BEST PRACTICES
Why Your “Working” Productivity Suite is Costing You Time and Security
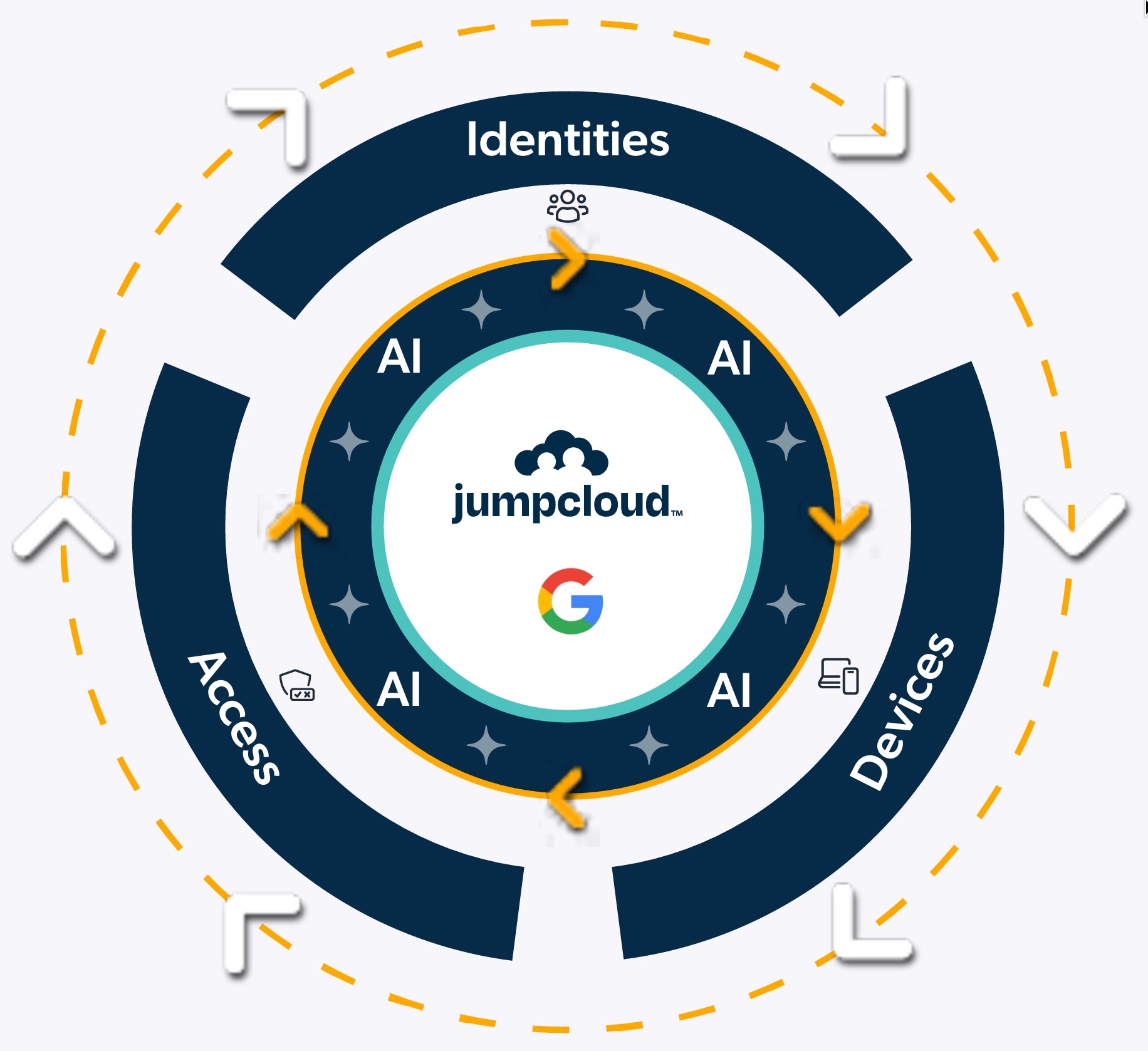
Stop patching the gaps! Discover the high cost of fragmentation and how true unification—like the JumpCloud/Google Workspace collaboration—creates a single, secure control plane for Zero Trust.