Network security is of the utmost importance as the number of reported data breaches continues to rise. Implementing the proper measures can be harder for certain organizations than others, especially those experiencing firsthand the rise of macOS usage in the modern enterprise. As such, these sysadmins and network engineers are looking for ways to optimize RADIUS authentication for Macs in order to securely connect to WiFi and VPN.
We will discuss what RADIUS is and how it is used for authentication, as well as how RADIUS is used to authenticate Mac network access.
What is RADIUS?
Before we dive into Mac specifics, let’s look at the RADIUS protocol overall. RADIUS stands for the Remote Access Dial In User Service. A RADIUS server works on behalf of a client to authenticate user network access via their credentials stored in an identity provider (IdP). The IdP then takes the credentials shared through RADIUS to ensure that a user accessing the network is who they say they are and can be trusted.
Specifically with wireless networks, one of the more popular ways that RADIUS is used is to require users to input their unique set of credentials instead of a shared WPA key, making said authentication tighter than standard WiFi security. This process makes it easy to combine multi-factor authentication (MFA) and RADIUS for VPN security as well.
RADIUS Authentication Process
Let’s take a look at the nuts and bolts of RADIUS authentication generally so that we can understand it and apply it for Macs. The following graphic details the process for RADIUS authentication on port 802.1x:
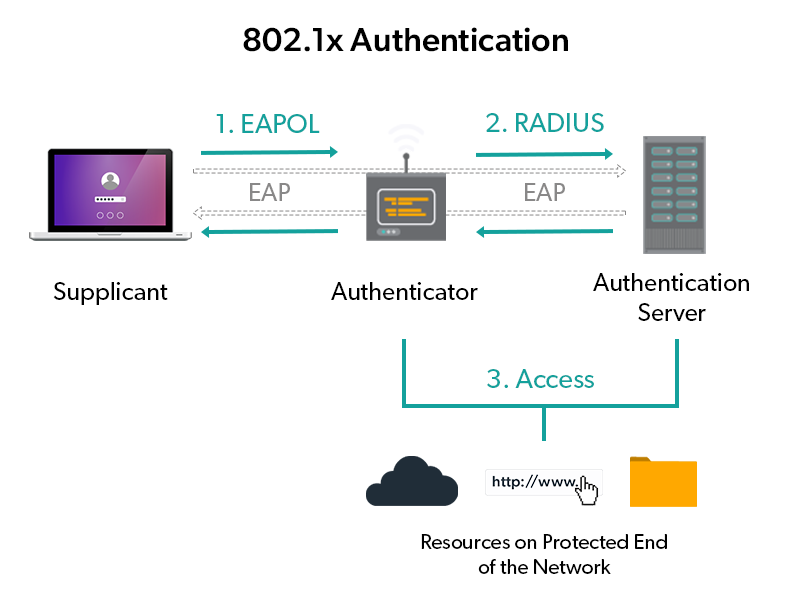
A key aspect to focus on in this scenario, however, is the supplicant and its relationship to the identity provider (not shown in the diagram above). The supplicant is the user/system requesting access to the network via the RADIUS server, and, subsequently, the identity provider.
The supplicant in this case would be on the macOS system. Although early Macs required additional supplicant software, most modern Mac systems have native supplicant software baked in that uses the PEAP protocol (which uses a similar process to EAP, detailed above).
Regardless, the major issue with RADIUS authentication that admins face is the implementation itself. With that in mind, let’s examine how RADIUS authentication for Macs works in a handful of hypothetical scenarios.
RADIUS Authentication by Organization Type
Mac-Centric Organizations
For organizations that solely use macOS systems, the average IdP of choice for many years has been Open Directory — a sub-component of macOS Server. Admins can integrate their choice of RADIUS server, such as FreeRADIUS, with Open Directory and, after some legwork, integrate RADIUS authentication into their environment.
The drawback here is that it appears Apple is no longer focusing on keeping up Open Directory, choosing instead to hone in on the consumer market they have come to dominate. Many are speculating that in the near future, Open Directory will not receive regular updates, which can lead to severe security vulnerabilities and an inability to support new macOS versions as well.
Mixed-OS Organizations
Organizations that feature a heterogenous blend of systems, including Macs, Windows, and Linux, face more challenges in RADIUS authentication. Many of these organizations rely on on-prem Microsoft Active Directory (AD) as their core IdP.
Integrating AD with a RADIUS server like FreeRADIUS or Microsoft’s own Windows NPS has the same integration challenges as the previous example. Using AD paired with FreeRADIUS or Windows NPS alone for Macs, however, is far more difficult using native configurations because unlike Open Directory, AD wasn’t designed for Macs. In order to do so, an organization will likely need to employ an identity bridge to connect their Macs to an AD instance — which will need to be configured to work with RADIUS as well.
Adding additional solutions into the RADIUS authentication process creates more line items on an IT department’s budget, not to mention the uptick in work required to set it all up and manage it. Beyond that, creating additional steps in the process also invites potential attack vectors into an organization’s network, subverting the reason for implementing RADIUS altogether.
RADIUS Authentication for Macs and More From One Cloud Solution
What IT organizations need is a way to centralize their IdP, identity bridge, and RADIUS server in a single solution. This is where JumpCloud’s open directory platform comes into play.
JumpCloud is a modern cloud directory service, and has reimagined Active Directory for the modern era. IT organizations today leverage JumpCloud to manage their users and their access to virtually all the assets and resources they use daily. That means identity management for systems, networks, applications, infrastructure, and more — regardless of platform or location (cloud or on-prem).
For RADIUS authentication for Macs, organizations can use JumpCloud’s Cloud RADIUS feature, a completely cloud-hosted RADIUS server setup, to provision and secure access to wireless networks, all from a cloud console. Cloud RADIUS provides all the benefits of RADIUS authentication without any of the hassle of implementation.
Sysadmins can use JumpCloud in various ways to address the scenarios laid out in the section above.
Create a Directory in the Cloud
For organizations looking to get off their macOS Servers, or for those growing tired of their AD instance, JumpCloud is the complete cloud directory service. Organizations can migrate their existing directories, including those housed in Google Workspace or Microsoft 365, directly into JumpCloud. From there, they can manage their users, systems, networks, etc. as they would normally, except from a single solution based in the cloud.
Extend AD to RADIUS and Macs
AD-centric organizations can use JumpCloud’s AD Integration feature to propagate their existing AD credentials to non-domain resources, such as Mac systems and JumpCloud’s hosted RADIUS service. AD Integration leverages a pair of agents downloaded on an AD domain controller to create a bi-directional sync between the AD domain and JumpCloud-managed resources. Organizations with AD Integration can keep their AD instance in the driver’s seat while letting JumpCloud manage the tricky bits, such as RADIUS authentication for Macs.
Try JumpCloud Cloud RADIUS
If you’re ready to test out JumpCloud’s RADIUS capabilities on your Mac, sign up today for a trial of JumpCloud. If you’d like additional information, feel free to consult JumpCloud’s Knowledge Base, or drop us a line.





