As cloud adoption in IT continues to accelerate, vendors are introducing cloud directory offerings to the space. Some of these, however, aren’t exactly what you’d expect. This head scratching has led IT admins to wonder what a cloud directory is and how it is different from the on-prem identity provider (IdP) or traditional directory service they are accustomed to.
In truth, a cloud directory isn’t just a cloud-washed version of the on-prem directory service or a simple relational hierarchy of cloud identities; rather, it’s a new generation identity and access management (IAM) platform.
Directories Before the Cloud

Historically, the directory, or identity provider, lived on-prem and was most often delivered in the form of Microsoft Active Directory, where OpenLDAP was used as the open source alternative. With the IT network largely Windows-based and on-prem, it made a great deal of sense that a Microsoft solution helped manage user access.
In short, the on-prem identity provider would connect users to their IT resources including systems, applications, files, and even the network itself. When everything was Windows, it was easy to see why Active Directory and the domain controller were so valuable. End users would simply login to their Windows laptop or desktop, and they had access to whatever they were entitled to within the on-prem network.
Rise of the Cloud
That identity and access management model started to break down as the IT network shifted away from being on-prem and Windows-based. AWS cloud servers started becoming popular, Mac and Linux machines infiltrated the network, and Exchange was replaced for Google Workspace and Microsoft 365. Active Directory, the on-prem directory service, started to struggle.
While it would be a straightforward conclusion to move the directory service up to the cloud with everything else, that was not the case for Active Directory and other directories. The identity provider remained cemented on-prem and unable to adapt to the changing IT landscape.
Seeing this vacuum, vendors began releasing add-ons to the traditional identity provider that would help to span the gap between the ever-expanding cloud and on-prem, Windows environments. These include identity bridges, web-application single sign-on (SSO) tools, privileged access management, multi-factor authentication, governance solutions, and more. While they helped to add the functionalities missing from AD and other directories, these add-ons couldn’t capture the full IAM picture.
As all of these changes occurred, a next generation identity management platform emerged to enable IT organizations to shift to the cloud and non-Windows resources effectively and create a Domainless Enterprise.
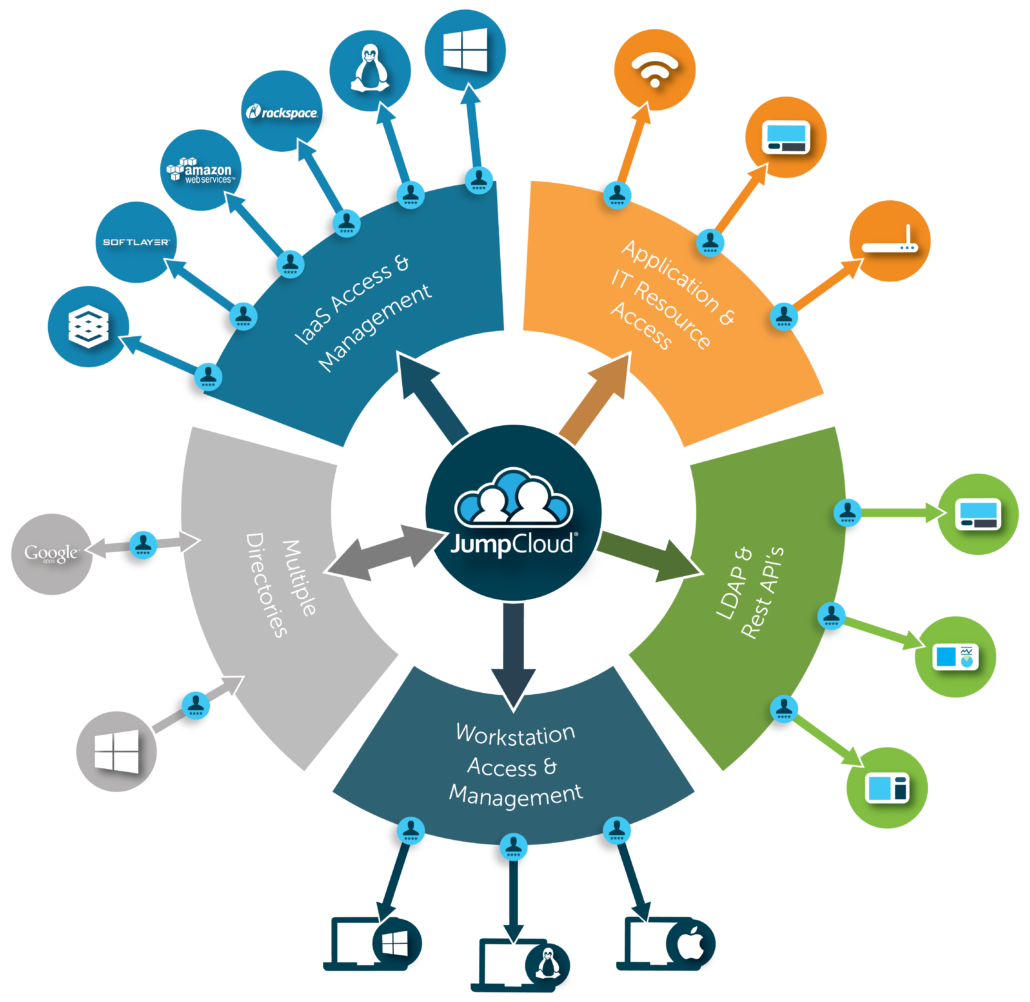
Called the cloud directory, this cloud identity provider securely managed and connected users to their systems (Windows, Mac, Linux), web and on-prem applications via LDAP and SAML, cloud and on-prem servers (e.g. AWS, GCE, Azure), physical and virtual file servers (Samba, NAS appliances, Box, G Drive, etc.), and wired and WiFi networks through RADIUS. This cloud directory is JumpCloud Directory Platform.
A Cloud Directory is:
Cloud-based directory
There is no on-premise server to run and manage. While DaaS lives in the cloud, it can be connected to the cloud or on-premise. There is no tricky networking required. If your device or application is connected to the Internet, it can authenticate against the cloud identity provider solution.
Cross-platform
A modern Directory-as-a-Service supports all major operating systems and device types. Macs are treated as first-class citizens. This safely gives employees the tools they need to be most productive.
SaaS
Organizations get all of the benefits of software-as-a-service. There is no software to install and host on-premises. Organizations can purchase only what they need and pay on a monthly basis. There’s no expensive licensing and long-term commitments.
Secure
Modern Identity-as-a-Service solutions embed security into the directory. Admins no longer need additional tools to detect and find compromises of their credentials. A modern directory starts with security and understands that in the modern era, credentials are like gold. DaaS solutions not only work to detect compromises, but they also use a number of techniques to protect credentials, including hashing and encryption.
A directory service is critical to connecting employees to their IT resources. Any directory service can alleviate some of the burden. However, in today’s cloud era, a modern directory service – delivered as-a-service – is the new standard.
JumpCloud: The Cloud Directory
With JumpCloud, the identity provider is made directly available from the cloud. This directory-as-a-service leverages the LDAP, RADIUS, and SAML protocols to link user identities to applications, both on-prem and in the cloud, as well as networks, file servers, and more, regardless of provider or location.
As a third party cloud directory, JumpCloud also provides complete endpoint management for the three major platforms (Windows, Mac, Linux). The concept of a cloud directory is encapsulated in the shift to a Domainless Enterprise where every access transaction is secured and enabled regardless of platform, provider, protocol, and location.
Learn more about JumpCloud’s cloud directory by visiting our blog or YouTube channel, or by contacting us with questions. To see the cloud directory firsthand, you can schedule a demo or try the product out yourself by signing up for a trial.




