Regardless of industry or organization size, company leaders must guard their data fiercely from bad actors and improve their cybersecurity practices.
A shifting IT landscape makes for new and different challenges to which IT admins must respond. For example, the frequency of ransomware and DDoS attacks decreased in 2018, but losses caused by business email compromises doubled and cryptojacking incidents more than tripled, according to the Online Trust Alliance.
Protect your data against these varied attacks with a layered approach. This checklist provides the first steps in doing your due diligence to secure your company and ward off bad actors. Security isn’t one-size-fits-all, and you’ll want to tailor your solutions to your organization, but these are the high-impact basics to get you started.
1. Identify Resources to Guide Cybersecurity Work
To begin with, identify frameworks to guide your cybersecurity work and strengthen your company’s security posture. Combine these frameworks for even more guidance as you complete your work.
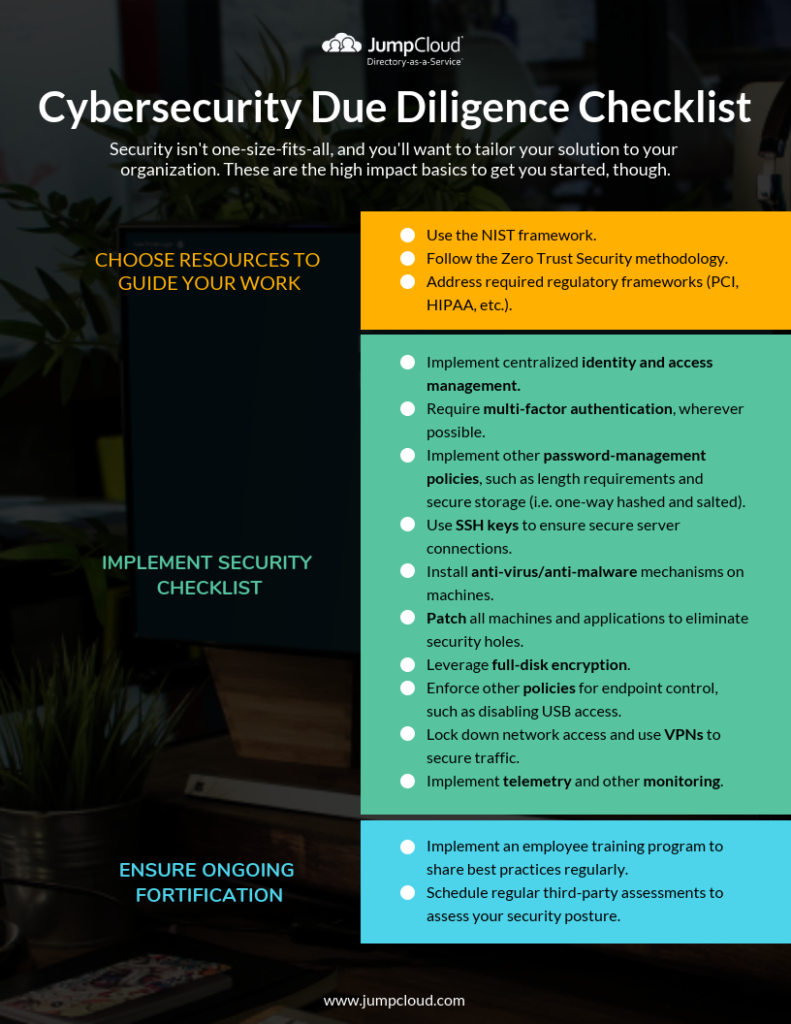
NIST Framework
The National Institute of Standards and Technology (NIST) produced a framework for improving critical infrastructure cybersecurity, which officials said should serve as “every company’s first line of defense.”
This framework outlines five functions:
Identify — Develop an organizational understanding to manage cybersecurity risk to systems, people, assets, data, and capabilities.
Protect — Develop and implement appropriate safeguards to ensure delivery of critical services.
Detect — Develop and implement appropriate activities to identify the occurrence of a cybersecurity event.
Respond — Develop and implement appropriate activities to take action regarding a detected cybersecurity incident.
Recover — Develop and implement appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident.
These functions “aid an organization in expressing its management of cybersecurity risk by organizing information, enabling risk management decisions, addressing threats, and improving by learning from previous activities.”
To learn more about this framework and how it can be implemented, check out NIST’s “Framework for Improving Critical Infrastructure Cybersecurity” publication, which provides an in-depth look at its guidelines.
After familiarizing yourself with this framework, you can pair it with the zero trust security (ZTS) methodology to inform your security work further.
Zero Trust Security Methodology
Following the ZTS methodology, IT admins want to take four key steps:
- Verify employees are who they say they are.
- Verify employees use clean systems to which they have access.
- Verify those employees and systems have rights to the applications they access.
- Verify employees are working on secure networks.
This methodology is a layered approach to security that provides more defense than its predecessor, which was perimeter-based and allowed bad actors to traverse networks if they breached the perimeter. This resource provides more information about understanding and implementing the zero trust security methodology.
Depending on your organization’s industry, you will also need to adhere to compliance regulations, which you can do in conjunction with the preceding guides.
Required Regulatory Frameworks
Whether it’s the Payment Card Industry Data Security Standard (PCI DSS) audit, the HIPAA Security Rule, or another compliance regulation (e.g. GDPR), you will need to ensure your cybersecurity practices are in alignment if they apply to your company.
2. Implement Centralized Identity and Access Management
Using those frameworks to guide organizational decision-making and big-picture thinking, you should then consider the following security measures as you fill out the frameworks.
First and foremost, prioritize centralized identity and access management. IAM is about ensuring the right users have the right access through a set of defined policies and procedures. It’s become a more complex undertaking because IT admins need to ensure employees connect to all the resources they use, including systems, applications, files, and networks, whether those resources are on-prem or in the cloud.
A central identity provider is critical here. If employees have dispersed sets of identities to access various company resources, the security threat increases because of problems like password reuse and identity sprawl. Instead, it is far more secure — and more convenient for them — if they each use one hardened identity to access every resource.
Additionally, for IT admins, the ability to manage user identities from a single interface improves security. For example, once an employee leaves the company you can easily remove them from all their resources instantly rather than manually removing them from each one.
3. Determine Additional Cybersecurity Measures
After implementing central identity and access management, additional fundamental measures improve your company’s security posture, including:
- Require multi-factor authentication wherever possible, including systems, applications, and networks.
- Implement additional password-management policies, such as length requirements and secure storage (i.e. one-way hashed and salted).
- Use SSH keys to ensure secure server connections.
- Install anti-virus/anti-malware mechanisms on machines.
- Patch all machines and applications to eliminate security holes.
- Leverage full-disk encryption.
- Enforce cross-platform policies for endpoint control, such as disabling USB access.
- Lock down network access and use VPNs to secure traffic.
- Implement telemetry and other monitoring.
4. Ensure Ongoing Fortification
Beyond the frameworks and security measures detailed above, you should implement a stringent employee training routine and use third-party assessments to continually enhance cybersecurity at your company.
It’s important to recognize that no tool or product completely eliminates an organization’s most vulnerable threat vector: the employee. Whether it’s a compliance requirement or not, an employee training program to share best practices regularly is an imperative. These trainings can touch on topics such as adhering to password complexity best practices, recognizing and averting phishing attempts, and avoiding using public WiFi networks.
You can also schedule regular third-party assessments to evaluate your security posture and identify weaknesses.
External penetration testing and other audits expose vulnerabilities you can address with additional policies and practices.
Learn More
If you’re interested in learning more, contact us and our security experts will help your company lock down its data and operations.
You can also consult the following checklist to put this guide into practice. Again, this is not comprehensive, but it is a good place to start
If you’d like to download this one-page resource, click the link below.