IT organizations have made significant investments into security solutions, and firewalls (with VPNs) are among the most expensive. Unfortunately, network appliances are too frequently not unified with other infrastructure such as identity and access Management (IAM), which leaves gaps in the implementation of Zero Trust security strategies.
There’s an awareness that IT should be doing more, but cost, complexity, and management overhead are often major roadblocks.
JumpCloud removes these impediments and makes it possible to maximize your Fortinet investment by leveraging its built-in capabilities in conjunction with the JumpCloud directory platform’s layers of security. JumpCloud’s IAM security controls supercharge firewall and SSL VPN management and security through its directory, conditional access policies, and multi-factor authentication (MFA).
Those capabilities are otherwise unavailable on a Fortinet appliance or involve additional costs and vendors. This configuration also reduces the firewall’s footprint on the open web, reducing the potential attack surface area with JumpCloud’s IAM.
This article demonstrates how to easily integrate JumpCloud with your Fortinet appliance, beyond single sign-on (SSO), to significantly increase your overall network security posture.
JumpCloud Adds Zero Trust Security, Intelligent Management
JumpCloud leverages Fortinet’s integrated support for single sign-on (SAML SSO) to direct users to the JumpCloud portal for authentication. That’s where a Zero Trust authentication flow occurs before access is permitted to a VPN (for users) or firewall console (for admins).
There’s no third-party MFA solution (or FortiTokens) to manage and the user experience is consistent for anyone who’s accustomed to using JumpCloud SSO to access their apps and other resources.
Unified Zero Trust Security
Conditional access policies layer on additional security that’s not available through standard identity management integrations such as Active Directory or even with MFA alone. JumpCloud adds the option to restrict connections to managed devices and specified geographies, and enforces mandatory MFA for every login. It’s a unified system for all of your access control requirements.
Smarter User Management
Access to a VPN (or admin group) is determined by group membership inside of JumpCloud’s cloud LDAP directory. IAM is in effect from the initial user onboarding via HRIS integrations (or SCIM provisioning), onward throughout the user’s complete identity lifecycle.
For instance, attribute-based access control (ABAC) can suggest new group members or identify when a user shouldn’t have access to a particular resource if their role within your organization changes.
This capability will function using JumpCloud by itself or in addition to existing directories such as Active Directory, Azure AD, or Google Workspace. The choice is up to the IT administrator.
Integrate JumpCloud with Fortinet NSFWs, SSL VPN
Let’s begin by outlining the Fortinet portion of the integration, followed by JumpCloud’s setup. It’s helpful to have an understanding of Fortinet’s command line interface (CLI) to streamline the process. It’s possible to then use the GUI to make changes and verify your configurations.
Fortinet Setup
The initial setup establishes the SAML service provider (Fortinet) and identity provider (JumpCloud). These settings must be identical when you enter them into the JumpCloud admin console in later steps to prevent SAML SSO integrations from producing unknown errors.
# config user saml
edit "jumpcloud"
set cert "Fortinet_Factory"
set entity-id "<IP or FQDN>:8443/remote/saml/metadata/"
set single-sign-on-url "<IP or FQDN>:8443/remote/saml/login/"
set single-logout-url "<IP or FQDN>:8443/remote/saml/logout/"
set idp-entity-id "https://sso.jumpcloud.com/saml2/saml2/JumpCloudForti"
set idp-single-sign-on-url "https://sso.jumpcloud.com/saml2/JumpCloudForti"
set idp-single-logout-url "https://console.jumpcloud.com/userconsole"
set idp-cert "REMOTE_Cert_2"
set user-name "email"
next
End
The GUI will display the following, with slight variations such as whether you’ve previously imported a SSL certificate. This example lists “REMOTE_Cert_3,” but the difference is superficial. You may also opt to use a different attribute for authentication such as “username.”
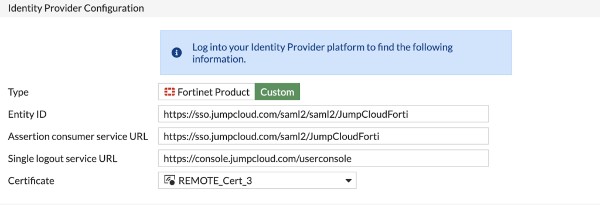
Note that it’s a best practice to replace the default unsigned SSL certificate with one that’s issued by a certificate authority (CA). There’s a built-in interface to use Let’s Encrypt as your CA.
Next, we’re going to first configure the Fortigate SSO user group, followed by the optional step of establishing an SSL VPN configuration, authentication rule, and the requisite firewall rules.
# config user group
edit "ssl-saml-group"
set member "jc-saml-vpn"
next
End
These firewall rules, derived from a Fortinet support article, are only applicable if you don’t have an existing SSL VPN that has established access control lists and IP assignments. Skip this section if it doesn’t apply.
# config vpn ssl settings
set servercert "self-sign"
set tunnel-ip-pools "SSLVPN_TUNNEL_ADDR1"
set tunnel-ipv6-pools "SSLVPN_TUNNEL_IPv6_ADDR1"
set port 8443
set source-interface "port1"
set source-address "all"
set source-address6 "all"
set default-portal "web-access"
# config authentication-rule
edit 1
set groups "ssl-saml-group"
set portal "web-access"
next
end
end
# config firewall policy
edit 1
set name "samltest”
set srcintf "ssl.root”
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
set logtraffic all
set groups "ssl-saml-ngrp"
set nat enable
next
I followed the steps above for my initial setup in preparation for this article. I find it important to tune my configuration by specifying how IPs are assigned (as well as defining a range) and to modify whether users may access the VPN using FortiClient applications.
However, you should consult your own policies and work with your Fortinet rep if you need any guidance on this.
An example of a tuned configuration is shown below.

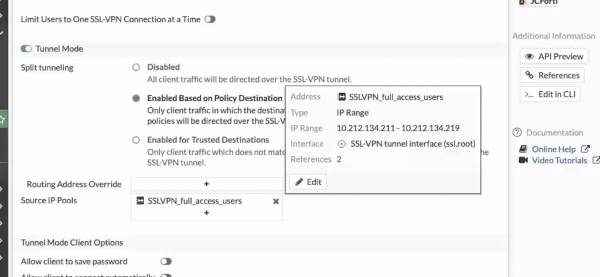
You’re now ready to move on to the JumpCloud portion of the SSO integration, but keep your Fortinet instance open to retrieve SAML field information and your local SSL certificate.
JumpCloud Setup
Your first task is to create a custom SSO connector for Fortinet, but be sure to check and see whether a pre-built connector is available to you. JumpCloud provides hundreds of free connectors as part of your subscription and regularly adds new ones for its users.
Create a SAML Connector
Navigate to the SSO button in the left panel of your administrative console and hit the “plus” sign. Then, select “Customer SAML App” (if you’ve searched for a Fortinet connector and there is not one present in the catalog). You may label your connector as well as create a color scheme and logo; this SAML how-to article goes into greater detail about the steps that are outlined below.
This is the one that we created for this article, as an example.
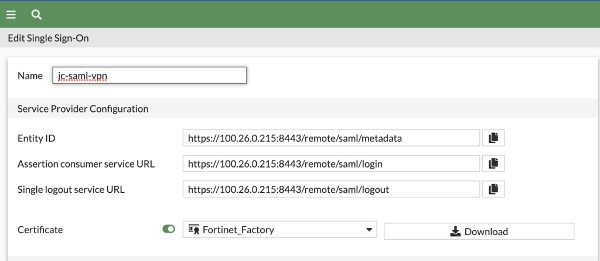
The next step is to navigate to the SSO tab. You’ll set an Entity ID that’s unique to your organization’s environment. It’s important to note that this and all the other settings on this screen are case-sensitive on both systems; any typo will result in errors and the integration will fail. Note: It’s a best practice to export/import metadata, but that’s not an option on the Fortigate GUI.
- Fill in the fields from the service provider (Fortinet appliance). They’ll resemble, but will not be identical to these settings:
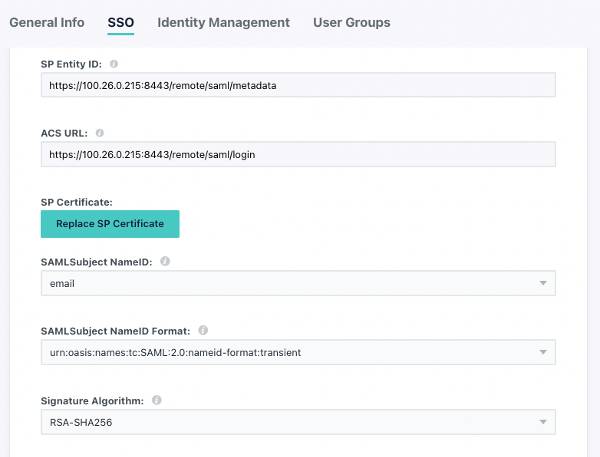
Be certain that the entries are identical to your appliance’s settings.
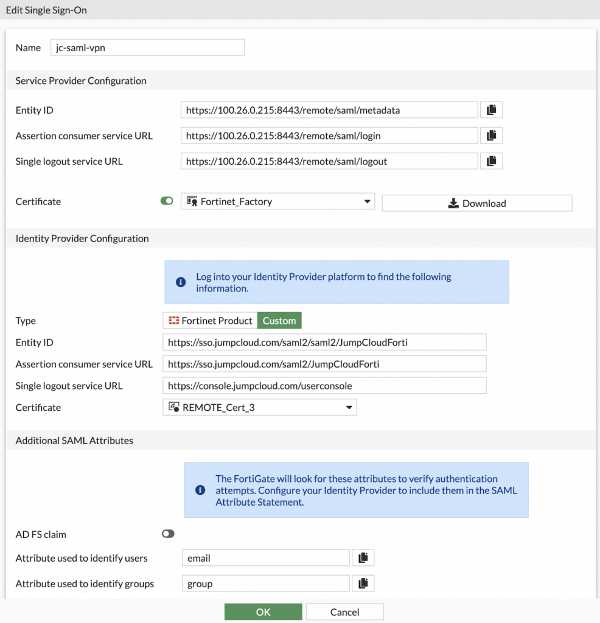
This is the view from Fortinet.
- Upload the local Fortinet certificate. Complete instructions for this step can be found in this Fortinet support article.
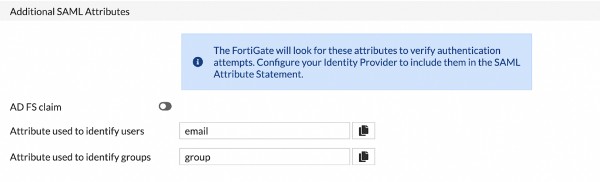
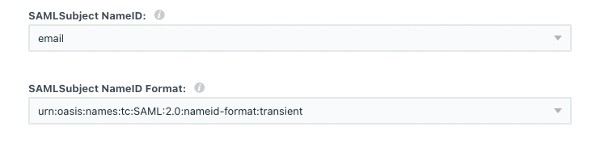
Set SAML Subject NameID as “email” and select the format in the image below.
- Enter the Default RelayState and Login URL as shown below, but using your FQDN.
- This login URL redirects logins to the JumpCloud User Portal for VPN web portal and tunnel sessions.
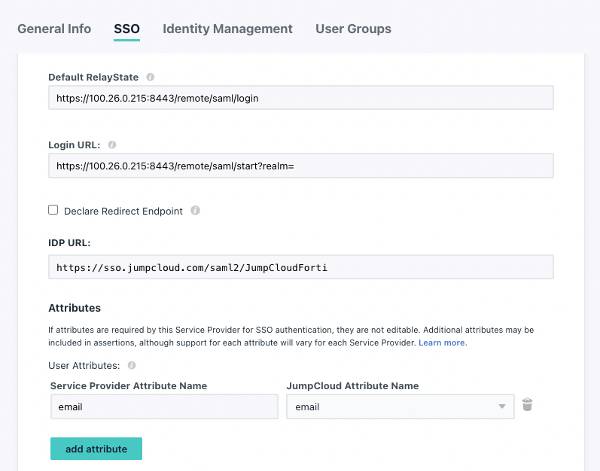
- Set the user attribute to “email,” or whichever you prefer to use and map it to “email.”
You will then activate the configuration, which may be modified later. Then, you’ll download the JumpCloud SSL certificate to upload into Fortinet. Make certain the name matches the CLI configuration.
Assign Permissions within Groups
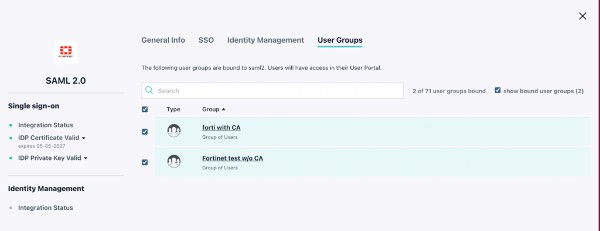
Navigate to the User Groups tab and add a group(s) that should have access to the VPN. The link below is a detailed guide for admins who are uninitiated with JumpCloud.
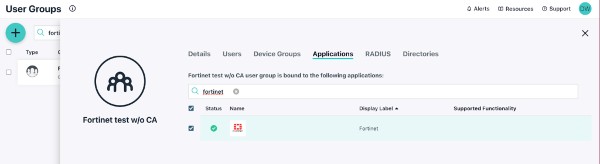
You may also assign the “Fortinet” application to a user group from that interface.
You should now be ready to test your SAML SSO integration.
Test Your Initial SSO Integration
Log in as a user that’s bound to the group(s) that you associated with the SAML connector. You’ll be prompted for your JumpCloud credentials and logged into the SSL VPN web portal if it’s successful.
You may also test using the Fortinet login page; it will redirect to JumpCloud. This is an important step toward better security, because an attacker that uncovers your firewall’s IP would be redirected to JumpCloud should they decide to attempt to breach it.
You’re also freed from establishing vpn.domain.com and can use a GUID or random subdomain.

The VPN Portal will appear as an application within the user console.
Type this command in the Fortinet CLI to verify connectivity:
# get vpn ssl monitor
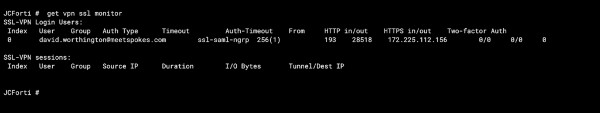
A user has successfully signed into the SSL VPN.
FortiClient (optional), will redirect to the JumpCloud login for VPN tunnel access. Verify that the firewall allows traffic via port 8443; using that port helps to monitor traffic and won’t clash with admin logins to the appliance of the standard port, 443.
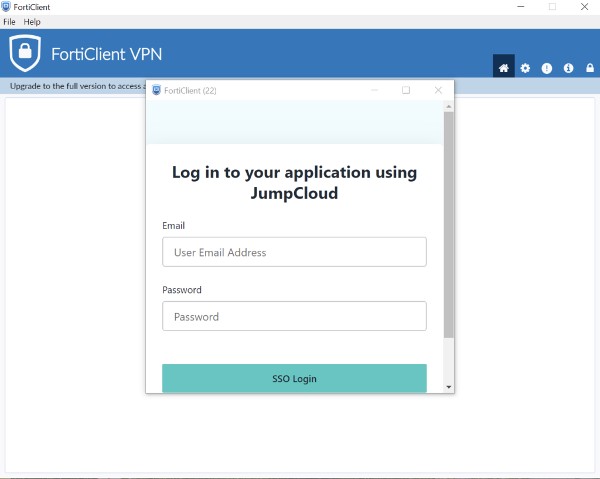
FortiClient loads a session to log into JumpCloud.
Add JumpCloud’s Zero Trust Security
Additional Zero Trust security is available through JumpCloud Conditional Access.
Policies are assigned to existing groups or you may create dedicated groups for special requirements. Different groups may have different policies (or no policies). Policies include:
- Geofencing: You may whitelist specific countries to access your VPN. Access from countries that aren’t whitelisted will be disallowed.
- Require JumpCloud managed devices: IAM is an important security control, but allowing unmanaged devices within the “gates” is akin to the Trojan horse breaching the walls. JumpCloud manages devices across every major OS.
- Mandatory MFA: MFA will challenge users to prove who they say they are using a TOTP code or Push MFA through the JumpCloud Protect™ application. You can determine which type in user setup (we recommend push for better ease of use).
Retest your connectivity to ensure that everything works as it should.
You’re now finished integrating JumpCloud with your Fortinet appliance. Your SSL VPN is now remarkably more secure than if you weren’t running with MFA or conditional access policies. Organizations that use Azure AD may utilize delegated authentication where the same Microsoft credentials that they use everywhere else will work with JumpCloud SSO (and more).
Try JumpCloud SSO with Conditional Access
Firewalls and VPNs are crucial components of perimeter-based security and should be protected. JumpCloud makes it easy to test and extend Azure or Okta with MFA and conditional access for Zero Trust security. Sign up for a trial of JumpCloud today to get started.





