October is Cybersecurity Awareness Month, and this year’s theme is See Yourself in Cyber, which focuses on the individual’s role in cybersecurity. While cybersecurity can feel complex and inaccessible to the average person, the reality is that everyone has a role to play in security, from executives to the IT team to end users. This month, the JumpCloud blog will focus on helping you empower everyone in your organization to do their part regarding cybersecurity. Tune in throughout the month for more cybersecurity content written specifically for IT professionals and MSPs.
Many organizations spend quite a bit of time onboarding new employees and making sure they have access to everything they need; however, the same care is often lacking when it comes to offboarding. Whether a long-time employee suddenly leaves on bad terms, a contractor is no longer being utilized for some period of time, or an employee goes on leave, improper offboarding or suspension of that user’s permissions and access poses significant risk for your organization.
Offboarding and deactivating a user’s identity can be a manual and time-consuming process, yet it is also very time-sensitive and sometimes requires IT admins to be available at a moment’s notice. Not every employee gives notice prior to leaving, and unforeseeable events can happen that force admins to scramble at the last minute to deprovision that user’s access to company resources.
This process becomes even more difficult if your organization needs to provide access to IT resources for temporary workers like contractors and interns, or has full-time employees that may need to be temporarily offboarded or have their IT resource access suspended rather than be permanently offboarded due to personal events like marriages, births, family care, overcoming an illness or injury, and more.
Most Companies Struggle With Offboarding
Improperly offboarding employees is a dangerous game to play, yet, according to TechRepublic, 48% of organizations said they are aware that former employees still have access to corporate networks. Further, 20% of organizations say they’ve experienced a data breach that’s linked to former employees.
These stats tell us that improperly offboarded employees are a predominant threat to organizations; however, the tools and resources needed to fix this issue aren’t there. The missing link here could be a lack of time, no simple way to quickly offboard or suspend user access to all IT resources, and/or lack of insight into the security risks posed by inadequate processes. It puts a spotlight on the notion that offboarding is as much a security issue as it is an operational one for IT.

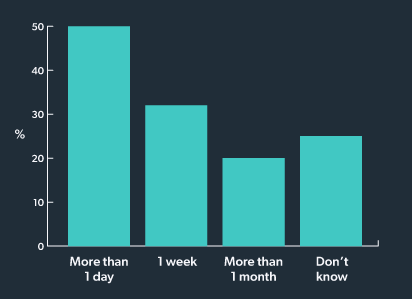
Another important finding from TechRepublic is:
Half of IT leaders said that ex-employees’ accounts remain active for longer than a day after their departure, 32% said it takes a week to deactivate an account, and 20% said it takes a month or more. Another 25% said they don’t know how long accounts remain active once the employee has left the company.
These percentages pose a significant problem for the organizations that fit into these stats. It only takes one angry ex-employee, one ex-employee that’s simply being careless with the handling of their credentials, or one employee on leave that still has active access to make damaging changes in some shared resource, even though they weren’t there for the last best practices discussion.
Case Study: Improper Offboarding and Compliance Violations
Here’s a real world example of how improper offboarding of employees and contractors can lead to considerable compliance violations, substantial fines, and the subsequent loss of public trust.
Pagosa Springs Medical Center (PSMC)
In 2018, Pagosa Springs Medical Center found itself at the epicenter of a major HIPAA violation which ended up costing them $111,400 — all because they did not properly offboard a terminated employee.
After their termination, the former PSMC employee retained remote access to PSMC’s web-based scheduling calendar, which contained patients’ electronic protected health information (ePHI). The investigation revealed that PSMC impermissibly disclosed the ePHI of 557 individuals to this former employee.
HIPAA calls out the need for a formal offboarding process under the security rule section – § 164.308(a)(3)(ii)(C): “Implement procedures for terminating access to electronic protected health information when the employment of a workforce member ends.“
Source: HHS
HIPAA is just one standard that can easily be violated due to improper offboarding — there are many others out there with similarly severe consequences for non-compliance.
A Quick Offboarding Checklist
Even at organizations where offboarding is seen as a fairly quick process, i.e. less than a couple of hours, the risk of that ex-employee or another bad actor taking advantage of existing access is still prevalent.
TechRepublic also found that 70% of IT decision makers surveyed said it can take up to an hour to deprovision all of a single former employee’s corporate application accounts. Keep in mind, this does not include revoking an employee’s access to their devices and networks.

To combat this and improve your organization’s security posture, it’s helpful to put steps in place that improve offboarding efficiency. One of these steps should include an offboarding checklist to ensure that no loose ends are left after an employee’s departure.
Your offboarding checklist should include deactivation of access to:
- All applications
- Productivity tools:
- Ex. Google Workspace and Slack
- CRM tools:
- Ex. Salesforce and Zoho

- Cloud Infrastructure
- File shares
- Devices
- Corporate Networks
- VPN
- RADIUS
- Or, if WiFi access is not centrally managed, periodically refresh the Corporate WPA2 passphrase
- And ensure return of equipment
Questions to Consider When Improving Offboarding Workflows:
- Does HR inform you in a timely manner when an employee leaves your organization?
- If an employee is terminated or leaves abruptly, are you able to deactivate their identity immediately?
- Are you able to suspend the identity for contractors who leave the company and may return?
- What about employees on medical leave who may return?
Improving Employee Offboarding
Sticking to an offboarding checklist to ensure all access is revoked is extremely important, but what’s just as important is the process in which everything is deactivated. Not only are manual offboarding processes time-consuming, but they also leave a lot of room for human error.
While working to improve and standardize your entire offboarding workflow, we also recommend that you establish routine communication with HR around onboarding and offboarding, as well as find an identity provider (IdP) to streamline the process.
Establish Routine Communication With HR
If you’re not already in continuous communication with HR regarding employees coming and going, you need to establish a better process between departments. HR should let you know when an employee is scheduled to leave or immediately notify IT when someone leaves abruptly. HR should also inform you in advance when an employee is scheduled to return from leave or their contract is renewed.
Though many project management tools exist to help alert internal stakeholders about new tasks, and some HRIS systems can even directly integrate into your core directory service to fully automate this process, this communication can be quickly achieved by creating an email alias or group with select individuals from HR and IT. Whenever someone across the organization alerts HR of a change in employment, they can CC this email alias to give IT the necessary “heads up” they need to act quickly.
Find the Right Identity Provider
When choosing an identity provider, find one that has the following capabilities:
- Allows you to automate deactivation of a user’s identity
- Once you set the date/time of deactivation, your IdP should take care of the rest
- Lets you easily and quickly revoke access to ALL resources
- Deactivating a user’s identity should revoke access to applications, devices, networks, and any other resources that user had access to
- Simplifies user activation and reactivation
- If an employee returns from leave or a contractor’s contract is renewed, you should be able to quickly and easily reactivate their identity in a just few steps
- Includes integration capabilities with common HRIS software
Fixing the communication disconnect between HR and IT and implementing the right identity provider will allow you to securely and efficiently revoke access and re-provision access as needed, through just a few clicks.
JumpCloud’s Offboarding and User Suspension Features
Using JumpCloud® as your primary IdP allows you to quickly deprovision user access to virtually all of their IT resources. Our scheduled suspension features allows you to schedule a date and time for user deactivation which revokes access to applications, devices, networks, and any other IT resource their account has permissions for.
If the user in question will be returning, you can use this capability as a temporary suspension, and the user can later be reactivated; what’s more, they’ll receive updated permissions and access to new or changed resources as determined by their associated user, device, and policy groups automatically once reactivated. If the user in question will not be returning, use this feature to schedule their deactivation and then fully remove their account when appropriate (as dictated by compliance regulations or internal policy).
The JumpCloud scheduled user suspension feature simplifies and automates the deactivation workflow for scheduled permanent offboarding, as well as temporary suspension of contractors, freelancers, and employees on leave. This feature lets you revoke access to all resources, not just corporate applications. All of this works together to improve your overall security posture and ensure that your organization remains compliant with relevant standards.
All of this coupled with the fact that JumpCloud integrates with HR software like Workday and Bamboo, as well as provides API-based integration with other tools, provides a seamless onboarding and offboarding experience for IT admins.
Try Scheduled User Suspension
This feature can be found within the JumpCloud Admin Console — find it under User Management > Users. Try it today by signing up for a trial of JumpCloud. Enjoy all of the functionality of the JumpCloud Directory Platform, including scheduled user suspension, and see if JumpCloud is the right IdP for your organization!





