JumpCloud’s AD Integration (ADI) provides IT admins an all-in-one solution to complement their sprawling AD-based IT environments. Instead of leveraging SSO solutions, identity bridges, MFA tools, and on-prem RADIUS and / or LDAP servers, IT admins roll all of these disparate tools into one cloud-based solution. And with AD Sync – a key feature of AD Integration, IT admins gain the ability to simplify password management activities – especially for macOS users – by offloading password change actions to a self-serve process on their system.
It’s a win for everyone involved.
AD Import
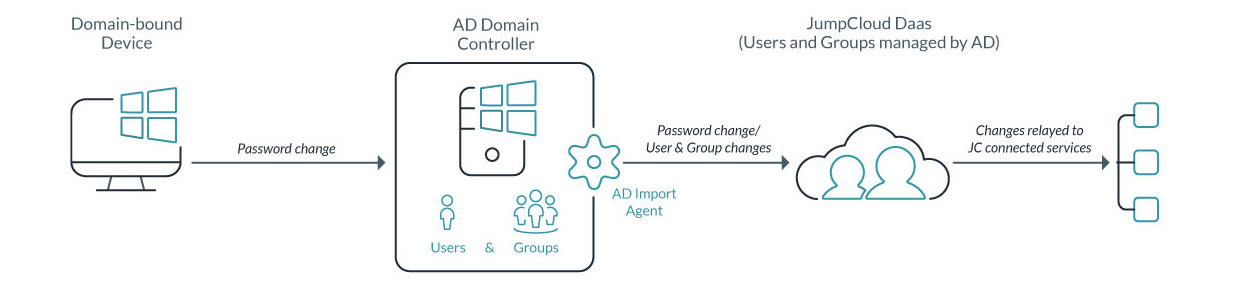
JumpCloud’s AD Import, the first facet of AD Integration, extends Microsoft® Active Directory® managed identities to resources not directly supported by AD. Simply sync users and groups from AD with JumpCloud® Directory-as-a-Service® and extend their access to networks, applications and systems—all while your users continue to access virtually all of their resources via their AD credentials. Simple for your end users and complete control for you.
AD Sync
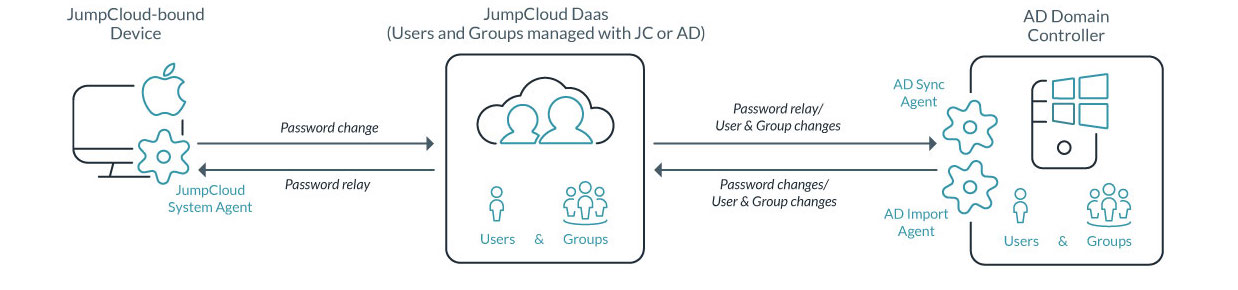
AD Sync, the second critical piece of the ADI JumpCloud feature, enables users to change their password either in a web-based portal (all major OSes) or on the system itself (Windows® and macOS®) to help alleviate the burden of support tickets aimed at password resets. Passwords are automatically synced back to Active Directory, maintaining it as the core, authoritative identity provider for an organization.
Features of AD Integration
- Authentication services for remote/unbound Mac, Linux, and Windows systems through JumpCloud’s LDAP, RADIUS, and SAML services using AD identities.
- User and group synchronization for all selected objects. AD to JumpCloud password and data synchronization in seconds.
- JumpCloud to AD data and password synchronization via AD Sync. Ideal for macOS and Linux users.
- Synchronization of AD Users to G Suite™ and Azure® AD / Office 365™ with no middleware like Google Cloud Directory Sync (GCDS) or Azure AD Connect.
- Multi-factor authentication (MFA) services for JumpCloud synchronized user accounts and Mac and Linux systems.
- Support for every Windows Server version starting with 2008. Windows 7 through 10 support as well. Management of non-AD bound Windows devices.
Benefits of AD Integration
- Maximize your investment in Active Directory.
- Enable IT to leverage the best IT resources regardless of platform, provider, or location.
- Centralize control over virtually your entire IT environment.
- Control access to remote and unbound Mac, Windows, and Linux systems with AD credentials.
- Simplify access management of remote employees without a VPN.
- Eliminate the need for multiple AD instances scattered throughout an organization.
- Improve security by reducing identity silos and implementing MFA.
- Extend an AD-based identity for systems, cloud and legacy applications, VPNs, wireless networks via RADIUS, servers in AWS®, files on-prem and in the cloud, and more.
- Promote proactive password changes and empower employees to stay on top of password management while fielding less password-focused support tickets with AD Sync.
Demo Active Directory Integration Today
If you’re interested in maximizing the ROI of your Active Directory implementation, schedule a personalized demo today to see how it works.