The keys to an organization’s Bring Your Own Device (BYOD) policy live in the IT department, even when devices themselves are the property of employees or contractors.
BYOD models that allow users to select and own their work device of choice rather than receiving a dedicated machine purchased and managed by IT are becoming more and more popular, especially since opportunities for (and a desire to) freelance have skyrocketed and the global pandemic relegating many end users to their home offices is still ongoing. For this reason alone, there are benefits for businesses to implement a BYOD policy.
Even though the user is the device owner, IT still needs to control the device for its use as a work machine. In some BYOD workplaces, however, IT is constrained by their rights over personal machines.
But today, securing devices is too critical to put constraints on to protect employees. While traditional IT management solutions make a critical assumption that IT has full rights and control over the device, managing security on BYOD devices can be a significant challenge for IT admins, including a variety of BYOD risks that need to be addressed.
Check out our BYOD Statistics piece to learn more about BYOD adoption, impact on productivity, security concerns, and critical trends to be aware of.
BYOD Security Considerations
BYOD is a two-way transaction, where IT must respect parameters on an employee-owned device, and end users must adhere to certain rules that keep their device, and the resources they access on it, protected. The right way to align on this is drafting an organization-wide policy about the parameters of BYOD that:
- Make it clear what the organization can and can’t do with each device
- Assert the responsibilities that each device owner has with respect to accessing critical systems and data
In addition, there are factors organizations face that make BYOD even more complex:
- The need to support cloud and on-prem resources makes granting access to the right resources challenging
- Employees that work remotely or in hybrid work environments may connect via insecure networks
- Personal devices may not have the same (or any!) level of endpoint protection policies or software in place to protect against evolving threats
What can help employees feel more at ease around IT being able to secure their personal device?
Perhaps, a tradeoff: In exchange for IT being able to control certain things on their device, end users get a stipend from the organization for the use of their machine on behalf of the company. This can make BYOD more palatable to let IT put an agent on machines to secure them. This is just one example of a variety of other ways to implement a secure BYOD policy.
At the center of managing this, IT administrators have their work cut out for them when it comes to keeping users safe while working on devices the organization doesn’t own, while making sure users have secure and frictionless access to IT-managed resources so they can be productive.
The good news? JumpCloud makes it easy for admins to define and enforce BYOD security.
If you’re still weighing your options for a device use policy, BYOD, CYOD, COPE, and COBO are frequently discussed solutions.
Addressing BYOD Security with JumpCloud
IT’s main maxim in a BYOD culture is: prevent confidential corporate data from ending up on devices of unknown security postures that aren’t controlled by the organization.
JumpCloud’s cloud directory platform offers multiple capabilities, like Conditional Access, for IT admins to support BYOD initiatives and secure their environment by creating specific conditions that must be met by the user, their device, and the network on which they reside before they can handle critical data.
Control User Access to IT Resources
JumpCloud gives admins the ability to control access to devices, apps, files, and networks. In BYOD environments especially, secure resource access from devices should embrace the Zero Trust security mindset of trust nothing, verify everything. This allows you to tightly control how and who is able to access the resources you manage.
How do you implement Zero Trust device management? By building layers of security that you’re in charge of with Conditional Access Policies in JumpCloud. The Device Trust Policy is designed to give you authority over what devices are trusted and untrusted in your network, so you can even block BYOD devices from accessing certain applications in a security event.
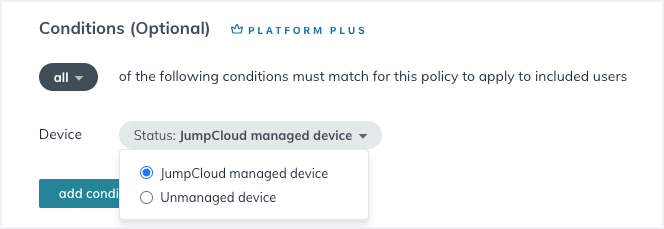
Know Every Device on Your Network
Admins in JumpCloud can authenticate user and device access via WiFi infrastructure (or, more commonly in remote work environments via a VPN), a key way to know exactly who is on your network. By leveraging JumpCloud’s cloud RADIUS functionality, each device requires network credentials to access the network so you know each device on the network and who owns it.
JumpCloud System Insights surfaces fleet-wide machine information for Mac, Windows, and Linux that updates in near real-time to keep admins appraised of device posture. This is critical data for admins to have access to in a BYOD workplace to ensure that devices are properly encrypted, have the right policies running, and more information specific to OS.
In addition, see what’s happening on JumpCloud-managed devices with Directory Insights, which presents device data you can drill down into to look at things like login attempts and authentications to track activity across your fleet.
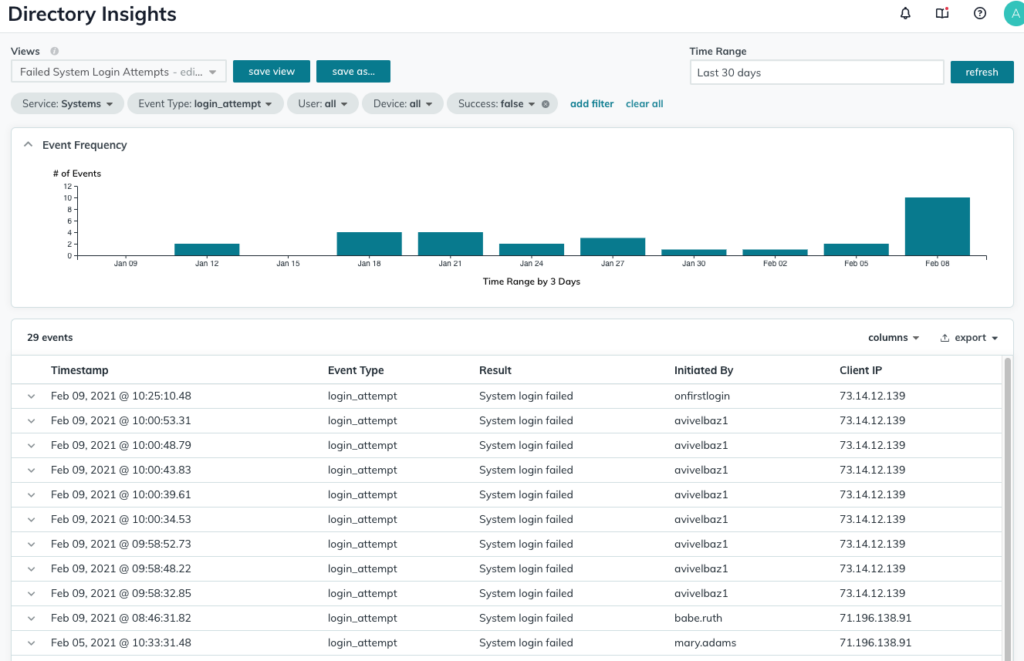
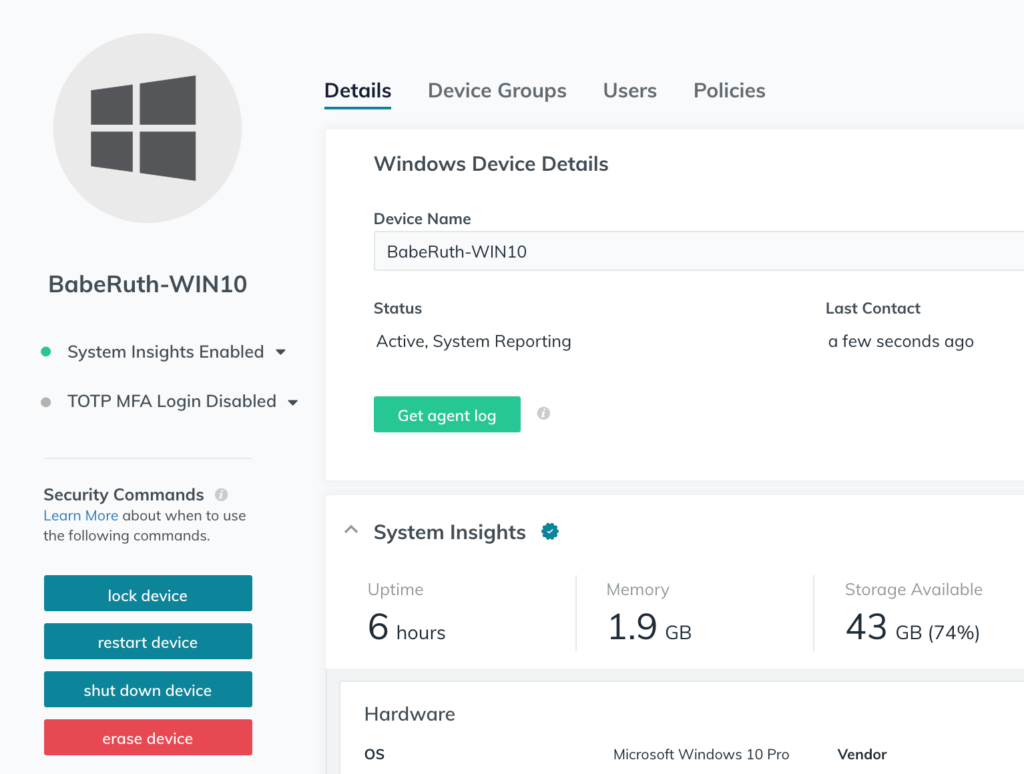
Be Able to Protect Corporate Data
In the most extreme situations, you need the ability to remotely wipe corporate data from a user’s device. Ideally, your organization’s BYOD policy will allow you to do this as a security measure. This is far less about malicious employees or contractors, and more about protecting devices that are stolen.
In these cases, admins should consider enforcing the deployment of company-managed agents onto personal devices if the level or type of access these employees, contractors, or freelancers need is high enough to warrant a more severe response to a potential security incident.
This would allow an admin to use functionality like JumpCloud’s security commands to address an event in which a device needs to be wiped to protect the data on it. You can do this by executing commands with scripts, or even more simply via point-and-click security commands for Mac and Windows computers from your JumpCloud console.
Embrace BYOD Without Sacrificing Security
BYOD is both an opportunity and a risk for an organization’s IT department. In many ways BYOD may even be necessary to keep the business growing. Leveraging the right technology that consolidates what you need to enforce security in a BYOD model is essential. JumpCloud can help you lock down your data and networks so that your business can enjoy the benefits of BYOD, and we’d be happy to demo that for you. Get in touch to let us know how we can help.




