We attended CrowdStrike’s Fal.Con 2022, a conference where security professionals learn to strengthen their security posture to improve their organization’s protection against evolving and more sophisticated attacks. Cybercriminals are relentlessly targeting small and mid-sized enterprises (SMEs), as well as the cloud infrastructure that enables modern IT. The concepts and topics discussed at Fal.Con are important to IT teams, as the boundary between a better security framework and IT operations dissolves.
The silos between endpoints, data protection, and user identity should no longer exist. Lack of integration has created substantial visibility gaps within the context of users and their permissions at a time when there’s a rise in novel cyberattacks. CrowdStrike has discovered that 75% of cloud breaches are due to compromised identities. A compromised identity is the entrypoint for lateral movement into your infrastructure, whether it’s hosted in the cloud or on-site. Cybercriminals have also monetized stolen identities to extract even higher ransoms from SMEs. What’s more concerning is that these criminal organizations (and state actors) have become significantly more adept at targeting cloud infrastructure and hiding their tracks.

The solution, explored in further detail below, is to implement Zero Trust security controls to make identity the new perimeter for cloud security. The rise of the remote worker increases complexity and IT professionals must adapt to the context of the end user. Consequently, a directory to manage all identities, devices, infrastructures (in combination with network and endpoint protection) is apparent, regardless of the size, industry, and/or hybrid/remote workforce models.
IT teams are often caught between security demands and pushback from business units over downtime, which creates more risk when left unresolved. Managing identities and implementing Zero Trust controls in your identity and access management (IAM) will help improve risk management. Identity management plays a central role in thwarting modern methods of attack and compromise.
Here’s JumpCloud’s perspective on the five most important themes from the conference.
1. Identity and Zero Trust
Blindspots grow as network complexity increases, such as more platforms, identities, cloud resources, and everything in between. This is addressed by putting security measures in place from the user’s side through single sign-on (SSO) and identity integration. This can be done using JumpCloud’s open directory to integrate identities from different services into one place, resolving security confusion. Then, environment wide multi-factor authentication (MFA) combined with conditional access rules for privileged access management (PAM) prompts users to prove who they are.
CrowdStrike now stresses the importance of identity integration with security systems to detect anomalous behavior. Attacks don’t always start at the beginning of the cyberattack kill chain, and may originate with lateral movement from a compromised identity. CrowdStrike gave an example of where a compromised Microsoft identity was used to escalate privileges in Active Directory via a Windows defect and common security tools to make a standard user a domain admin. This attack could have been prevented if Zero Trust security controls and monitoring were in place.
Bridging the Detection Gap
The concern in 2022 isn’t so much malware (there wasn’t any even used in Crowdstrike’s example above); it’s poorly controlled user identities and entitlements. Integrating a directory or IdP with a security platform bridges the gap for devices that don’t have sensors installed. Users access things from unmanaged devices. As a result, 25% of cyberattacks originate from those unsecured endpoints according to CrowdStrike. Strong identity management is vital to bridge that gap to protect your IT systems. That’s especially true in the cloud where attackers are lurking.
Misconfigurations in cloud setups and privilege escalations where entitlements are too permissive can create security breaches. Cloud providers are responsible for ensuring their security infrastructure is strong and vulnerabilities are mitigated quickly.
2. Evolving Threats in the Cloud
The shared responsibility model that cloud service providers (CSPs) have established places the security onus on the customer. That’s an important consideration as more organizations migrate their sensitive data and IT resources to the cloud. However, it often happens without SMEs having an adequate understanding of their responsibilities for security and data handling.
The attack surface expands as infrastructure grows, and that makes the cloud an attractive target. SMEs need faster defenders, because there’s far less time between breakout to lateral spread. CrowdStrike found that it has decreased from an average of 9 to 1.5 hours.
71% of attacks are malware free once an adversary is in your environment, cloud, or on premises. They’ve also re-tuned command and control methods with a more sophisticated approach that mimics traffic from trusted service providers. State actors have begun to specialize in this sophisticated approach to cybercrime and have become “access brokers” that participate in illicit markets for compromised IDs.
Fortunately, malware-free intrusions can be halted with identity protection. Zero Trust solutions for identity and IAM, coupled with identity protection, can prevent attackers from penetrating an organization’s IT infrastructure by picking up on analogies in behavior, location, and/or device usage. Even insurance companies have begun to realize that a Zero Trust security strategy is a baseline for effective IT operations.
3. Cyber Insurance as a Change Agent
It’s not uncommon for SMEs to apply for cyber insurance policies to transfer IT risks. The days of permissive underwriters that send checklists with little to no follow through are nearing an end. One Fal.Con session was hosted by a large cyber insurance broker and risk management firm. Their message was blunt: The pandemic of ransomware and email compromise is ebbing; more sophisticated attacks that require a baseline of security control with a heavy emphasis on identity management are emerging. Underwriting is beginning to consider how potential customers handle evolving adversarial tactics and techniques and if they’ve been breached. Failure to manage cyber risk can and will impact future insurability.
As expenses rise, it’s unlikely that an SME can absorb cyber risks. There’s also new litigation in place that could lead to a legal storm following a technology/security incident. This is due to intensifying regulations and rising systemic risks as criminal organizations become more effective.
The following security controls are what the insurance industry is beginning to rally around:
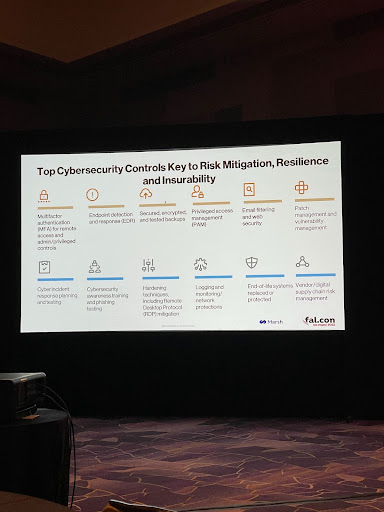
A Zero Trust strategy is being prescribed, along with a heavy focus on IAM, endpoint management, networks, data, and workloads. It’s based upon NIST SP 800-207 Zero Trust framework and new federal guidance. Simply stated, organizations should assume a state of compromise where two-way verification is the default, and make identity their new perimeter.
The insurance industry panelist stated that security doesn’t have to be a burden. Rather, “you can drive the car faster” with good security controls, quality IT practices and infrastructure, Zero Trust preparation, and cyber insurance (for risk transference). That combination can have a compounding effect for risk management. Managing users’ identities and machines are foundational building blocks to Zero Trust security strategies.
However, the challenges of change management in your fleet aren’t superficial. Business units may be wary of change, but a lack of security controls, visibility, and addressing vulnerabilities in a timely fashion creates a risk gap that only grows if not addressed.
4. Closing the Gap Between IT and Security
It’s understandable that IT teams may face pushback as they implement security controls and/or push out patches and configuration changes. IT changes can impact business productivity, and the burden of change management falls on IT. There have been over 1,000 patches released from Microsoft to date this year alone. Patch Tuesday has now become “Zero Day Tuesday.”
CrowdStrike advocates extended detection and response (XDR) as a holistic approach to cyberattacks. The goal is to achieve full visibility and security controls across the whole environment. While ideal, they acknowledge it’s difficult to make XDR a reality. This is due to the lack of available tools to achieve a holistic approach to security where change management, visibility, and the impact of change on businesses leave very real gaps.
The solution is to obtain the full spectrum of information about every IT asset, as well as the applications and identities that access them. Activity and data should have context. SMEs may have other constraints such as limited budgets and internal resources that get in the way of adopting a holistic approach.
It’s important to do the basics well. That includes managing endpoints cross-OS with unified device management, along with patching, remediations, and visibility into your environment. That’s why JumpCloud is included in the CrowdStrike Store. JumpCloud provides the option for cross-OS patching in addition to reporting on important activities, such as SSO authentications.
Patch Gaps
Another Fal.Con session emphasized the time that passed between the disclosure of the Follina and Windows Support Diagnostic Tool vulnerabilities in Windows and when a working patch was delivered to customers. JumpCloud found that many organizations didn’t apply any remediation while waiting for the patch. In practical terms, this delayed all of the patching activities that organizations have in place for change management, and days can effectively become weeks.
It’s understandable, because a mitigation can impact IT operations, but might not have much of an effect. Mitigations should be considered as an option to reduce risks when Zero Day attacks occur, especially when there’s been active exploitation, and risk should be weighed against potential harm. Mitigations offer faster protection and limit uncertainty during the patch gap. JumpCloud users can apply vendor-recommended mitigations across their fleets by using commands such as the Windows PowerShell module.
JumpCloud’s open directory platform unifies many IT functions.
5. IT Consolidation
A session at Fal.Con that focused on the economic rationale for Zero Trust concluded that it’s essential for risk mitigation and is among the top concerns of CIOs. The other main concern was IT consolidation. Organizations are consolidating their IT and security tools with fewer vendors. CIOs are attempting to solve complex and non-integrated resources to lower operational costs and improve their overall security postures. There are hidden costs to IT sprawl, such as increased training, higher management overhead, and overlapping features.
Consolidation could be made possible through partnerships and integrations such as JumpCloud and CrowdStrike, which are better together. This integration was recently recognized with JumpCloud being named CrowdStrike’s 2022 Emerging Partner of the Year. JumpCloud’s open directory platform with device management can become a part of your consolidation strategy while delivering Zero Trust access control to protect users’ identities in the cloud. JumpCloud offers a standalone LDAP directory, but can import identities from Active Directory, Azure Active Directory, Google Workspace, and Okta. Identities can then be orchestrated with IAM, including:
- Remote assistance
- SSO with environment-wide push and TOTP MFA
- Cloud RADIUS
- Mobile device management (MDM)
- Patching
- Decentralized password management for teams
- Conditional access policies
Try JumpCloud
You may sign up to JumpCloud through the CrowdStrike Store or directly through our website for a free 30-day trial that’s not limited by time or functionally in any way.
Need a Helping Hand?
Reach out to [email protected] for assistance in determining which Professional Service option might be right for you.




