It’s Cybersecurity Awareness Month! In honor of the theme — Do Your Part. #BeCyberSmart — we’re doing our part by educating organizations and IT teams on protecting themselves. Throughout October, the JumpCloud blog will focus on top cybersecurity issues, from IT admin best practices to CISO responsibilities. Tune back into the blog this month for new cybersecurity content or check out our archive of existing security articles for cybersecurity insights written specifically for the IT professional.
Imagine your boss calling your team saying their computer is locked and there’s a note on the screen demanding ransom to the tune of $5 million. Did your stomach just drop? Ours did.
Security incidents are an IT professional’s worst nightmare — and for good reason. They’re common, sophisticated, and can wreak havoc on a business.
As a security company, we wanted to understand which security incidents IT professionals fear most so we can advise them on building defenses that help them sleep at night. So we surveyed over 1,000 people who work in IT to hear their scariest IT security stories and learn how they’re equipping their stack and team, what concerns them most, how remote work affects their security approach, and more.
In this blog, we’ll cover the top three IT security scenarios respondents overwhelmingly ranked as the scariest. We’ll dive into why they’re so scary, what you can do to defend against them (spoiler alert: avoid dark basements and cornfields), and how businesses are pivoting in reaction to them.

Top 3 Scariest Scenarios (and Why They’re So Scary)
Survey Background
First, to give you a better picture of who we talked to and how they answered, we’ll briefly cover our survey methods.
JumpCloud conducted this survey in October 2021 via Propeller Insights with 509 US and 503 UK respondents. In terms of office setup, 40.6% of respondents work in the office full time, 32.5% work fully remote and 30% work in a hybrid-remote environment.
Among many other questions about their experience as an IT professional, we presented respondents with 9 different IT scenarios and asked them to rate them on a scale of most scary to least scary. The overall scores went from a not-so-frightening score — around 3,000 — all the way to a truly terrifying 6,500. Respondents’ top IT fears were overwhelmingly listed as security breaches, hacker attacks, and ransomware attacks.
The rundown of all presented scenarios and their scores is as follows:
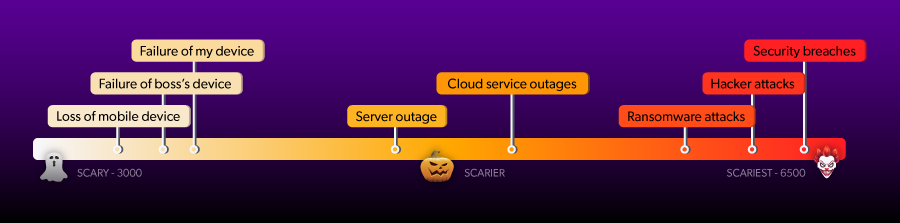
- Security breaches: 6,381
- Hacker attacks: 6,336
- Ransomware attacks: 6,240
- Cloud service outage: 5,071
- ISP or CDN outage: 4,728
- A down server: 4,641
- Your device going down: 3,622
- The boss’s device going down: 3,571
- A lost mobile device: 3,448
In addition, when asked whether they felt overwhelmed at work, only 13.4% respondents said no, and 32.1% answered neutrally. That left 54.5% of respondents reporting that they felt somewhat or very overwhelmed at work. This sets the scene of high-pressured environments where IT professionals are working diligently to fend off dangerous — and, often, likely — threats lurking around the corner.
Because the top three threat scenarios far outranked the rest as the scariest, let’s dive into those three scenarios, including what makes them so serious and how to defend against them.
1. Security Breaches
Security breaches topped the list of scariest scenarios for respondents — and for good reason. As of September 30, 2021, this year’s data breaches had already surpassed the total number of breaches in 2020 by 17%.
Why So Serious?
Security breaches can encompass foul play as well as human error, which makes them doubly scary and particularly difficult to protect against. Effectively defending against security breaches requires a holistic approach that addresses employee security best practices, implements the right security solutions, adequately equips IT teams, and constantly looks for and addresses vulnerabilities.
Notably, while malicious attacks account for many security breaches, the vast majority — 88% of them — are caused by human error. And the consequences can be severe: one respondent reported that this year, they lost £500,000 in a hack that was executed when an employee clicked on a malicious link. And this is actually a bit lower than the average cost of a data breach, which hit $4.24 million this year.
With so much on the line, the importance of employee preparedness can’t be overstated.
Building Your Defense: Don’t Go in the Basement

Most of us have seen enough scary movies to know (and the less horror-savvy have heard through the grapevine) that when there’s something fishy going on, don’t go in the basement. And yet, characters continue to go into dark basements, creaky attics, and decidedly haunted cornfields. Why?
What seems obvious to the expert often isn’t to a lay person in the thick of things. IT professionals could probably recite the signs of phishing emails until they’re blue in the face, and yet, phishing remained a recurring theme in our respondents’ scariest IT encounters.
Non-IT employees don’t spend their days thinking about cybersecurity; they spend their days thinking about their role (and their life outside of it). Thus, IT teams need to focus heavily on enabling employees and communicating with them frequently, both to relay best practices and address issues as they arise.
Fortunately, many companies have reportedly been doing their due diligence in this regard: the JumpCloud survey found that 81.8% of respondents’ companies regularly communicate best security practices with employees.
We’ll address defending against the more malicious security breaches next.
2. Hacker Attacks
Hacker attacks were ranked the second scariest IT scenario. These attacks fall under a more specific and sinister type of security breach. While hacker attacks can prey off of human error, they can also occur even when you and your team do everything right. Hacker attacks can’t, however, occur without the cybercrime component. So, what makes cybercrime so serious?
Why So Serious?
Just as you and your colleagues likely work to stay on top of IT trends, learn and adopt new technologies, develop new methods for accomplishing goals, and hone your skills on the job, so too do cybercriminals. In fact, cybercrime organizations often operate just like legitimate businesses, which means their employees (a.k.a. malicious hackers) are studying, learning, and growing their skills too.
What’s more, the coronavirus pandemic drove many companies to shift to remote work quickly. Cybercriminals have been studying these newly remote environments and learned to spot and exploit common vulnerabilities. For our respondents, where 32.5% worked fully remote and 30% worked in a hybrid remote environment, this poses some serious risks.
Building Your Defense: Outsmart the Attacker

Securing your environment against hacking takes more than your traditional antivirus software and firewall (73% of hackers say they’re irrelevant). Because hacking is now so strategic and skillful, the only way to protect against it is to be one step ahead of the attackers. And that takes holistic, strategic, and up-to-date security.
Implementing security that can outsmart hackers takes significant investments in time, effort, and money, and spans everything from network security solutions to identity and device management. And while the nature of holistic, strategic security means there’s no one-size-fits-all template, there is an approach that you can — and should — implement and use as a guide: Zero Trust.
Building Your Defense: Trust No One

Zero Trust security is a security approach that was developed in response to perimeter security’s decreasing efficacy in an increasingly cloud-based, SaaS-powered business world. Just as traditional antivirus software and firewalls can no longer be trusted, username/password-based logins shouldn’t be the only barrier to network and resource access.
Zero Trust security operates by the mantra, trust nothing; verify everything, and prescribes that no one should be authenticated or authorized without being verified securely. This goes for more than a user’s initial login; users must verify themselves separately to access any corporate resource. In addition, Zero Trust security defines secure verification as more than just a password. Rather, it prescribes multi-factor authentication (MFA) everywhere.
These tactics make it highly difficult for a hacker to gain access, and even more difficult for them to move laterally on the off chance that they do successfully gain access to a resource, protecting resources and preventing an attack’s spread.
Read more about securing your remote or hybrid environment with Zero Trust in our blog, Zero Trust Security for Digital Workspaces.
3. Ransomware Attacks
Not far behind hacking attacks or security breaches, ransomware ranked third most terrifying in terms of IT scenarios. Ransomware is a specific type of hacker attack that blocks access to critical assets and holds them for ransom, claiming they will return them in exchange for a sum of money.
Everything about ransomware is sinister and scary, but a few factors make them particularly serious threats.
Why So Serious?
First off, ransomware demands are usually high — in the first half of 2021, the average ransomware demand was $5.3 million. And that’s up 518% from last year, which averaged $847,000.
While these big sums look like they’re fit for big enterprises, that’s not always the case, and small businesses aren’t off the hook. Ransomware attackers go after everything from entire cities (like Baltimore) to small businesses, which make up more than half of ransomware victims. Over 70 of the survey respondents mentioned ransomware attacks or attempts when asked about their scariest IT experience in 2021 — one of which had ransomware come up on the company president’s computer. Another reported a ransomware attack on their supply chain, causing national food and water shortages.
But wait, we’re not done scaring you yet.
Like hacking operations, ransomware operations function like businesses — except ransomware attackers reap significant rewards every time someone pays their ransom. That funds their next venture — including sourcing high volumes and caliber of labor, deep espionage, and round-the-clock development so they can work swiftly, deftly, and accurately.
Without black market ransom funds powering your security teams, how can you compete?
Building Your Defense: Let’s Play a Game

The defenses outlined above can help businesses defend against ransomware. However, focusing on preventative measures without also planning response and mitigation measures in case of an incident is irresponsible. To fully defend your organization against ransomware, you’ll also need to play out what would happen if your organization were hit with an attack. You can do this with table-top exercises (TTX).
TTX is all too often overlooked, and it can be hard to gain traction for implementing TTX in an organization. However, table-top exercises are vital to preparing for attacks like ransomware where you need to be able to react quickly and correctly.
Table-top exercises are not unlike role-playing games: a facilitator lays out a scenario (i.e., your organization is hit with ransomware), and participants are given free rein to react how they would in a real situation. These exercises help answer many questions and iron out kinks you may not have thought of, like:
- Should you pay the ransom? (Experts usually advise against it).
- If the ransom note appears on a non-IT person’s computer, would they know to report it, and to whom?
- If the ransomware limits device or application usage for remote workers, how will they communicate with one another?
In addition to solidifying response and mitigation plans, table-top exercises give employees (not just the IT department) exposure to incident response proceedings to familiarize them with what a scenario might look like, how it might unfold, and their role as well as others’ roles to streamline communications during the process.
Because TTX can be hard to implement in your organization and the first time can be intimidating, we’ve written a blog to help you plan your first table-top exercise, including overcoming common obstacles, planning the scenario, and facilitating the exercise.
Why Weren’t the Rest Very Scary?
The rest of the scenarios presented were ranked far less scary than the top three above (a cloud service outage, an ISP or CDN outage, a down server, the respondent’s device going down, the boss’s device going down, and a lost mobile device). Why is that?
Much like an old slasher flick you’ve seen one too many times, these scenarios reflect problems that have become so commonplace that we know what to expect and how to handle them. Cloud-based infrastructure, SaaS services and remote work best practices arm businesses with workarounds, safeguards, and solutions to many of these issues.
For one, many businesses have begun moving their infrastructure to the cloud, which takes their reliance on hardware off the table and leaves issues like down servers, personal computers, and mobile devices at the bottom of the list.
This heavy reliance on cloud-based infrastructure explains cloud service outages coming in as the fourth-scariest scenario in the survey. However, it earned a much lower overall “scariness” score. Like the hardware issues listed, we’ve seen and learned how to handle cloud service outages: while they’re scary and inconvenient, we’ve learned that they usually right themselves. Most cloud service providers are trusted global companies that have so many security and backup measures in place that it would be extremely rare for a cloud provider’s outage to cause permanent damage to a company using their services.
Similarly, while ISP and CDN outages can cause detrimental downtime, experience has taught us that the effects are rarely permanent. Just like cloud providers, ISPs and CDNs usually have extensive backups and security in place. Additionally, organizations that power mobile work can work around internet outages by allowing employees to work elsewhere and use a different network during the outage.
How Organizations Are Responding
The discrepancy in rankings between the top three scary scenarios and the rest of the scenarios presented reflects a continuation in business’ shift towards cloud-based and SaaS solutions. It also indicates a dwindling reliance on hardware and legacy equipment.
Fortunately, the survey showed that organizations are rising to meet the challenges the top threats pose. The vast majority of organizations have increased their IT budgets over the last year and plan to do so again next year: over 80% of respondents said remote work has increased their focus on security, and 75.1% said their organizations increased their IT budgets in the past year; only 6.2% said their budget decreased. 77.3% of respondents expect their budgets to increase next year.
In the past three months, organizations have spent money on:
- Cloud services (66.7%)
- Security technologies (64%)
- Collaboration tools/software/apps (58.5%)
- Remote management technologies (56.9%)
- Mobile technologies (49.8%)
These spending habits further suggest that organizations understand the importance of cloud technology as businesses move away from legacy equipment and toward a mobile, work-from-anywhere world.
Shoring Up Your Defense: Understanding the Cloud Security Risk Landscape

In the era of the cloud, cybercriminals are proving scarier than outages and hardware issues. In short, if you have a black hoodie lying around, you’ve got the makings for the scariest costume at your Halloween parties this weekend (we hear this is the hacker uniform).
While we’ve provided a few defenses to get you started, your security shouldn’t end there. Security in today’s cloud-based and remote-enabled environment needs to be holistic, robust, and reliable. But it’s impossible to build an adequate defense without first understanding what you’re up against. Recently, our CISO sat down with VMware’s Head of Cybersecurity Strategy to discuss cloud security risk in detail. Watch the full webinar to learn from the experts about today’s cloud security risk landscape and how to navigate it.



