Work happens wherever the device and the person using it are located. Whether that’s a traditional office, home office, coffee shop, coworking space, or airplane tray table, IT leaders need to be able to secure the device and connect the user to their requisite resources through it.
How we approach security and the use lifecycle has also evolved. IT departments need more than just a new toolset to achieve the kind of fluid access control and device management required today — they need an entirely new architecture. This article explores how IT architectures have evolved and what organizations now need to meet the demands of the modern era.
Active Directory & the Domain
Microsoft’s proprietary directory service, Active Directory (AD), thrived in contained Microsoft ecosystems. In the past, on-prem domain controllers connected users to other resources on the network and managed on-prem Windows devices as well. This established a secure perimeter around organizational resources on local networks.
However, it was built in an era when a network was defined by the physical office building where employees worked. Despite its strengths in physical office spaces, AD is not a fluid architecture. It requires significant investments in hardware and on-prem networking, and it wasn’t designed for work outside the office. From the outset, IT admins had to retrofit it for workers on the road, like salespeople, which sparked the dawn of the VPN client.
The past several years have brought about a sea change in how IT works. The days of centralized, locally hosted IT are over. The tools and solutions that we use should reflect that reality. AD is no longer the best way to manage users and their access to resources, because it requires identity bridges and other add-ons to be a comprehensive solution. Those add-ons generate higher IT management overhead and increase potential cyberattack surface area.
Monopolistic Add-On Pricing
The current Active Directory ecosystem is best equated to a movie theater where your ticket grants you admission, but you’ll purchase more than you’d normally pay for at the concession stand to get everything that you want. An array of services ranging from complicated AD FS server farms, a flood of Azure AD licensing models, or Intune (which must be Azure AD joined or hybrid AD-joined) are now available as a multitude of add-ons that can be confusing to navigate and won’t support every environment, such as popular Linux distributions.
A different architecture now exists to eliminate the need for such AD add-ons, though.
A Boundless Domain: Remote & Flexible Working
Today, an organization might be all-remote all the time, or have entire departments that no longer work in-office. An organization might also face additional complexities associated with acquiring companies outside of its region or granting its partners secure access to shared IT resources.
Work from anywhere is now enshrined in how business is done, everywhere. Identity and access management (IAM), user lifecycle management, asset and device management, as well as patching and governance are the new frontier. Users work across devices and access many kinds of resources with their identity.
The current reality as seen in the news, and in our communities, demonstrates an incredible change of pace and the realization that world events no longer occur in isolation. We rely on the internet more deeply than ever, and the cloud is a mission-critical IT infrastructure that connects people to the resources they need to work.
This is especially pronounced in the business world where many companies are uncertain about how to respond to large-scale challenges (such as adopting a Zero Trust strategy) with limited IT resources.
Organizations need innovative architectures to support them — architectures that ensure business continuity in the face of change. The “domainless enterprise” employs IT architecture that’s fluid, flexible, and responsive. The domainless enterprise begins with how new users are on-boarded and persists throughout the entire user lifecycle, over many devices and shifts in roles and responsibilities.
It supports secure work from any location or circumstance. It also supports resource access that’s customized for each person based on their role and needs as well as the requisite security verifications that must be included every step along the way.
This architecture is user-centric, regardless of device, OS, or provider. IT needs to be able to secure and manage any device, whether it supports Windows, macOS, Linux, or even smart device operating systems like iOS and Android. This architecture meets individual IT resource needs while ensuring compliance for IAM and devices.
Modern IT is much more systematic than in the past: an IT admin tracks organizational assets, patches and configures systems, and continually manages access control. Some organizations also have compliance and reporting requirements, which must always be taken into account.
Control Your Identities
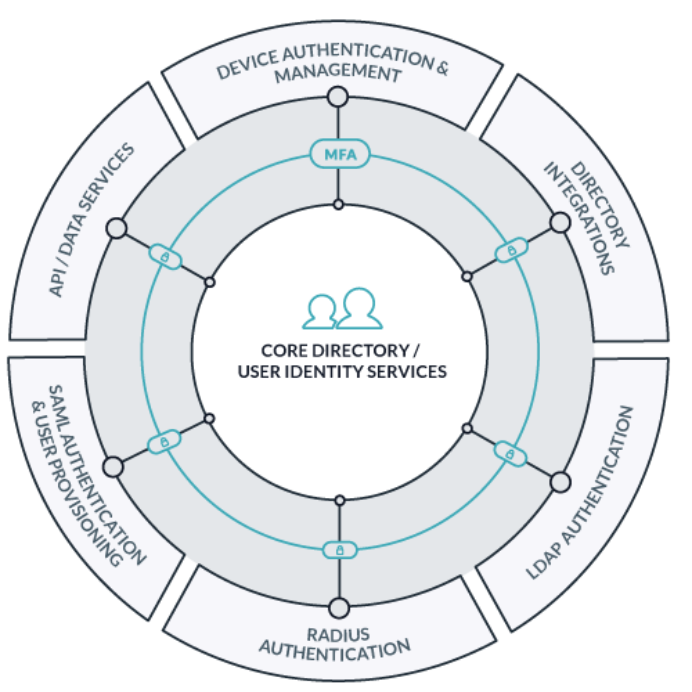
The heart of a domainless enterprise is a central cloud directory service, which serves as the hub for securely connecting users and their systems to the IT resources they need to accomplish their jobs. This may even include network devices within the IT department itself.
From a central cloud directory, IT needs only an internet connection to provision users to their devices and secure those devices, as well as provision users to all their IT resources, including SaaS apps and cloud infrastructure. This process may start by staging a new user in the directory and now may also include zero-touch onboarding where devices arrive ready for use.
From this same cloud directory, IT admins can control access, secure identities, manage and protect systems, and audit all access — all without the need for an on-prem domain controller.
How to Implement the Domainless Enterprise
Directory services for the domainless enterprise are entirely cloud-based and platform-agnostic. They perform as the authoritative repository for digital identities and can federate those identities everywhere they’re needed via an internet connection. This is also where rules, such as conditional access to IT resources, can be configured for even more robust access control.
The architecture has several components that are built for today’s IT workflows:
Device Security & Trust
This architecture relies on lightweight agent-based control of devices. A user should be able to log into their company-controlled device, secured with credentials and user-friendly Push MFA, and access their authorized resources with minimal friction. Via the agent, IT admins can configure the devices, lock down security with policies, and monitor data such as uptime and storage capacity — as well as immediately suspend access for any security reason.
Agents have root/sudo-level access at the OS level to push any command that IT requires to accomplish a task, or can operate as an Mobile Device Management (MDM) provider on systems that are managed that way. MDM establishes profiles and sends commands on both company-owned and BYOD devices, so security will always follow the user. Agents also deliver telemetry for reporting.
Patch management is an important integration to ensure that all devices remain up to date and within compliance before access is granted, without requiring additional servers to manage. Managing the devices users work from is a sensible step toward Zero Trust security.
User Identity Instantiation
Modern access control is built on top of user attributes. Permissions are no longer automatically granted with constructs such as nested groups; attributes deliver user-based determinations and reduce administrative overhead. For instance, an employee’s department or manager may change, so the system automatically recognizes and notifies IT that permissions should change.
This is made possible by importing or establishing attributes from any Identity Provider (IdP), even Active Directory. It’s also possible to utilize SCIM provisioning from your directory to scale your IT operations and more easily onboard user access to web applications. With this architecture, a user has one authoritative identity that IT controls, manages, and monitors.
From a central cloud directory, IT can federate that identity to:
- Resources, including SaaS apps; and single sign-on (SSO) provides hundreds of pre-built and custom connectors
- Cloud infrastructure such as AWS
- RADIUS network access points (using EAP-TLS with certificates)
- LDAP-reliant apps and devices
It can also sync with and manage changes between services like productivity suites (i.e., Google Workspace or Microsoft 365) that require user stores.
Learn more about the benefits of attribute-based access control.
This new architecture allows you to redefine the domain, which was previously limited to an office-based environment. It allows the new “domain” to stretch wherever employees perform their work, without the need for costly VPN connections or other networking solutions.
All an employee needs in this model is a device and an internet connection. Further, users only need to change their secure credentials in one spot — on their device — for virtually all their IT resources, which dramatically reduces the risk of an identity compromise through phishing. That’s especially true if integrated MFA strategically challenges the user where it matters most.
JumpCloud Helps Companies Grow
At JumpCloud®, we built the world’s first cloud directory service because we wanted to enable this domainless enterprise for all organizations. You can read more about the domainless enterprise in this whitepaper.





