We often hear the phrase, “Work on what is important, not necessarily urgent.”
IT organizations know this axiom all too well. In a business that is highly interruption driven and reactive, IT admins are craving a better way to control their work lives and the infrastructures that they manage.
Unfortunately, this is a massive challenge for virtually all IT organizations because end users are demanding tools and technology to make their lives easier; the business is searching for ways to increase speed and reduce costs; and security and compliance issues are a reality for every organization. As a result, there may be no place in IT where working on the foundation is more critical than in the identity management world. For that reason, this blog post will focus on the foundation of IT: the identity provider.

Why are Identity Providers Important?
The consequences of mistakes in the identity and access management strategy can be catastrophic. To add fuel to the fire, identity theft and breaches, compliance failures, and unprotected digital assets are more common than ever before. Unfortunately at the same time, the reality in this sector is that it is often easier to focus on the symptoms of issues rather than the root causes because it often solves the immediate pain.
Acquiring a web application single sign-on solution to solve the pain of end users accessing a wide range of SaaS applications is an easy example. Adding an LDAP server in AWS® to manage user access to Linux®cloud servers is another. Or, perhaps Mac® and Windows® systems go unmanaged because it is too difficult to implement Microsoft® Active Directory® in a modern, cloud forward environment. Of course, identity management didn’t use to work that way a long time ago. Nevertheless, with all of these heterogeneous IT resources and more at play, each generally requiring siloed management solutions, it is easy to see why a consolidated identity management platform (also known as, an identity provider) would be helpful.

Identity Management with a Traditional Identity Provider
The first step for any organization fifteen to twenty years ago was to implement the core identity provider. This, of course, was a much easier time because IT networks were homogeneous and under IT’s control on-prem. IT admins would implement Active Directory and they would have full control over a user’s access. This was a foundational element that enabled users to gain access to the IT resources they needed while the business had full control over who could access what. That identity was as core as the user’s badge to access the building.
As the IT landscape started to change, so did the way that users were granted access to IT resources. No longer were all of the IT resources connected to a standard identity provider, but rather user access was granted ad hoc in the specific system, application, file server, or network rather than centrally. This created a variety of different places where users and IT admins needed to go to manage their access. Over time, IT vendors realized the opportunity and started to build solutions around these problems, but they were all add-ons and one-offs from centrally managing a person’s identity creating a complex web of identity management solutions and activities. This evolution of the identity management approach makes sense as the IT landscape evolved, but IT organizations don’t need to settle for this less than ideal approach with multiple solutions and ad hoc approaches
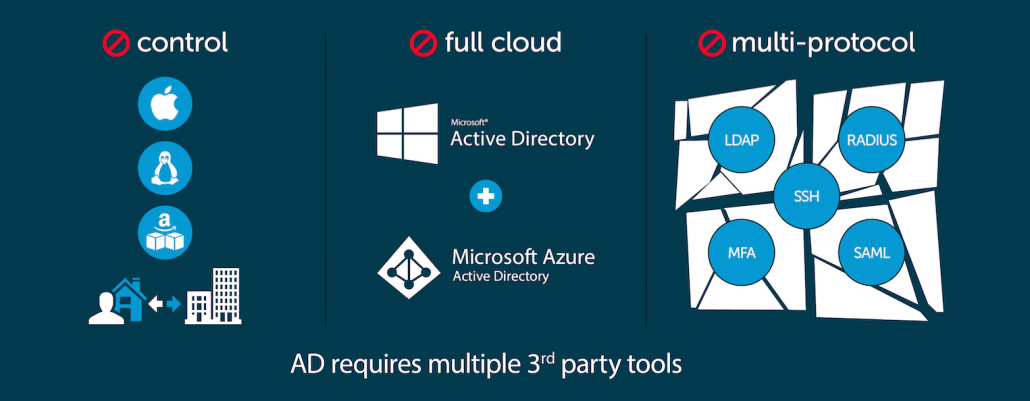
Why Focus on the Identity Provider?
The foundation for an IT organization can and should be a core identity provider (often called the directory service) that subsequently federates identities to the IT resources that their users need. Rather than creating multiple identities across the organization, IT admins can manage one authoritative identity for each individual. There is very little in IT that is more foundational than that. In doing so, IT admins gain control over user access at the core. Security can be implemented at the core. Compliance can be managed at the core. And, end users need to only leverage one identity to access their entire range of IT resources. The result is that systems, processes, and technologies can all be aligned to this one, single foundation across an organization. There isn’t an option to create one-off, shadow solutions that work for one group, yet leave the organization and IT exposed.
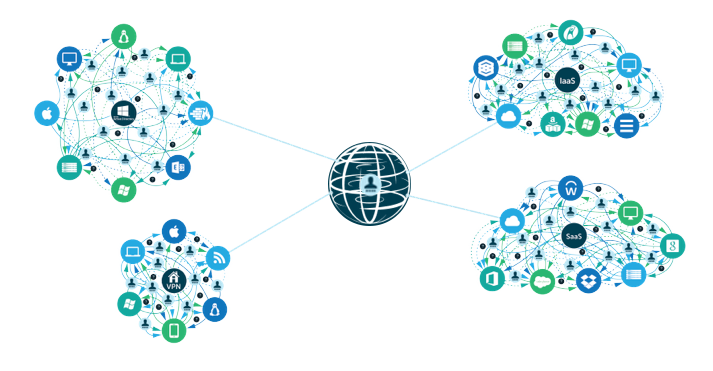
Building a Strong Identity Management Foundation
Of course, in order to build a strong identity management foundation, there needs to be laser focus from the IT organization that solving the problem at the core is the right approach. This is where building a culture to focus on what’s critical and important rather than just urgent is imperative. There are too many competing priorities that can solve the immediate pain but create many more downstream issues. With end users lobbying for easier access and executives focused on their specific projects, it can be extremely difficult for IT organizations to find the space to solve foundational issues.

By taking the time to focus on building one authoritative identity provider for the organization, the benefits can be significant, including:
Control – IT organizations have control over the user and the resources they need to access from one location within the IT infrastructure. IT admins don’t need to track down identities stored in multiple places or deal with shadow IT situations.
Security – with the risk of security breaches increasing everyday, a central identity provider gives IT organizations a leg up on the security challenges they face. Multiple identities aren’t floating around the organization with a risk of being compromised. Further, IT can enable significant step-ups in security such as multi-factor authentication, password complexity, and SSH keys.

Efficiency – with a core directory service in an organization, all IT resources effectively tie back to the central identity provider for authentication. This means that there is a highly efficient process to implement new IT solutions as well as control access. End users have one identity that they use for access, reducing friction and frustration on their part.

Scaling – as organizations scale the process of onboarding and offboarding users becomes more complex with each passing day, a central identity provider can be the foundation to build a highly scalable process that functions as the organization grows.

Solving problems at their core is the best way to make efficient use of your time now and in the future because the benefits continue to accrue as time goes on. Of course, that is often easier said than done when there are many competing priorities. IT admins face this problem in the identity management space with so many choices such as web application single sign-on, identity bridges, MFA solutions, and more. If IT organizations can step back and focus on the core of the problem – creating one identity for each individual across the entire organization – they will create a foundation for IT that can be leveraged to build a highly efficient and secure organization.
JumpCloud® and The Foundation of IT: The Identity Provider
Fortunately, a next generation identity provider platform has recently emerged that can help IT admins consolidate virtually all of their identity management infrastructure into one comprehensive cloud-based solution. Called JumpCloud® Directory-as-a-Service®, it empowers IT with increased control, security, efficiency, and scalability throughout their infrastructure.
Contact JumpCloud or schedule a demo to learn more about the foundation of IT: the identity provider. You can also sign up for a free account and see a next generation identity provider platform in action today. Your first 10 users are free forever!
