When setting up a Git repo, controlling access is key. With JumpCloud’s LDAP solution, it’s easy to manage your users’ access to your repositories. Let’s walk through how this can be done.
Create your Git server
We’re assuming here that you have a clean Linux server machine. I’m using Ubuntu 14.04. Other systems might have slight variations with the commands, especially in the installation steps.
Install Git
Installing the Git server software is simple.
sudo apt-get install git
Add user identities to the Git server
Git controls access to repositories through the fundamental user access to files and directories on the machine. By managing these users via LDAP, you manage who can access which repositories.
Let’s configure LDAP in JumpCloud to get this going.
Get your organization’s setting from the JumpCloud admin console
Find your organization’s information in the settings in the JumpCloud console. Make sure LDAP is toggled to ‘on’. We’ll be using the value found here for the Organization ID.
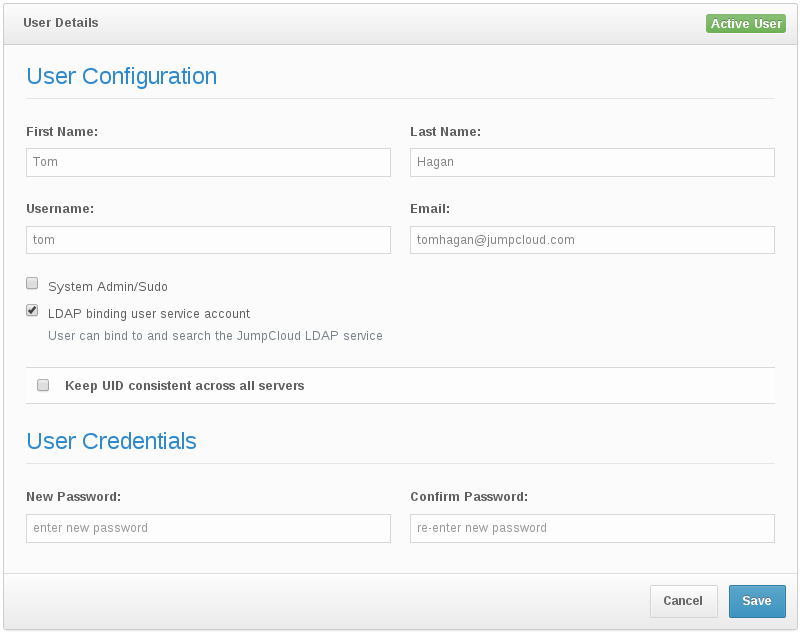
Set your user as an LDAP admin
In this case we’re going to use an individual user account as the LDAP admin. Make sure the “LDAP binding user service account” is checked in that user’s details. We’ll need this user’s email address and password below.
Configure UIDs in JumpCloud
Note that to have the users in JumpCloud available to your machine, you need to assign values for the uids.
Under “Settings”, make sure you have checked “Keep UID consistent across all servers”, and for each individual user, also check this value and assign them a UID.
On your Git server – install the SSSD libraries
On your Linux box, install the libraries. For Debian-like systems1 use the following.
sudo apt-get install sssd libpam-sss libnss-sss
Configure SSSD
Now that sssd is installed, we will edit the file its configuration to direct it to use JumpCloud’s LDAP. Note that you’ll substitute your values found in the JumpCloud console above for <org-id>, <user-email>, and <password> to associate with your account.
The file we create is /etc/sssd/sssd.conf.
[sssd] config_file_version = 2 services = nss,pam,ssh domains = jumpcloud
[nss]
[pam]
[domain/jumpcloud]
debug_level = 2 id_provider = ldap enumerate=true auth_provider=ldap cache_credentials=true ldap_uri = ldaps://ldap.jumpcloud.com:10636 ldap_search_base = ou=Users,o=,dc=jumpcloud,dc=com ldap_default_bind_dn = uid=,ou=Admins,o=,dc=jumpcloud,dc=com ldap_default_authtok = ldap_group_search_base = ou=Groups,o=,dc=jumpcloud,dc=com ldap_user_ssh_public_key = sshKey ldap_tls_cacert = /etc/ssl/certs/ca-certificates.crt sudo_provider = none
Once you’ve made this change, set the file’s permissions using
sudo chmod 600 /etc/sssd/sssd.conf
and then restart sssd using
sudo service sssd restart
.
Key-based authentication
At this point our users can log in using their passwords (if allowed by the ssh config). Since we’re wanting to use key-based authentication, we’ll also need to make a change to the/etc/ssh/sshd_config file. Add the following lines
AuthorizedKeysCommand /usr/bin/sss_ssh_authorizedkeys AuthorizedKeysCommandUser root
and then restart the service using
sudo service ssh restart
Create your repository
Now your users have the ability to create and manage repositories on the server.
User connie creates an empty git repo
ssh connie@git-server git init –shared –bare /DevRepos/connies-repo.git
Share the repository
One key point here is that we want to share access among people within the same group.
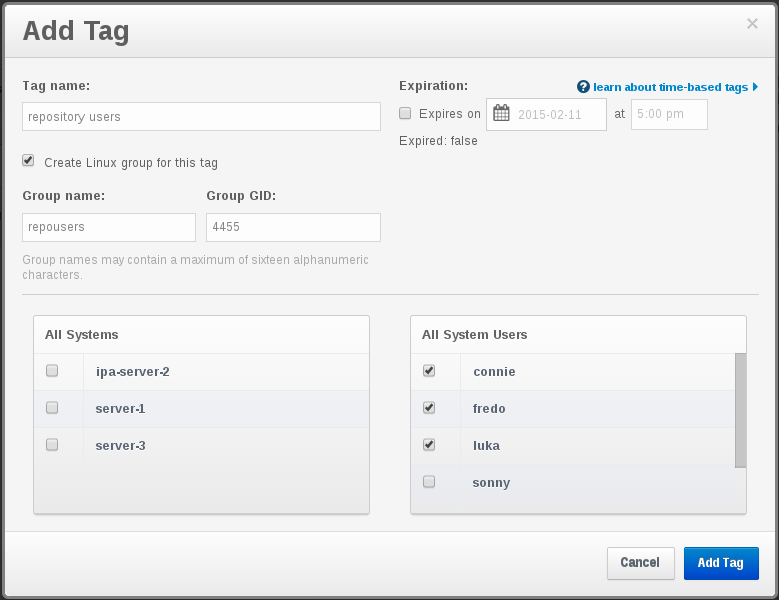
First, in JumpCloud create the appropriate group with the right users.
User connie needs to tweak ownership of the repo in order to share access with the group.
ssh connie@git-server chown -R connie:repousers /DevRepos/connies-repo.git/
That gives anyone in that same group access. Let’s make sure ONLY that group has access.
ssh connie@git-server chmod 770 /DevRepos/connies-repo.git/
Now user luka can clone
git clone luka@git-server:/DevRepos/connies-repo.git
and push changes to it
git push origin master
with no problem, but users outside of the repousers group cannot.
Easy!
- I’ve tested this against Ubuntu 14.04 – other flavors may vary somewhat ↩