Today’s modern IT environment consists of Mac, Windows, and Linux devices, and users at many companies are spread out all over the world. This all adds a new layer of complexity to user and device management that can easily result in a substantial loss in productivity and/or present major security concerns if not dealt with properly. This diverse IT landscape requires a modern approach to user and device management.
To keep up with the current and future iterations of the modern IT environment, a device management system needs to recognize that users are at the core of everything — including devices. On top of that, the user and device management system that your organization chooses to employ needs to include five key components and capabilities:
- Zero-touch enrollment and deployment
- Full user management control
- Remote device configuration
- Remote software management and OS updates management
- Device health and telemetry monitoring
In this article, we’ll hit on why proper device health and telemetry management is essential within your IT ecosystem, what types of data you should be monitoring, and how JumpCloud specifically addresses device health concerns whether the devices are remote or on-prem with Directory and System Insights.
Why Modern IT Environments Need a Device Health and Telemetry Solution
Putting a system in place that monitors devices and their overall health is essential to maintaining a secure IT environment and a productive workforce. Telemetry data pulled from devices can be used for a variety of improvements across an organization, including (but not limited to) the user experience, security posture and practices, as well as application health and performance. Device health and monitoring in this sense is not to be confused with user activity monitoring and privacy invasion.
With how often devices are used in an organization, likely 40+ hours a week, there’s significant room for problems to arise if those devices are left unmanaged and are not closely monitored for updates, security gaps, and inconsistencies. Whether you have a device management system in place already or you’re looking to implement one from scratch, you need to consider what device health data you currently monitor and what data you want to monitor going forward — does the solution you have in mind cover all of that?
What Types of Data You Should be Monitoring Across Devices
Although the types of data collected and monitored vary across organizations based on different goals and needs, there are many types of data that we recommend all organizations monitor.
Examples of data that should be monitored across company devices:
- User authentications to relevant pieces of software and networks
- General admin activity/changes within the environment
- Events such as password changes, lockouts, and file disk encryption adjustments
- The policies/configurations assigned to each device
- Commands being run
- Applications and browser extensions installed
- Memory/storage capacity
- Software versioning for patch management
Automatically collecting this data sets your IT team up for success considering the significant amount of time they already pour into related tasks where they may have to manually hunt down data and information. Having this data readily available for viewing and filtering is integral to passing compliance audits and to making immediate changes within the environment when someone notices that something is amiss.
The point of device health and telemetry monitoring is to ensure that managed devices are in tip-top shape to prevent security breaches and losses in productivity through a proactive approach to managing devices. This type of device monitoring should not interfere with user privacy or production — conversely, it should help decrease the number of incoming support requests to the IT team and increase system uptime.
How Device Data is Monitored With JumpCloud
JumpCloud’s platform includes two primary ‘Insights’ tools that can be used to monitor, log, export, and save user, device, network, and system data — they are called Directory Insights™ and System Insights™.
Directory Insights
Directory Insights is JumpCloud’s event logging and compliance feature. Directory Insights allows admins to get a bird’s eye view of what’s happening in their IT environment, which is absolutely necessary in order to pass compliance audits. The information found in this feature can be used as evidence to prove compliance to auditors, make useful changes within the environment, and monitor suspicious activity directory-wide, no matter where users and devices are located.
Examples of activities and processes you can monitor with Directory Insights:
- User authentications to the admin/user portals, SAML SSO apps, RADIUS, and LDAP
- Activity in JumpCloud Portals, including admin changes within the directory
- Windows, macOS, and Linux events: user authentications to systems including agent-related events on lockout, password changes, and file disk encryption
- MDM command results

System Insights
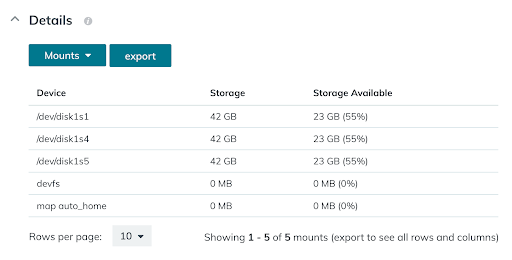
JumpCloud’s System Insights feature extends system management by providing telemetry across your fleet of devices, whether macOS, Windows, or Linux. Using System Insights, you can easily take stock of your suite of systems and get an overview of the state of the devices across your organization. You can also query system endpoints to proactively resolve issues without interrupting users.
When it comes time for an internal or external audit, these insights can be used as evidence to prove that your systems are compliant. Along with that, a very important security point to consider is that System Insights allows security and DevOps teams to interrogate machines in search of security vulnerabilities so they can fix them before they can be exploited.
System Insights provides vital information on:
- Users and groups
- Hardware and disk utilization
- Applications and browser extensions
- Encryption settings and software versioning
- And over 200 other data points
The Takeaway: Modern IT Environments Need a Modern Device Health and Telemetry Solution
Utilizing tools like Directory and System Insights is a core part of modern device management, because no matter where organization-managed devices are, IT can monitor and manage them from a single pane of glass.
These tools help you understand the reliability of your organization’s systems and gather critical information about system uptime, which can be leveraged to diagnose problems before they present far-reaching effects. These tools also let you monitor device memory and storage statistics which can be used when making system upgrade decisions. In terms of inventory management, these features help you keep track of hardware information such as vendor, model, serial number, and user assignment. Most importantly, adding these insights into your environment allows admins to track patterns and quickly see when something seems off regarding security and compliance — giving them the time and resources they need to improve security posture and set up processes to help prevent future breaches.
Modern device management includes but is not limited to managing device health and telemetry. At JumpCloud, we believe that there are five key components of modern device management that cannot be overlooked. Each component works hand-in-hand with the others to ensure that your web of devices remains secure, compliant, and efficient.





