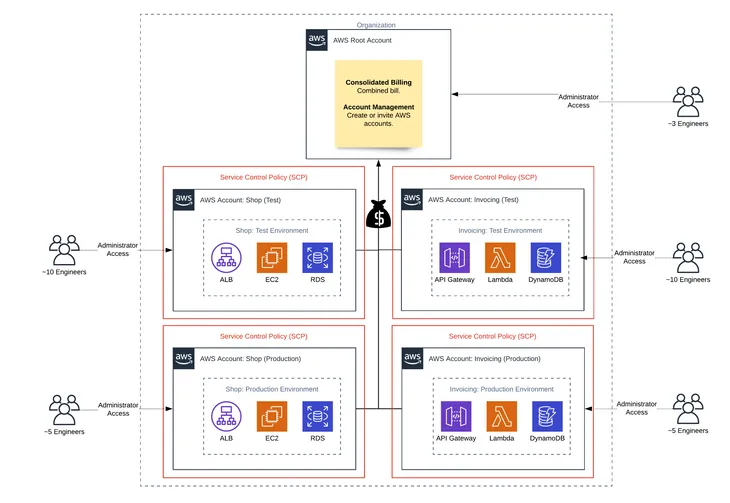
The following provides an example scenario to identify the best use case for each service. Admin Bob must decide whether he should utilize AWS IAM or AWS IAM Identity Center to manage his AWS resources. In this particular scenario, he manages a group of 20 engineers who are accessing 10 AWS accounts.
AWS Terminology
Before jumping in to decide which one Bob should choose, let’s first define a few key AWS terms that are vital to Bob’s decision. The definitions were taken directly from AWS and the diagrams below from cloudonaut.
Account
An AWS account is a container of AWS resources. Using multiple AWS accounts is a best practice for scaling environments, as it provides a natural billing boundary for costs, isolates resources for security, gives flexibility for individuals and teams, in addition to being adaptable for new business processes.
Organization
An AWS Organization is a collection of AWS accounts that can be organized into a hierarchy and managed centrally. Organizations help to programmatically create new accounts and allocate resources, and simplify billing by setting up a single payment method for all accounts. In addition, AWS Organizations is integrated with other AWS services so admins can define central configurations, security mechanisms, and resource sharing across accounts.
User
An AWS user is an AWS identity created directly in the AWS IAM or AWS IAM Identity Center admin console that consists of a name and credentials.
Federated User
A federated user is a user identity that is created in and centrally managed and authenticated by an external identity provider. Federated users assume a role when accessing AWS accounts.
Group
A group is a collection of users. Groups let admins specify permissions for multiple users, which can make it easier to manage the permissions. Any user in that group automatically has the permissions that are assigned to the group. Any user removed from the group will lose those permissions. For instance, if Bob places a new employee into the Engineering group, which has access to the Lambda and DynamoDB production account, then the new employee will also be granted access to the resources in that account.
Role
A role is similar to a user in that it is an AWS identity with permissions and policies that determine what the identity can and cannot do in an AWS account. However, instead of being uniquely associated with one person, a role is intended to be assumable by anyone who needs it. A role does not have standard long-term credentials such as a password or access keys associated with it. Instead, when a user assumes a role, it provides them with a set of temporary security credentials for that session. Admins can use roles to delegate access to users, applications, or services that don’t normally have access to those AWS resources.
AWS IAM Identity Center Permission Set
A permission set defines the level of access a user has to AWS resources within an AWS account. For Bob, once he provides access to the necessary accounts in AWS IAM Identity Center, he can use predefined or custom permission sets to control the level of access.
What Is AWS IAM?
AWS Identity and Access Management enables admins to manage access to AWS services and resources within an AWS account securely for what it calls “entities” — IAM users created from the AWS IAM admin console, federated users, application code, or another AWS service. Admins can create and manage AWS users and groups directly, and use permissions to allow and deny their access to AWS resources. Admins create roles to manage access for all other entities.
For instance, if Bob wants to control who has access to a specific S3 Standard bucket, then he can create a role and add permissions to that role to control which users have access.
What Is AWS IAM Identity Center?
AWS IAM Identity Center also manages access to AWS services and resources. The difference between AWS IAM and AWS IAM Identity Center is that the latter manages access for all AWS accounts within an AWS Organization, as well as access to other cloud applications, e.g., Salesforce.
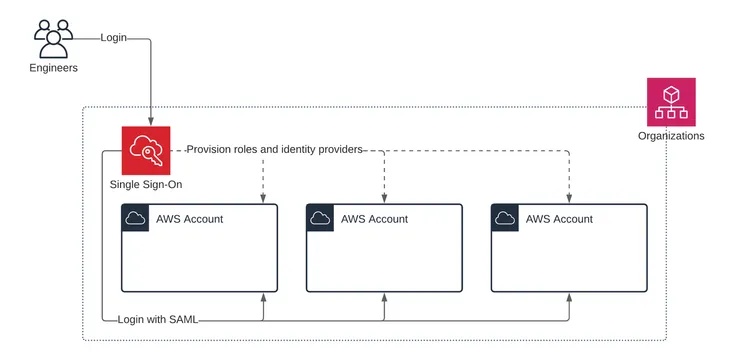
AWS IAM Identity Center includes a user portal where end users can find and access their assigned AWS accounts, cloud applications, and custom applications in one place.
AWS IAM vs. AWS IAM Identity Center
Bob now understands the specific AWS terminology and what each service offers. He is ready to explore the differences between using AWS IAM and AWS IAM Identity Center for managing access to AWS resources. Bob will compare what he would need to do in each service to accomplish the task of adding new accounts and granting access to specific AWS resources within those accounts to his team of engineers. This comparison will allow Bob to make a final decision about which service can best meet his needs.
Adding Accounts
Bob has 10 AWS accounts. He needs to create two new AWS accounts, a test account and production account for Lambda and DynamoDB, to isolate his environments and ensure proper access.
Using AWS IAM, Bob will need to create two new accounts following the signup process.
Using AWS IAM Identity Center, Bob will need to open the AWS Organizations service and add two new accounts from there.
Configuring Identity Providers
Bob is using JumpCloud as his single identity provider.
AWS IAM supports setting up multiple identity providers per account. Using AWS IAM, Bob will need to log in to each AWS account and configure JumpCloud as the identity provider.
AWS IAM Identity Center only supports a single identity provider. Using AWS IAM Identity Center, Bob configures JumpCloud as his identity provider once, and JumpCloud becomes the identity provider for all his new and existing AWS accounts.
Defining Permissions and Roles
Bob needs to define the permissions and policies that govern what his users can and cannot do within an AWS account and to which AWS resources they have access. He will need to do this from the admin console of the service he is using.
Using AWS IAM, Bob will need to log in to each AWS account and create a new role(s), or from one AWS account, Account A, create policies that allow a role to be assumed in another AWS account and to control the level of access to S3, Lambda, and/or CloudWatch in Account B, for example.
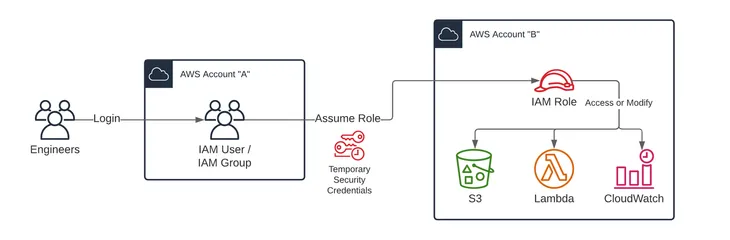
Using AWS IAM Identity Center, Bob can reuse existing AWS IAM Identity Center policies and permission sets. Policies and permission sets are defined at an organization level and are applied to groups or users at the account level. If the ones that are already defined are not applicable to these new accounts, then he can create new ones in the AWS IAM Identity Center admin console.
User and Group Provisioning
Using AWS IAM, federated users log in as a role not as their specific user identity. Bob doesn’t need to create users or groups. If he has a specific need to create a user account that is not managed by an identity provider and can log in as a user identity, he will need to create a user in AWS IAM directly. If he has a use case for having several AWS users, he could create groups to organize these users and make assigning access to these users simpler.
Using AWS IAM Identity Center, Bob can configure a SCIM integration and have users automatically created in AWS IAM Identity Center when they are created in his identity provider. Otherwise, he would need to create users and groups manually within the AWS IAM Identity Center admin console.
Assigning Access
With the roles defined, Bob is ready to assign roles to his users and groups.
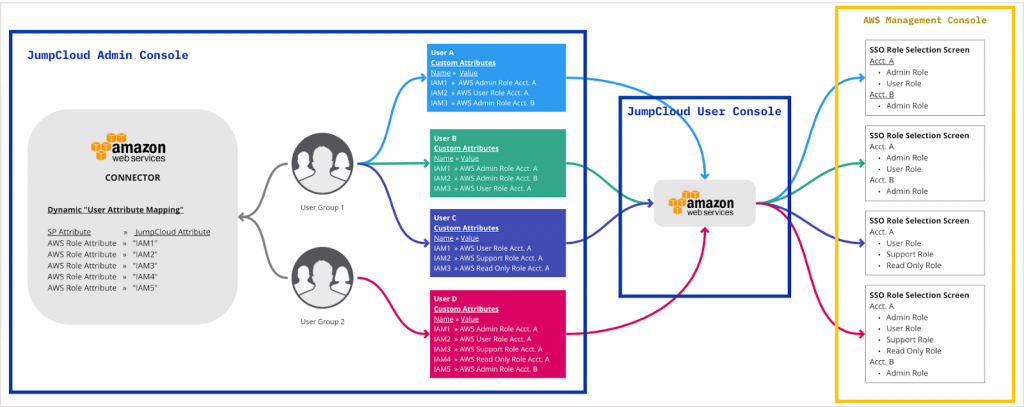
Using AWS IAM, roles are assigned to federated users using attributes in the SAML assertion for each AWS account. For each role, Bob will need to define a role attribute at the connector, group, or user level in JumpCloud. He will need to get the Amazon Resource Name (ARN) for each account and each of the roles he defined and construct the SAML attribute value from the role and account ARNs.
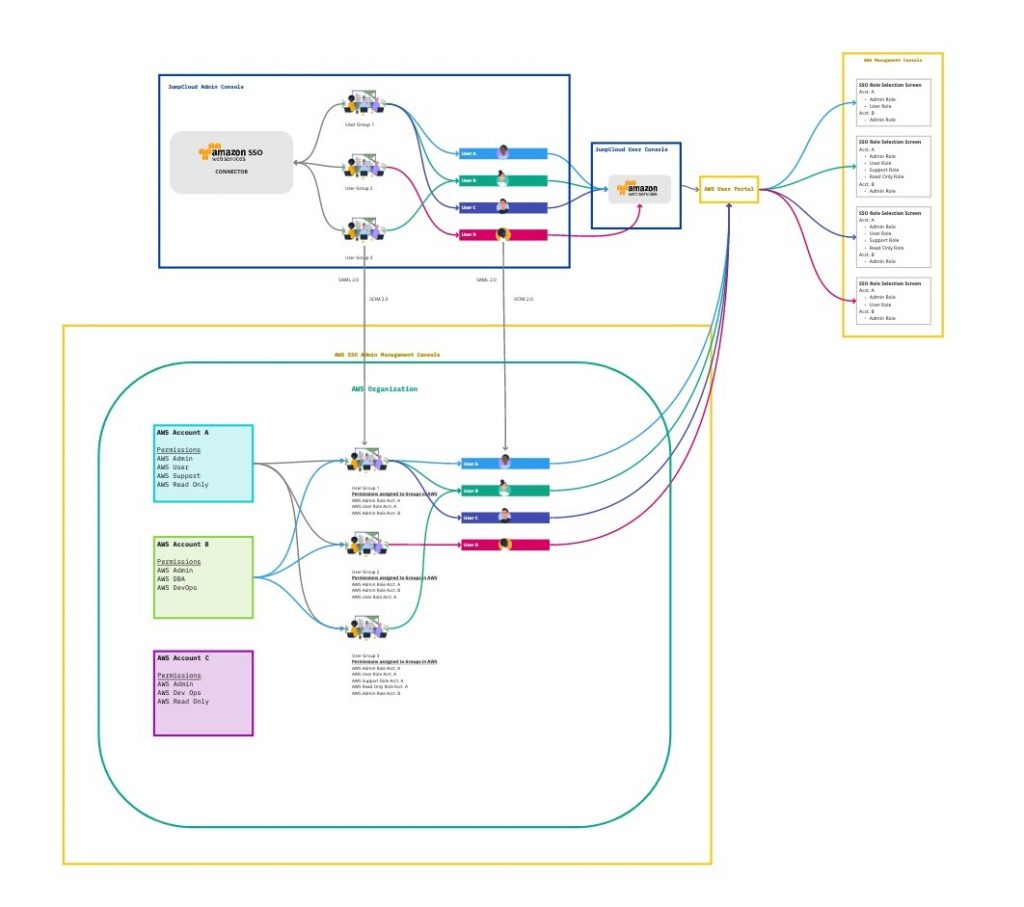
Using AWS IAM Identity Center, roles are assigned through group membership or directly to the user for each AWS account. Once the groups are created, Bob will need to assign permissions to each group in each account. He is able to further refine who within the group gets the permissions using tags, which use specific user attributes such as department or role, to determine if the permission should be granted.
Those permissions will then be inherited by users who are members of the group and meet any additional conditions of the permission(s). If there are certain users who need specific privileges in addition to what they inherit from their group, he can assign permissions to those users directly within each account.
What’s Best for Bob?
Bob is ready to make his decision. Bob chooses AWS IAM Identity Center over AWS IAM.
AWS IAM Identity Center is ideal for managing multiple AWS accounts. With his Engineering group set up in AWS IAM Identity Center, Bob can now grant his users access to the accounts they need at the user or group level.
Within the AWS IAM Identity Center service, if Bob wants to grant his Engineering group access to the production account for Lambda and DynamoDB, then all that he would have to do is select AWS accounts, check the account box, and assign at either the group or user level. To further enhance the type of access his users or groups have, Bob will have to specify the permissions levels. This includes using existing permissions, i.e., Power User, or creating a custom permission set.
An added benefit of AWS IAM Identity Center is that any new user added to the group will automatically be granted the same level of access as other members in the group. If Bob adds Mary Adams to the Engineering group, then she will also be granted Power User access to the production account for Lambda and DynamoDB.
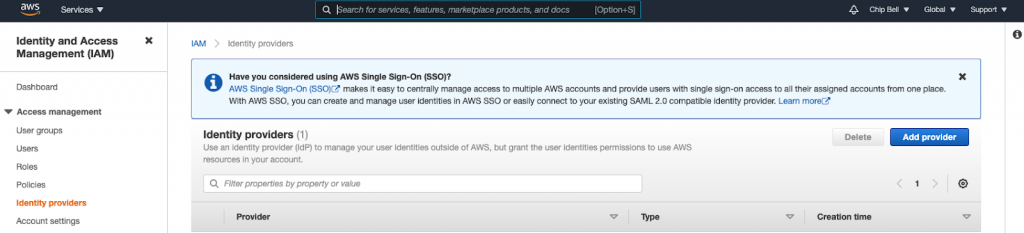
Interestingly, AWS is also pushing their users to switch from AWS IAM to AWS IAM Identity Center. Within the identity providers tab of AWS IAM, Amazon has a banner promoting AWS IAM Identity Center.
How Can JumpCloud Help?
As the example above illustrates, for admins, such as Bob, they can easily manage their AWS IAM and AWS IAM Identity Center users and groups from JumpCloud. All they have to do is declare JumpCloud as their identity provider and connect their IAM and/or SSO groups to their JumpCloud groups.
For AWS IAM Identity Center, JumpCloud has group management integration that will simplify onboarding and user management. This will allow admins to manage their AWS IAM Identity Center groups from JumpCloud.
In the case of Bob, once he provides the account and application access at the group level in AWS IAM Identity Center, then any user he adds to the Engineering group in JumpCloud will automatically be granted entry to the Engineering group in AWS IAM Identity Center, with access to the same accounts and applications as the existing engineers. If Bob has a new engineer joining his company, then all he has to do is create their identity in JumpCloud and add them to the Engineering group in the Admin Portal.
This will create their identity in AWS IAM Identity Center and place them in the Engineering group, granting them similar access and permissions as their peers.
Evaluate JumpCloud Free Today
If you’re new to JumpCloud and interested in learning more about how the platform supports SSO with AWS, then start a free trial of JumpCloud today!
Frequently Asked Questions
What is the difference between IAM and IAM Identity Center?
AWS IAM focuses on managing access within individual AWS accounts, while IAM Identity Center oversees access across multiple AWS accounts and integrates with other cloud applications.
What is the IAM Identity Center?
The IAM Identity Center is a service that streamlines access management for AWS accounts and other applications, providing a user portal for single sign-on access.
Should I use the AWS Identity Center?
If you’re managing multiple AWS accounts or require centralized user management and permissions, AWS Identity Center is generally the better choice over AWS IAM.
What are use cases for AWS IAM Identity Center?
It’s particularly useful for organizations with a diverse user base accessing multiple AWS accounts or external cloud applications, simplifying user provisioning and access control.
How do I choose between AWS IAM and IAM Identity Center?
Consider AWS IAM if you’re dealing with a single account and need granular control; choose IAM Identity Center for broader, centralized management across several accounts.




